By Jake Longden, Cofense Phishing Defense Center
Telegram is a popular messaging app. Its encrypted messages, and potential message self-destruct options, can be attractive to legitimate users looking for more privacy and protection than standard/legacy messaging options. This, however, can also be appealing to threat actors for illegitimate purposes.
In addition to the standard messaging application, Telegram also offers API options that allow users to create programs that use Telegram messages for an interface. The Cofense Phishing Defense Center (PDC) has observed a new phishing campaign that posts the harvested credentials utilizing the Telegram API.
Figure 1: Email Header
To add authenticity to the email, the threat actors have spoofed the email address so that it appears to be from an internal address ([email protected]). However, the address is an external one ([email protected]).
This, combined with the subject line and the heading of the email body, creates a sense of urgency and importance for the email to better attract the user’s interest.
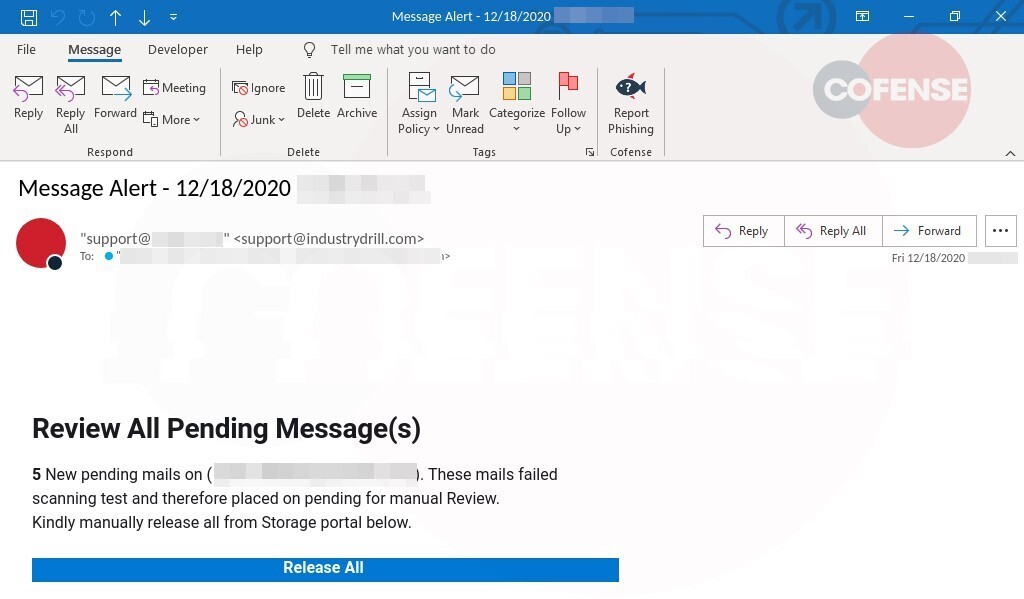
Figure 2: Email Body
The user is presented with a notice advising that they have messages to review. The bold and large title attracts attention, and is followed by further information to clarify the purpose of the email. Then there’s a button for the user to click to “Release All” the blocked emails to their inbox.
This follows a common style of emails sent by SEGs (secure email gateways) when they have blocked an email from reaching the user’s mailbox. It allows users to analyze the blocking policy, then decide if the policy was correct before opting to release the email to their inbox. Here, the threat actor has added the recipient’s email address to the body to provide a personal touch.
In taking this approach, the threat actor has exploited methods used in multiple phishing campaigns designed to gain users’ trust (by spoofing an internal source), and then reducing critical analysis.
