
The US Department of Justice today said that Moises Luis Zagala Gonzalez (Zagala), a 55-year-old cardiologist with French and Venezuelan citizenship residing in Ciudad Bolivar, Venezuela, created and rented Jigsaw and Thanos ransomware to cybercriminals.
Zagala (aka Nosophoros, Aesculapius, and Nebuchadnezzar) also offered support to cybercriminals who bought the malware and shared profits earned after ransoming victims worldwide.
"As alleged, the multi-tasking doctor treated patients, created and named his cyber tool after death, profited from a global ransomware ecosystem in which he sold the tools for conducting ransomware attacks, trained the attackers about how to extort victims, and then boasted about successful attacks, including by malicious actors associated with the government of Iran," said US Attorney Breon Peace.
"We allege Zagala not only created and sold ransomware products to hackers, but also trained them in their use," Assistant Director-in-Charge Driscoll added.
Jigsaw ransomware includes a "Doomsday" counter that will delete a certain amount of files from the victims' drives every hour until the ransom is paid, with an increasing number of files after each reset.
Jigsaw hasn't been active since the fall of 2021, and, even then, the activity was really low. A Jigsaw ransomware decryptor is available from Emsisoft.
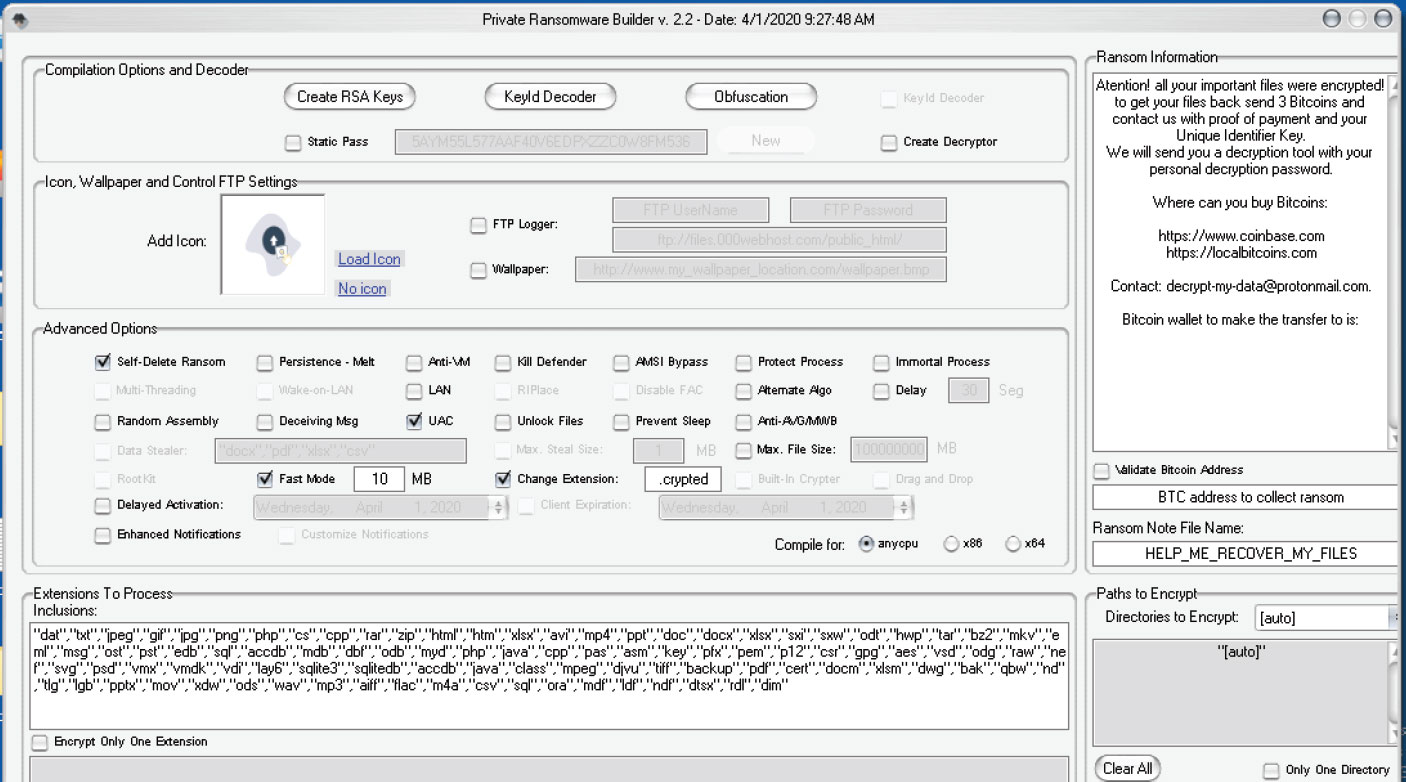
Thanos ransomware is a Ransomware-as-a-Service (RaaS) operation advertised on Russian-speaking hacker forums. The malware allows affiliates to customize their own ransomware using a builder offered by the developer.
