
SAP's security updates for this month address multiple critical vulnerabilities. The most serious of them, rated with the highest severity score, affects the company's Business Client product.
Two other products from the company received patches for critical severity flaws that give unauthorized users access to configuration objects and allow remote code execution.
Critical risk score
On Tuesday, the SAP Product Security Team shared information about vulnerabilities discovered and fixed in company products. In total, there are 19 security notes, five of them being updates to previous bugs.
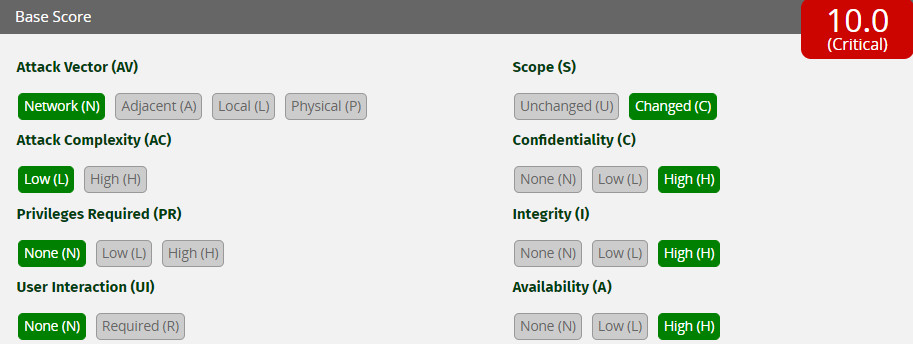
One of these updates refers to a vulnerability that impacts SAP Business Client, a user interface that acts as an entry point to various SAP business applications.
The security risk resides not in the product itself but in the browser control (Chromium) that comes with it. There are no details about the issue, except that it has been rated with a the maximum severity score, 10 out of 10.
NIST still deliberating
SAP also delivered an update that fixes a remote code execution bug in SAP Commerce used to organize product information for distribution across multiple communication channels.
The issue is identified as CVE-2021-27602 and affects SAP Commerce 1808, 1811, 1905, 2005, and 2011. SAP evaluates it as critical too, giving a severity score of 9.8 out of 10.
However, the National Institute of Standards and Technology (NIST) has yet to analyze it and provide a severity score, which may be lower.
An attacker authorized into the Backoffice Product Content Management application of SAP Commerce can exploit it to achieve remote code execution on the system by injecting malicious code in the source rules.
Another update that SAP views as critical is for the Migration Service component in the NetWeaver software stack - versions 7.10, 7.11, 7.30, 7.31, 7.40, 7.50 - that enables organizations to integrate data and business processes from multiple sources.
The vulnerability is tracked as CVE-2021-21481 and SAP lists it with a severity score of 9.6 out of 10. NIST, however, gives it a base score of 8.8, which makes it a high-severity risk.
The problem addressed by the update is that the Migration Service did not perform an authorization check. Unauthorized attackers could access configuration objects to obtain administrative rights on the system.
Other fixes SAP delivered on its Security Patch Day cover vulnerabilities that the company assessed as having high-severity:
| Security Note | Bug Description | CVE | Severity Score |
| 3017908 | - information disclosure in SAP NetWeaver Master Data Management | CVE-2021-21482 | 8.3 |
| 3017823 | - information disclosure in SAP Solution Manager | CVE-2021-21483 | 8.2 |
| 2993132 | - missing authorization check in SAP NetWeaver AS ABAP and SAP S4 HANA (SAP Landscape Transformation) | CVE-2020-26832 | 7.6 |
| 3039649 | - unquoted search path in SAPSetup | CVE-2021-27608 | 7.5 |
| 3001824 | - information disclosure in SAP NetWeaver AS for Java (Telnet Commands) | CVE-2021-21485 | 7.4 |
Additional patches from SAP released this week are for medium-severity vulnerabilities. The company says that multiple bugs affecting the same product can be addressed by one security note.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now