
Security researchers discovered a new ransomware strain they named Mimic that leverages the APIs of the 'Everything' file search tool for Windows to look for files targeted for encryption.
Discovered in June 2022 by researchers at cybersecurity company Trend Micro, the malware appears to target mainly English and Russian-speaking users.
Some of the code in Mimic shares similarities with Conti ransomware, the source of which was leaked in March 2022 by a Ukrainian researcher.
Mimic attacks
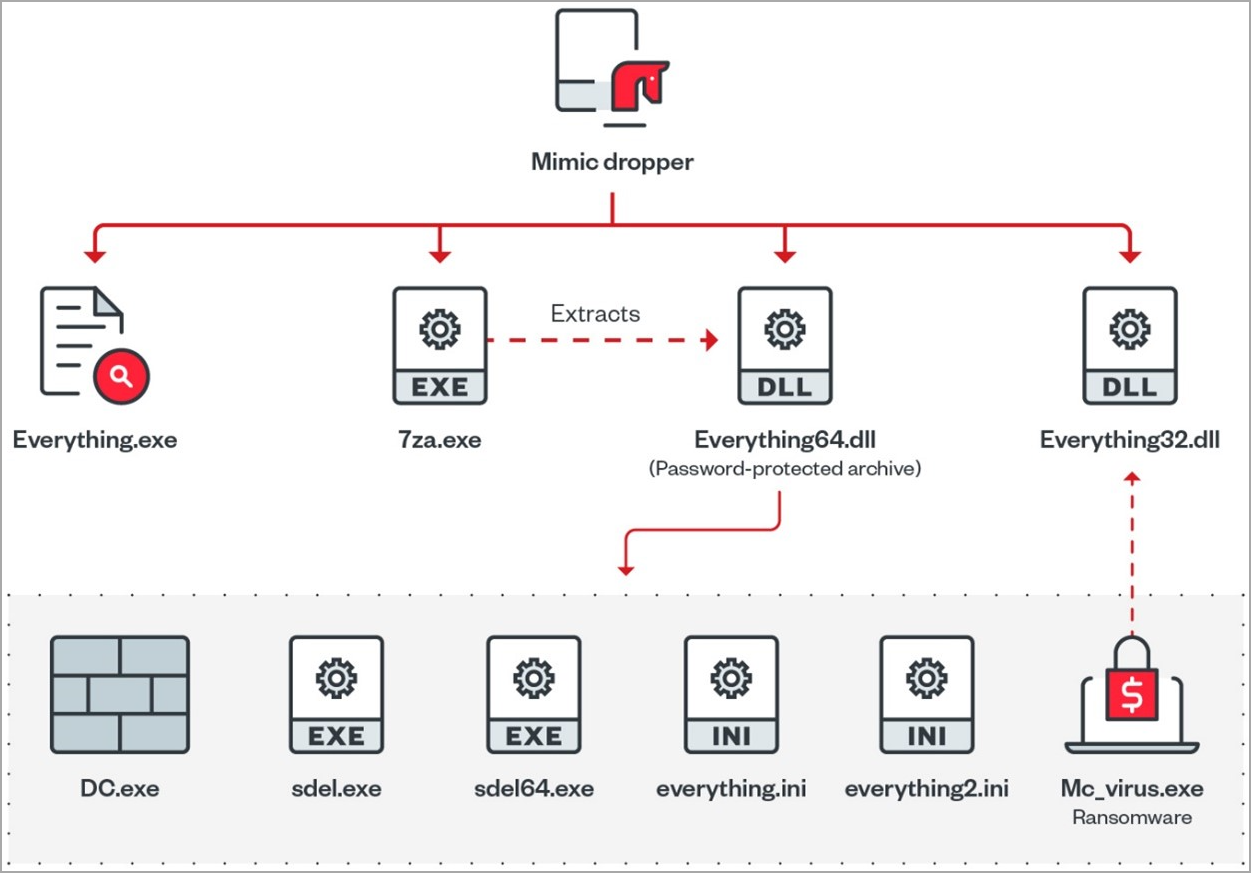
Mimic ransomware attacks begin with the victim receiving an executable, presumably via email, which extracts four files on the target system, including the main payload, ancillary files, and tools to disable Windows Defender.
Mimic is a versatile ransomware strain that supports command line arguments to narrow file targeting, while it can also make use of multiple processor threads to speed up the data encryption process.
The new ransomware family features several capabilities seen in modern strains, such as:
- Collecting system information
- Creating persistence via the RUN key
- Bypassing User Account Control (UAC)
- Disabling Windows Defender
- Disabling Windows telemetry
- Activating anti-shutdown measures
- Activating anti-kill measures
- Unmounting Virtual Drives
- Terminating processes and services
- Disabling sleep mode and shutdown of the system
- Removing indicators
- Inhibiting System Recovery
Killing processes and services aim to disable protection measures and free up important data like database files, making them available for encryption.
