
Microsoft Research has announced a cloud-based malware detection service called Project Freta to detect rootkits, cryptominers, and previously undetected malware strains lurking in your Linux cloud VM images.
Mike Walker, Senior Director of New Security Ventures at Microsoft, stated, “Project Freta is a roadmap toward trusted sensing for the cloud that can allow enterprises to engage in regular, complete discovery sweeps for undetected malware,” in a blog post released by the company.
Malware detection strategies rely on “sensors,” i.e., certain activities happening on a system based on a limited dataset, predicting the presence of a malware strand. However, this model is outrun by malware creators who, from time to time, find innovative ways to evade these predictive, sensor-based technologies.
The datasets collected so far on cyberattacks focus on what was detected by these “sensors” rather than what was missed. Project Feta aims to solve this problem by reversing the dataset.
If Freta can inspect each VM image's volatile memory from a large dataset of snapshots, it can better learn different environments and how malware behaves in each of them.
Instead of focusing on lowest-resourced attackers that can be easily spotted by existing sensors, Project Freta aims to stop highly resourced attackers by automatically fingerprinting and analyzing snapshots of thousands of Linux cloud VMs.
At its inception, Freta supports over 4,000 kernel versions.
“Project Freta was designed and built with survivor bias at its core. It is a security project designed from first principles to drive the cost of sensor evasion as high as possible and, in many cases, render evasion technically infeasible,” continues the blog post.
Project Freta is based on four sensing tenets, which require no program can:
- Detect a sensor is present before it installs itself in the environment,
- Hide from the sensor as long as the program is within the monitoring view of the sensor
- Burn itself, as in erasing or modifying itself upon detecting a sensor is present
- Sabotage the sensor so that it cannot acquire the malicious program
If these four properties can be guaranteed in infrastructure, even the stealthiest of malware can be spotted and stopped.
This effort aims to make it extremely difficult and economically unfeasible for highly skilled malware creators to produce stealthy, undetectable strands, therefore halting cyberattacks on the cloud infrastructure.
“What would happen if a commercial cloud could guarantee the capture of malware, no matter how expensive or exotic, in volatile memory? Producers of stealthy malware would then be locked into an expensive cycle of complete re-invention, rendering such a cloud an unsuitable place for cyberattacks. This is the future we wish to realize,” added Walker.
The key benefits of using Microsoft Freta include:
-
“Detect novel malicious software, kernel rootkits, process hiding, and other intrusion artifacts via agentless operation by operating directly on captured VM snapshots
-
Very easy to use: submit a captured image to generate a report of its content
-
Memory inspection means no software to install, no notice to malware to evacuate or destroy data
-
Designed for automating IR-like discovery tasks directly into a cloud fabric -- though volatile memory snapshots captured from an acquisition tool can also be used for bare iron scenarios where virtualization is not available”
A first look at Microsoft's Project Freta
After learning about this project, we immediately wanted to give it a test to see how easy it was to analyze Linux virtual machine images for rootkits.
To get started, you need to head to https://freta.azurewebsites.net and login with a Microsoft account.
You will then be shown a dashboard showing sample virtual machines and their VM snapshot images and detailed reports.
