 May
20
2021
May
20
2021
Teams is the new Windows
When you say collaborate, you say Microsoft Teams. I think there is hardly an office around where Teams is not an intricate part of the daily work and communication process, especially organizations already using Microsoft 365 services. They really can’t deny that added value of Teams. And if you still think Teams is just for videocalls and online meetings, you are in for a surprise: it is the collaboration platform of the 21st century.
All in one
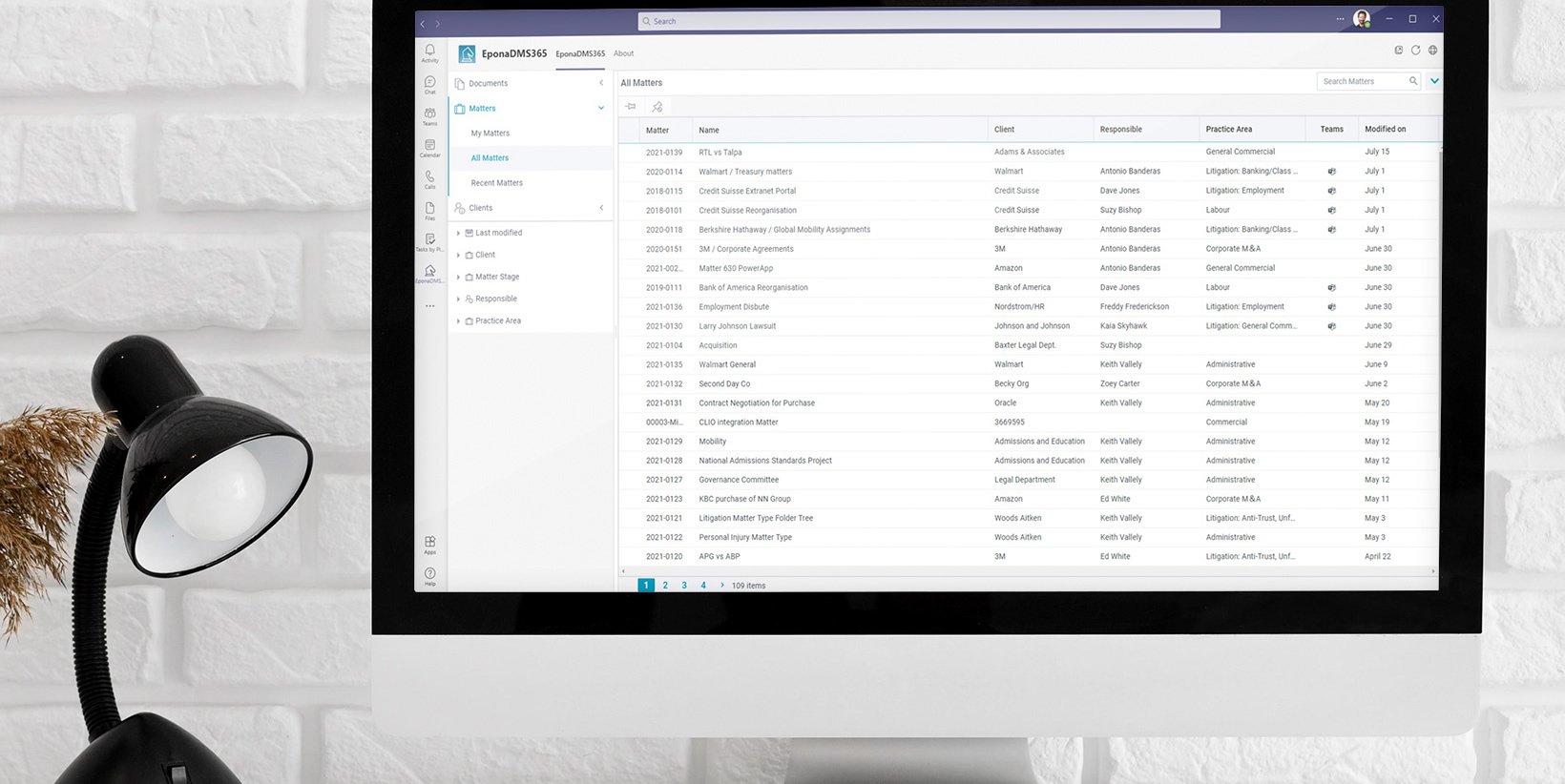
When I say, “Teams is the new Windows,” what I mean is that it changes the way we use applications. We used to install an application on Windows or used a web-app in a web browser. Now, data and application functionalities are becoming available directly inside of Teams. This means that in the future, to look up a matter or a file, you no longer must navigate to a separate application, but stay in Teams to complete your task. Teams has its own app store that holds many handy integrations and applications, and the number of available apps keeps expanding!