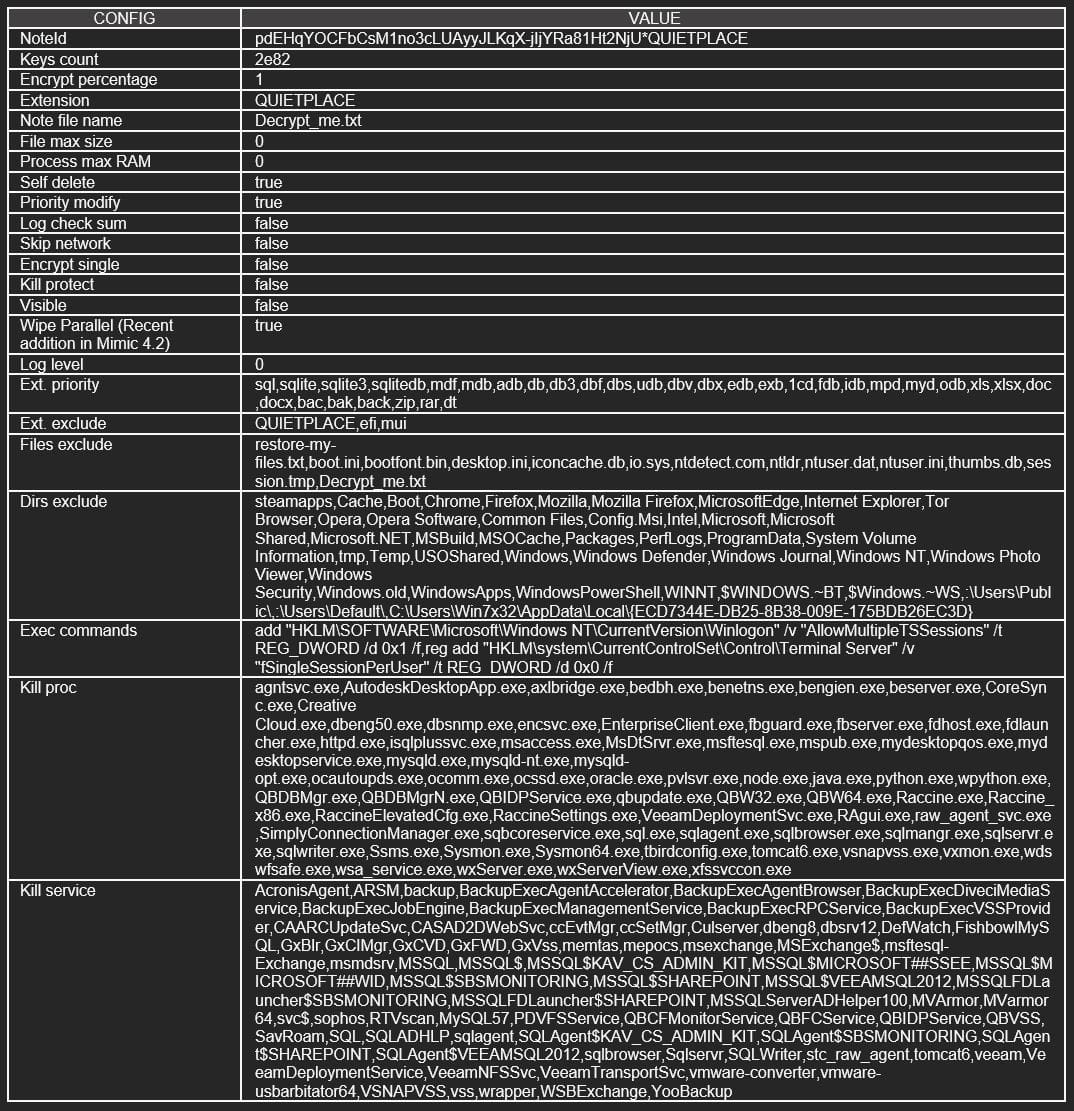
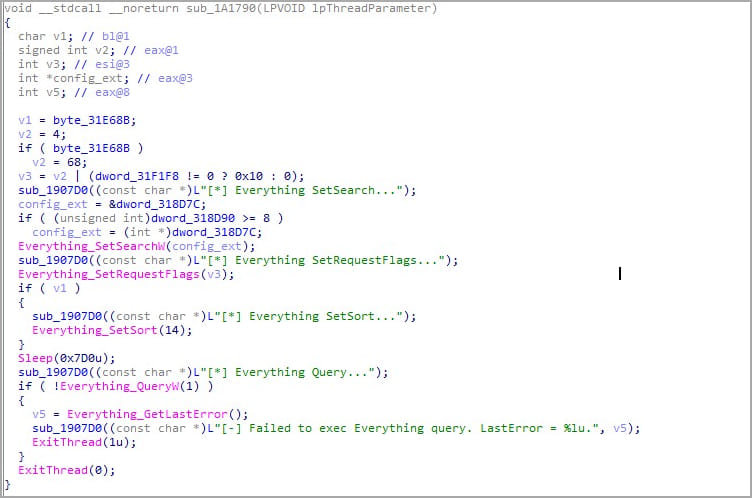
Abusing Everything
"Everything" is the name of a popular filename search engine for Windows developed by Voidtools. The utility is light and quick, uses minimal system resources, and has support for real-time updates.
