
A report analyzing data from the start of the year concludes that distributed denial-of-service (DDoS) attacks on Russian companies have increased 2.5 times compared to the same period last year.
A DDoS attack is when an attacker floods a service or network bandwidth with more requests than it can handle, causing the service to suffer an outage.
Threat actors are increasingly deploying huge swarms of DDoS-backing devices (botnets) to launch crippling attacks against targets on a wide range of industries and sectors.
DDoS attacks are commonly used to extort victims with ransom demands or as a distraction for IT teams while hackers attempt to steal precious data from compromised systems.
Another reason for launching these attacks against an organization is to disrupt their business, degrade the quality of their services, and lead their clients to competitor platforms.
Russians under fire
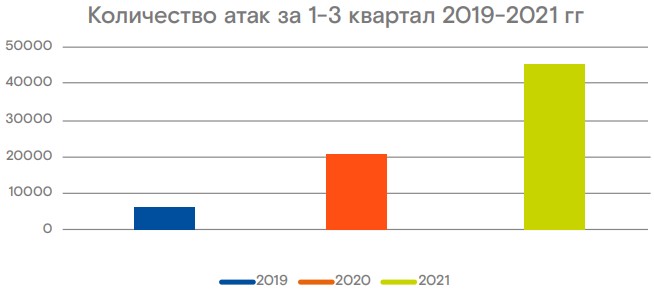
In a report from Rostelecom, the largest telecommunications provider in Russia, September 2021 was recorded as the worst period for DDoS attacks again Russia in recent history.
During that time, threat actors launched 90% of all 2021 DDoS attacks analyzed in the report, a notable surge that also manifested in other regions.
Last month, we reported on VoIP service providers troubled by DDoS disruptions, the emergence of a massive DDoS botnet called Mēris, and Yandex battling the largest DDoS attack in its history.
Source: Rostelecom
In terms of targeting trends, DDoS actors appear to be moving away from the gaming industry, which was the focus in 2020 due to COVID-19 lockdowns and stay-at-home orders, and are now targeting online trading, financial, and public sector entities.
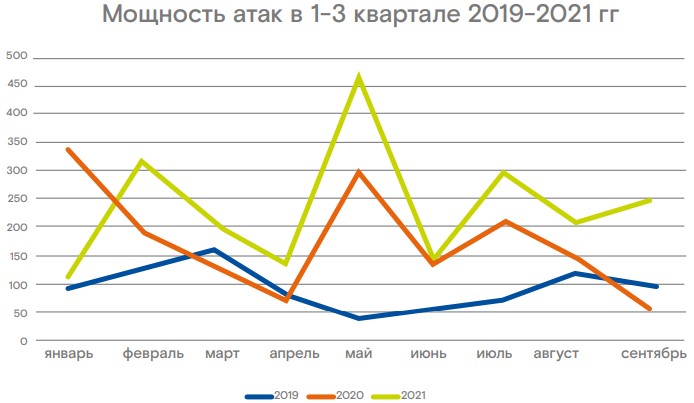
Compared to 2020, the attacks have grown 26% more powerful, last 1.5 days longer (from 3 to 4.5), and rely upon much larger botnets that count hundreds of thousands of devices.
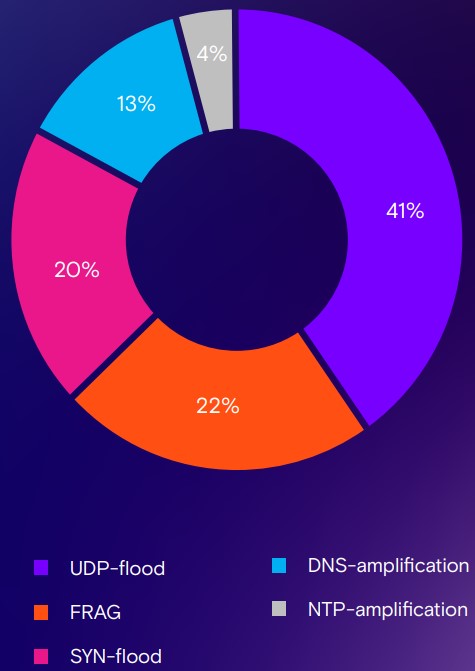
As for the types of DDoS attacks, the main methods remain SYN flooding, UDP flooding, and fragmented packet attacks (FRAG).
Source: Rostelecom
While there hasn’t been a technical development this year that would break through all mitigations, DDoS actors appear to make up for this by scaling up.
As Rostelecom explains, the most commonly recruited devices in the analyzed 2021 DDoS swarms is networking equipment from MikroTik.
In the process of its investigation, the telco managed to identify and “free” 45,000 of these devices, but a lot more remains under the control of DDoS botnet operators.
Source: Rostelecom
To reduce the risk and impact of DDoS attacks, Rostelecom suggests detaching web apps from the rest of your firm’s resources either by placing them in different data centers or onto separate sites.
Moreover, they suggest adding a Web Application Firewall (WAF) as an extra layer in your existing anti-DDoS solution, which should also help stop app data theft attempts.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now