
Ransomware took the media spotlight this week after a ransomware gang known as DarkSide targeted critical infrastructure in the USA.
The DarkSide gang dominated the ransomware news cycle after they attacked Colonial Pipeline, the largest US fuel pipeline. Due to this attack, the pipeline was shut down, and President Biden issued a state of emergency.
Colonial restored the operation of the pipeline on Thursday after news broke that Colonial paid a $5 million ransom. This was a profitable week for DarkSide as chemical distributor Brenntag also paid a $4.4 million ransom.
After DarkSide's public-facing servers and cryptocurrency wallets were reportedly seized by law enforcement, the ransomware gang announced that they were closing their operation "due to the pressure from the US."
Other news this week includes one of the most popular Russian-speaking hacking forums banning topics promoting ransomware and details about a new ransomware operation known as Lorenz.
Finally, the Conti ransomware hit Ireland's Health Service Executive (HSE), which has disrupted the Ireland health care system.
Contributors and those who provided new ransomware information and stories this week include: @serghei, @Seifreed, @VK_Intel, @BleepinComputer, @DanielGallagher, @fwosar, @FourOctets, @struppigel, @demonslay335, @malwrhunterteam, @jorntvdw, @PolarToffee, @LawrenceAbrams, @malwareforme, @Ionut_Ilascu, @darktracer_int, @Amigo_A_, @ValeryMarchive, @fbgwls245, @y_advintel, @ddd1ms, @campuscodi, @chum1ng0, @PogoWasRight, @MikaelThalen, and @FireEye.
May 8th 2021
Ransomware gangs have leaked the stolen data of 2,100 companies so far
Since 2019, ransomware gangs have leaked the stolen data for 2,103 companies on dark web data leaks sites.
Largest U.S. pipeline shuts down operations after ransomware attack
Colonial Pipeline, the largest fuel pipeline in the United States, has shut down operations after suffering what is reported to be a ransomware attack.
May 9th 2021
New STOP ransomware variant
Amigo-A found a new STOP ransomware variant that appends the .pcqq extension.
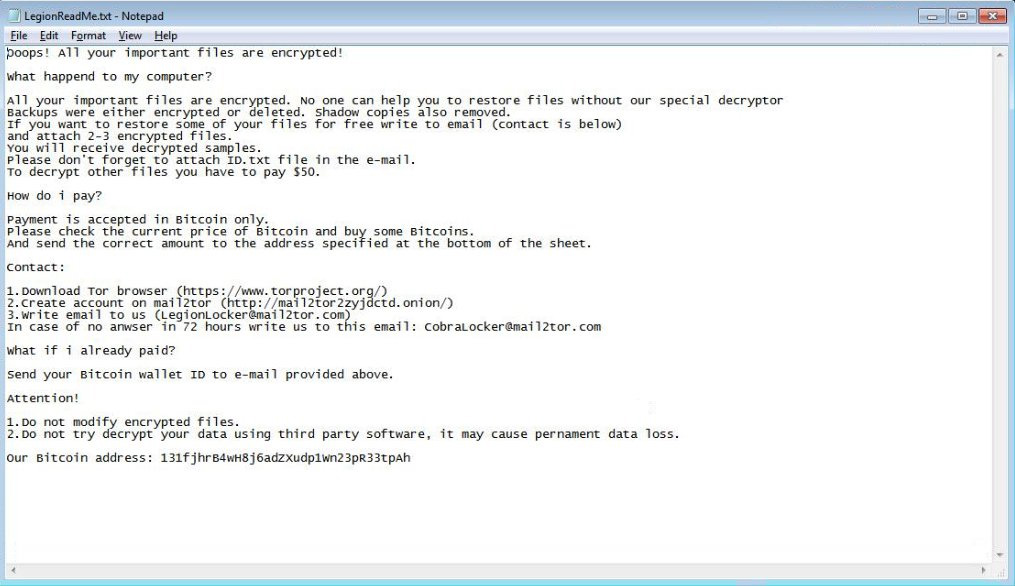
New LegionLocker version
dnwls0719 found a new version of LegionLocker 3.0 that appends the .LGNLCKD extension and drops a ransom note named LegionReadMe.txt.