Mimic ransomware uses Everything’s search capabilities in the form of the ‘Everything32.dll’ dropped during the infection stage to query for specific file names and extensions oin the compromised system.
Everything helps Mimic locate files that are valid for encryption while avoiding system files that would render the system unbootable if locked.
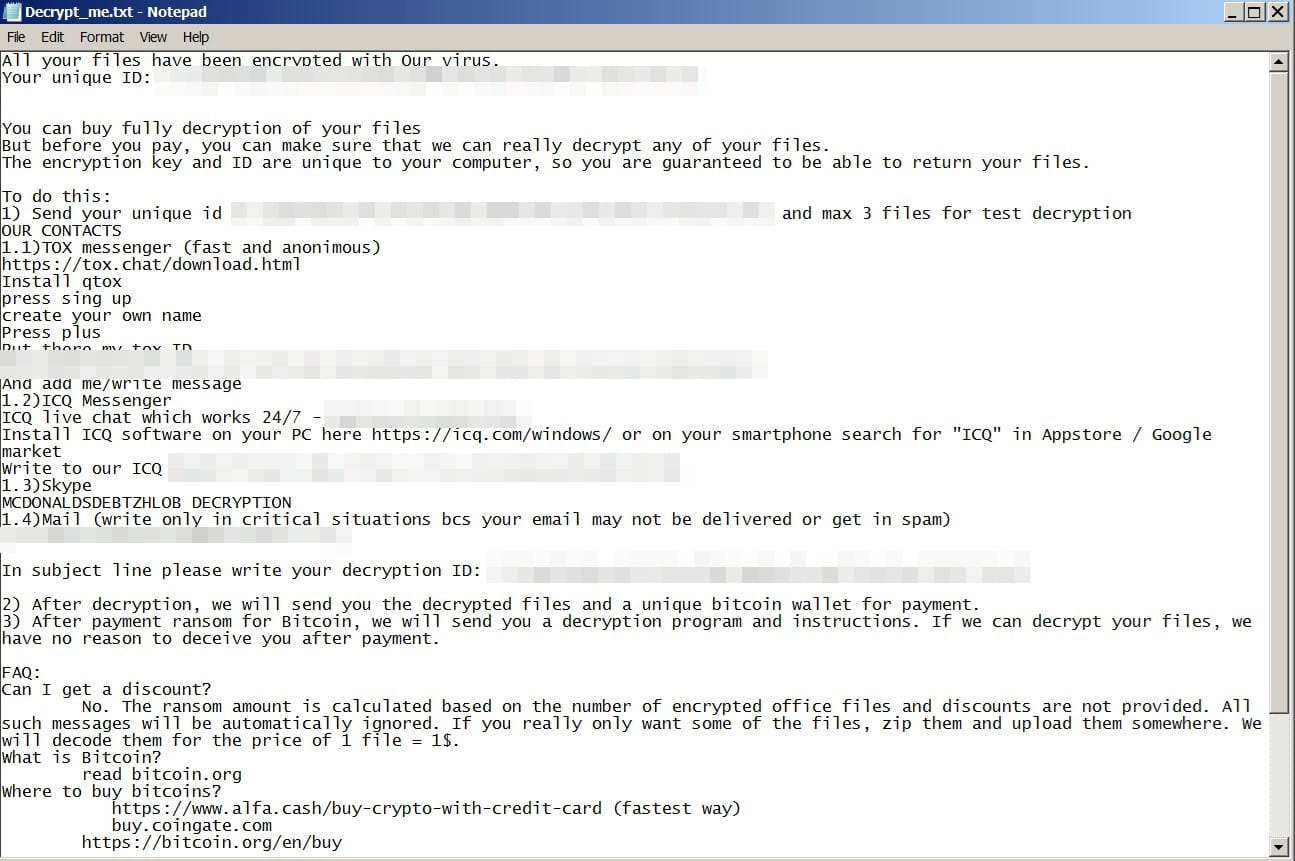
Files encrypted by Mimic get the “.QUIETPLACE” extension. A ransom note is also dropped, informing of the attacker's demands and how the data can be recovered after by paying a ransom in Bitcoin.
Mimic is a new strain with unproven activity as of yet, but using of the Conti builder and the Everything API proves its authors are competent software developers who have a clear understanding of how they can achieve their goals.


Comments
Amigo-A - 1 year ago
Bravo, TrendMicro! Six months later, after increased attacks, at least one antivirus company began to report this.
https://id-ransomware.blogspot.com/2022/08/n3ww4v3-ransomware.html
https://www.bleepingcomputer.com/forums/t/775305/
Six months after my publication in the Digest, after numerous samples uploaded to VirusTotal, after numerous forum posts, at last someone else has done the analytical work and reported it.
Now all the laurels of the victor go to YOU! Bravo, TrendMicro!