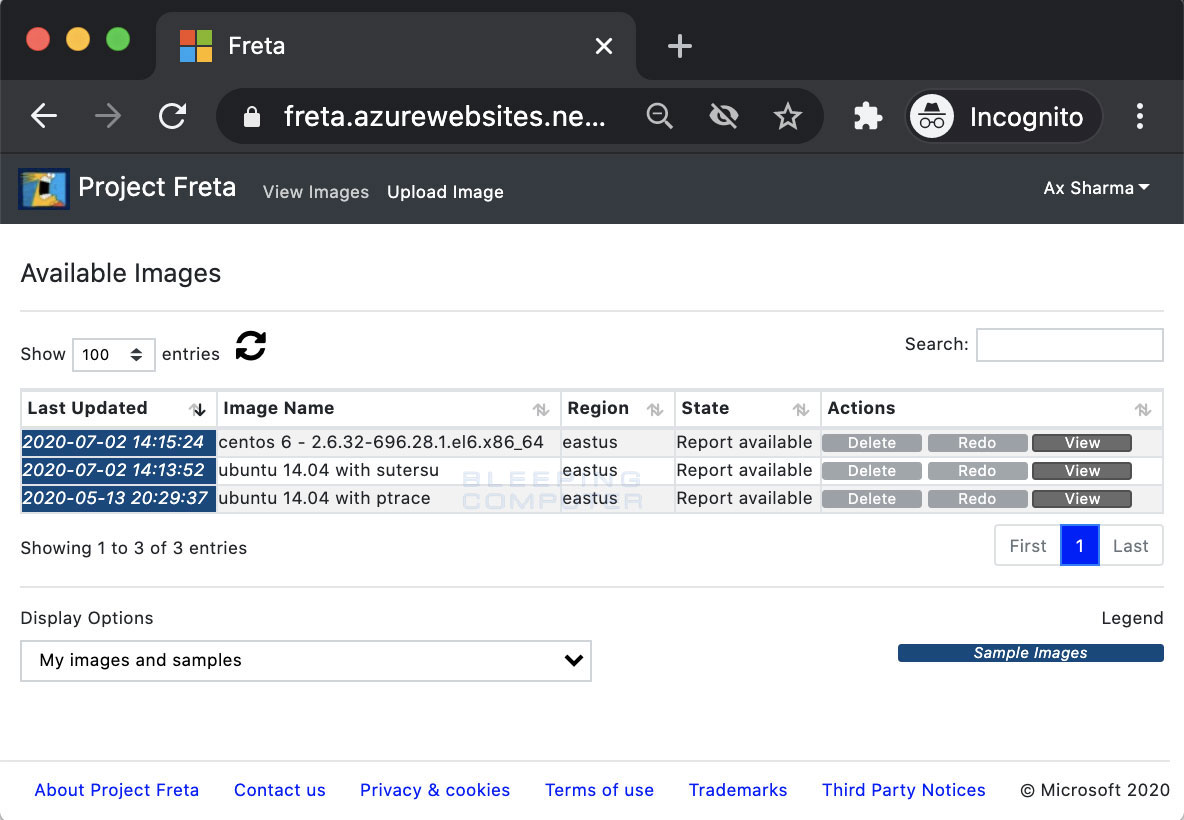
Source: BleepingComputer
Viewing a report will allow you to see various information, including debugged processes, Kernel calls, open files, and of course, potential rootkits.
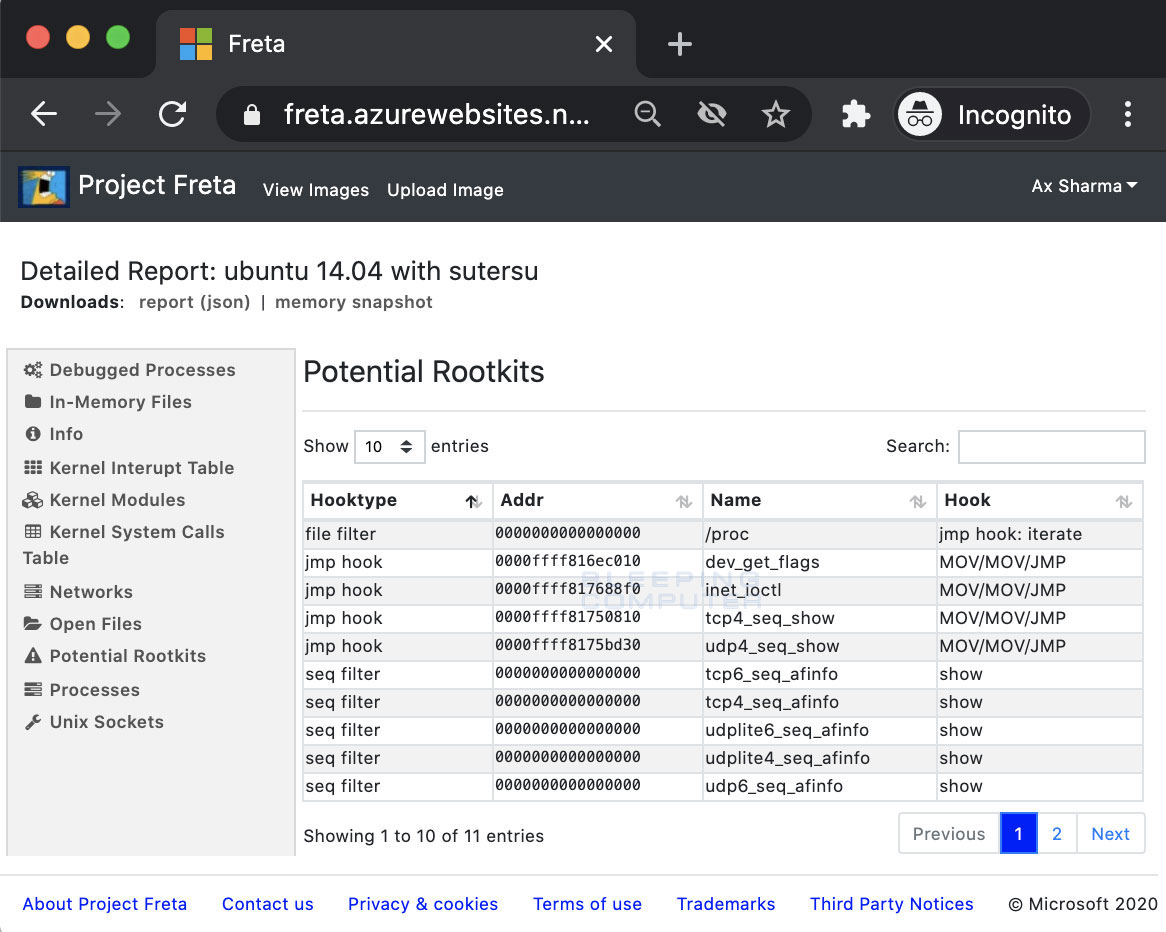
Source: BleepingComputer