While Zagala ran an affiliate program where cybercriminals would share their ransomware profits, he also licensed the Thanos malware using a licensing server he hosted in Charlotte, North Carolina.
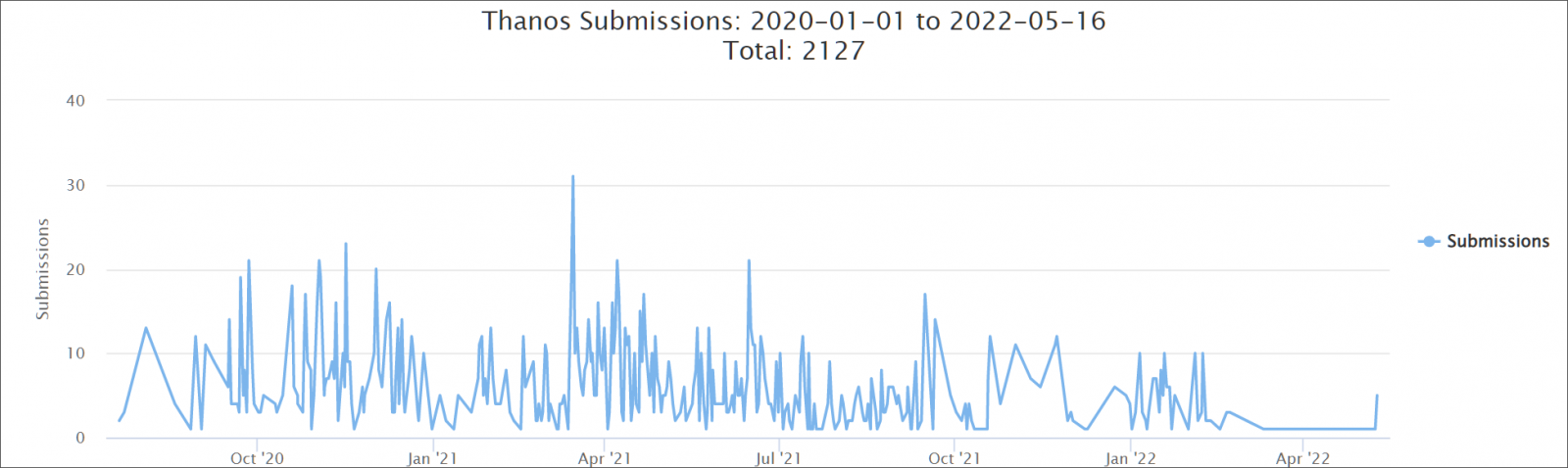
This ransomware strain stopped showing up in ID-Ransomware submissions in February 2022, and the ransomware builder was leaked on VirusTotal in June 2021.
Some Thanos ransomware samples have previously been tagged as Prometheus, Haron, or Hakbit ransomware due to different encryption extensions used by affiliates. However, Recorded Future's Insikt Group discovered that they're the same malware.
"Based on code similarity, string reuse, and core functionality, Insikt Group assesses with high confidence that ransomware samples tracked as Hakbit are built using the Thanos ransomware builder developed by Nosophoros," Insikt Group said.
According to today's DOJ press release, Zagala allegedly publicly discussed how his "clients" used his tools in ransomware attacks, "including by linking to a news story about an Iranian state-sponsored hacking group's use of Thanos to attack Israeli companies." (likely this report from ClearSky on MuddyWater's Operation Quicksand).
In May 2022, law enforcement agents linked Zagala to the Thanos ransomware operation after interviewing one of his relatives who collected some of Zagala's illicit proceeds from the ransomware operation using a PayPal account.
This individual also showed them contact information stored in his phone that the defendant used to register some of the Thanos ransomware malicious infrastructure.
If convicted, Zagala faces up to five years in prison for attempted computer intrusion and five years of imprisonment for conspiracy to commit computer intrusions.


Comments
buddy215 - 1 year ago
I don't see that the doctor is in custody. Venezuela is an ally of Russia. Extradition to USA or prosecuting him in Venezuela isn't in the numerous news sites that I have checked.
TsVk! - 1 year ago
Being an ally of Russia is irrelevant. US has implemented severe sanctions against Venezuela since 2015 and there's no way that they would give them anything.
Saigua - 1 year ago
0h great, now 55 year old cardiologist Barbie is going to be all 'CDRH surgery and 2 sided compliance is hard, let's resell malware on the darkweb.'