The great thing I like about Teams, is that it works almost everywhere. On the web, on a Mac, Windows PC, a smartphone: Teams gives you an almost universal viewport to the world, no matter which application or silo holds your data.
Security risks
Accessing all that data through one single portal sounds like creating extra security risks. Compromise the one portal, and the whole store is up for grabs, right? The contrary is true. If you use the Microsoft Security and Compliance framework, together with Teams, the risk of an incident taking place only gets smaller. This is because Teams is such an intricate part of the Microsoft 365 ecosystem. Things like sensitivity labels can now be applied to your data, so you can prevent information from being (accidentally) visible to other parties.
Sensitivity labels give employees confidence
Using sensitivity labels, you can classify any document in Microsoft 365 (being SharePoint, Teams or OneDrive, it’s all the same to Microsoft) to give it a specific security state. You could classify an e-mail or a document as “for internal use only”, which prevents it from being opened by anyone not having a Microsoft 365 account associated with your organization. And it gets better!
Safely share your screen
We have all been there: you’re in a meeting and someone needs to share their screen. Upon sharing the screen, their Outlook was still visible and the whole meeting gets a good look in their agenda or in their e-mail correspondence. Sensitivity labels are quite clever: if an e-email was labeled for internal use only, the shared screen blurs or blocks the view of that specific e-mail. This prevents other attendants from outside your organization from seeing it.
The next step is what is called information barriers. This blocks specific communication tools or functions on the computer while you are working on a classified document. Thus, preventing the accidental sharing of the file. This provides an extra line of defense in the prevention of human error: the greatest origin of most security breaches.
The sensitivity labels and the related protection tools give your employees the confidence to work safely on delicate matters. That is quite the improvement compared to having to constantly frighten them, and by doing so slowing them down and limiting their productivity and creativity.
Classifying matters
These security options become available by classifying your matters and files. Since this is usually done by jurisdiction or case manager, you can quickly classify and secure great volumes of information. A recent shift we saw when it comes to information accessibility, is a shift from “open, unless”, to “closed, unless” security.
In the past, old matters and files would be left accessible to the entire organization, so everyone could learn and take from old cases. But since (luckily) security and privacy have become an even bigger priority to most organizations, this shift to “closed, unless” is now finally taking place. Things like conditional access, where not only the users rights, but also things like the device they’re using or their location are used to verify access, are becoming a more common practice each day.Sharing of knowledge can now be achieved through Knowledge Management Systems, where curated and checked content (cleaning out i.e., old client information) can now be safely shared with the entire organization by a specialized knowledge management team.