May 10th 2021
US declares state of emergency after ransomware hits largest pipeline
After a ransomware attack on Colonial Pipeline forced the company to shut down 5,500 miles of fuel pipeline, the Federal Motor Carrier Safety Administration (FMCSA) issued a regional emergency declaration affecting 17 states and the District of Columbia.
DarkSide ransomware will now vet targets after pipeline cyberattack
The DarkSide ransomware gang posted a new "press release" today stating that they are apolitical and will vet all targets before they are attacked.
US and Australia warn of escalating Avaddon ransomware attacks
The Federal Bureau of Investigation (FBI) and the Australian Cyber Security Centre (ACSC) are warning of an ongoing Avaddon ransomware campaign targeting organizations from an extensive array of sectors in the US and worldwide.
City of Tulsa's online services disrupted in ransomware incident
The City of Tulsa, Oklahoma, has suffered a ransomware attack that forced the City to shut down its systems to prevent the further spread of the malware.
May 11th 2021
Ransomware gang leaks data from Metropolitan Police Department
Babuk Locker ransomware operators have leaked personal files belonging to police officers from the Metropolitan Police Department (also known as MPD or DC Police) after negotiations went stale.
Shining a Light on DARKSIDE Ransomware Operations
Since initially surfacing in August 2020, the creators of DARKSIDE ransomware and their affiliates have launched a global crime spree affecting organizations in more than 15 countries and multiple industry verticals. Like many of their peers, these actors conduct multifaceted extortion where data is both exfiltrated and encrypted in place, allowing them to demand payment for unlocking and the non-release of stolen data to exert more pressure on victims.
May 12th 2021
Darkside: an increasingly used ransomware ... with a high success rate
Darkside ransomware recently came into the spotlight with the attack on Colonial Pipeline , the operator of a critical oil pipeline across the Atlantic. But he actually started his career sometime last summer, rather quietly. According to our observations, its operators devote a new page to each victim, specifying the date when the encryption load was triggered. The web pages are numbered, which gives an idea of the acceleration in the pace of attacks conducted with Darkside in recent months.
Biden issues executive order to increase U.S. cybersecurity defenses
President Biden signed an executive order Wednesday to modernize the country's defenses against cyberattacks and give more timely access to information necessary for law enforcement to conduct investigations.
May 13th 2021
Colonial Pipeline restores operations, $5 million ransom demanded
Colonial Pipeline has recovered quickly from the ransomware attack suffered less than a week ago and expects all its infrastructure to be fully operational today.
Meet Lorenz — A new ransomware gang targeting the enterprise
A new ransomware operation known as Lorenz targets organizations worldwide with customized attacks demanding hundreds of thousands of dollars in ransoms.
Insurance giant CNA fully restores systems after ransomware attack
Leading US-based insurance company CNA Financial has fully restored systems following a Phoenix CryptoLocker ransomware attack that disrupted its online services and business operations during late March.
Chemical distributor pays $4.4 million to DarkSide ransomware
Chemical distribution company Brenntag paid a $4.4 million ransom in Bitcoin to the DarkSide ransomware gang to receive a decryptor for encrypted files and prevent the threat actors from publicly leaking stolen data.
Popular Russian hacking forum XSS bans all ransomware topics
One of the most popular Russian-speaking hacker forums, XSS, has banned all topics promoting ransomware to prevent unwanted attention.
May 14th 2021
Irish healthcare shuts down IT systems after Conti ransomware attack
Ireland's Health Service Executive (HSE), the country's publicly funded healthcare system, has shut down all IT systems after its network was breached in a ransomware attack.
DarkSide ransomware servers reportedly seized, operation shuts down
The DarkSide ransomware operation has allegedly shut down after the threat actors lost access to servers and their cryptocurrency was transferred to an unknown wallet.
In a message to affiliate, the DarkSide gang announced they were shutting down their RaaS, and would provide decryptors for unpaid victims to affiliates.
QNAP warns of eCh0raix ransomware attacks, Roon Server zero-day
QNAP warns customers of an actively exploited Roon Server zero-day bug and eCh0raix ransomware attacks targeting their Network Attached Storage (NAS) devices.
Apex America hit by Sodinokibi ransomware
That’s how they describes themselves. The threat actors known as REvil (Sodinokibi) describe them as targets who have so far refused to pay ransom demands.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now