Upon examination of the URL, we see that the recipient’s email address has been coded so that the phishing page can prefill some data when it loads.
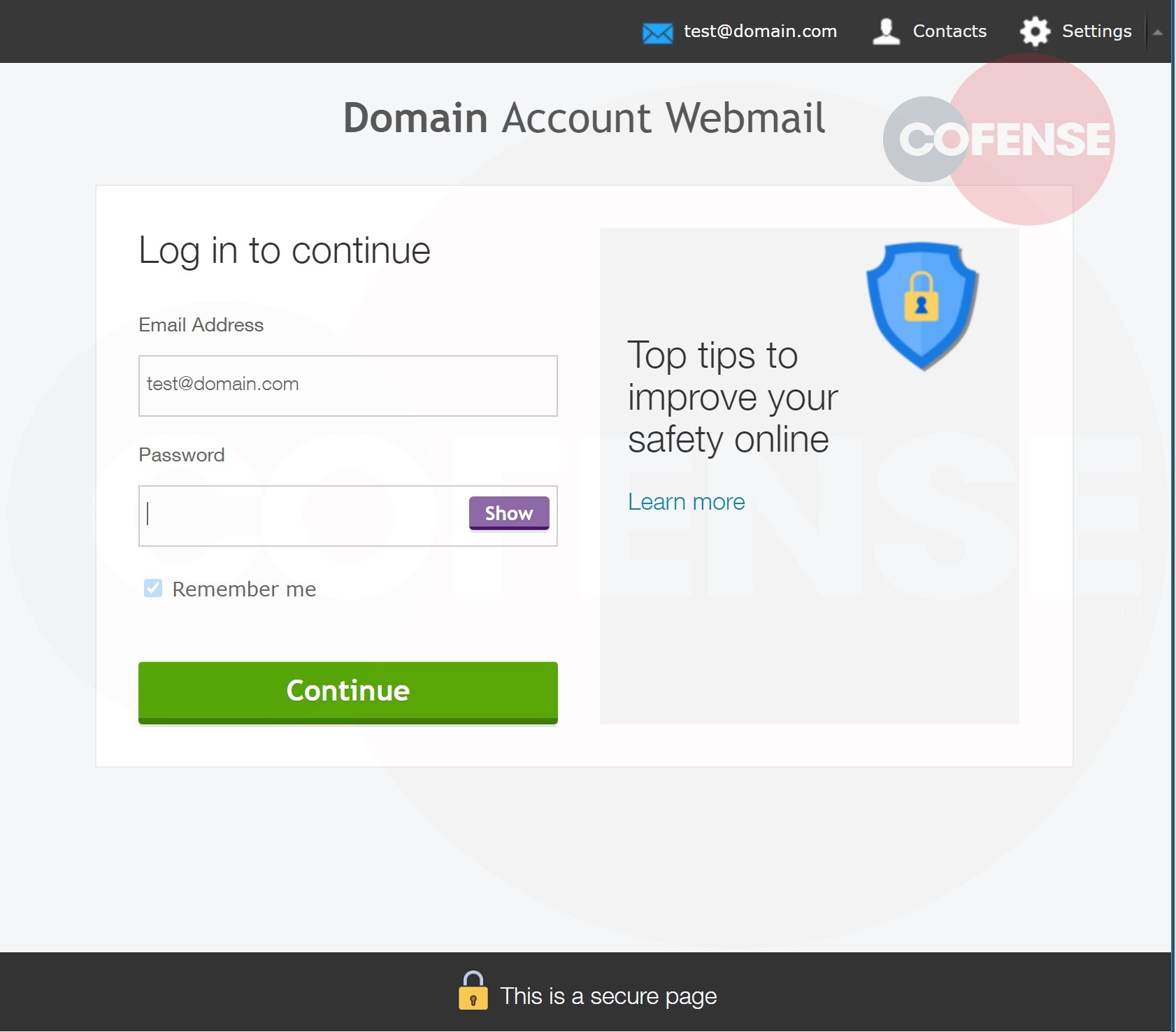
Figure 3: Phishing Page
Once the button is clicked, the user is redirected to a page that appears to be a Webmail login page. We can see that the page has pulled the email address from the initial URL then placed it at the top of the page and in the email address field for the login. The base domain from the user’s address has also been highlighted in bold above the login fields in the account webmail header.This construction makes the page look more legitimate and relevant to the user. However, the URL of the page gives indications that this is not entirely the case. In an attempt to further the appearance of legitimacy for the URL, the subdomain contains both “account-web” and “office365,” two common names for login pages.
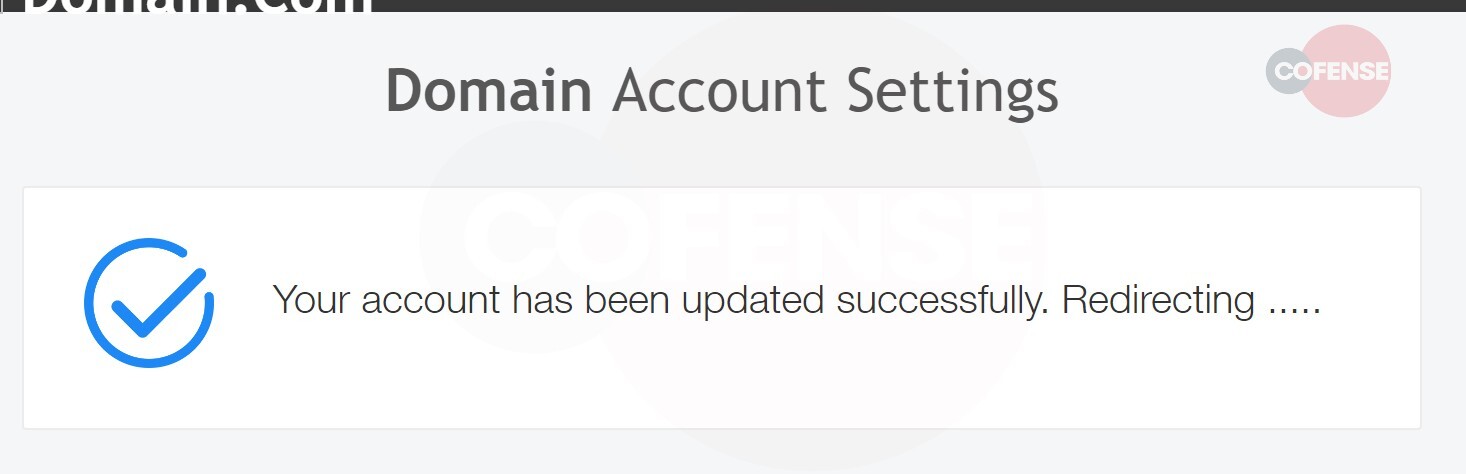
Once the password has been entered, and the “Continue” button has been clicked, the credentials are posted to the Telegram API. The user is redirected with a message stating that their account has been updated successfully. Finally, the page pulls the domain from the email address, redirecting to that website. In this way, the threat actor further heads off user suspicion.
Figure 4: Final Message
It’s a simple matter to prevent users from posting credentials to unauthorized webpages. Once the malicious domain has been identified, it can be blocked. However, by utilizing the Telegram API, the threat actor is working to circumvent interference. They’re complicating methods for removing stored credentials that have been harvested, and can view and access these credentials at their convenience on a page they control.
| Network IOC | IP |
| hXXps://www[.]epanorama[.]net/counter[.]php?url=hxxps://account-weboffice365config[.]firebaseapp[.]com/ | 104[.]27 [.]147 [.]211 172 [.]67 [.]153 [.]86 104 [.]27 [.]146.211 |
| hXXps://account-weboffice365config[.]firebaseapp[.]com/ |
151 [.]101 [.]65 [.]195 |