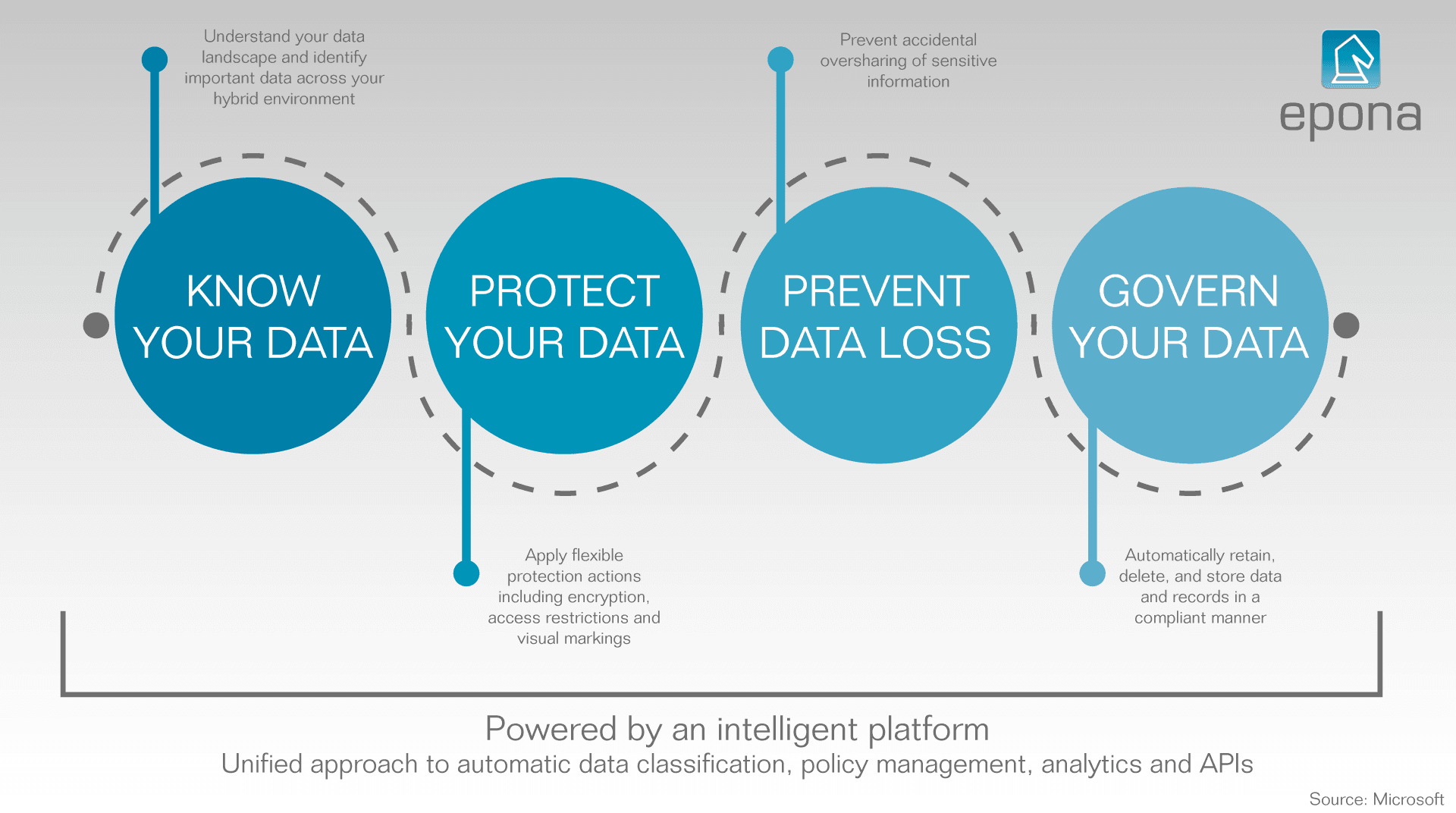
Know, protect, prevent, control
For managing sensitive information, Microsoft developed a special tool set known as the Security and Compliance Center. This represents four central themes: Information Protection and Governance (IPG), Insider Risk Management (IRM), Compliance Management (CM) and Discovery and Response (DR).
- IPG allows organizations to classify data, and apply the correct data protection measures based on the classification.
- IRM lowers employee risks, for instance by using the sensitivity labels to prevent information from showing up while sharing a screen.
- CM checks, also based on the sensitivity labels, whether the information is protected in a way that is compliant with regulations regarding its safety.
- And lastly DR, which actively looks for potential risks in your current setup, to improve information protection.
Microsoft 365 for law firms and corporate legal

Most organizations are not fully benefitting from their often already heavy investment in Microsoft 365. Our whitepaper “Microsoft 365 for law firms and corportate legal” outlines the next steps they can take, to start using Microsoft 365 as their next and final unified legal enterprise solution. Download it for free on our website for more insights in what you can accomplish with universal platform.
By: Marcel Lang – Director Epona USA