A more detailed display of this report can be shown in this image from Microsoft.
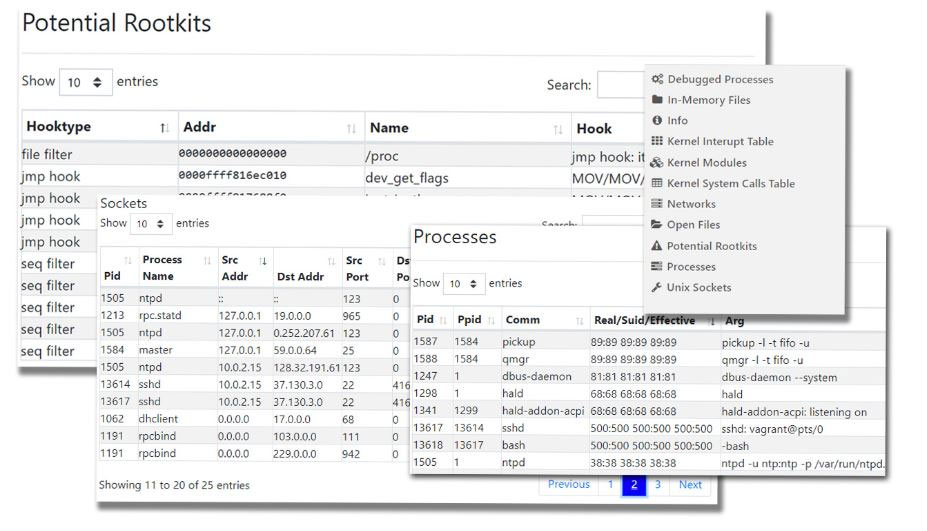
Source: Microsoft
Users also can generate a report in JSON format that can be imported into their tools.

Source: BleepingComputer
Of course, this project would be useless if we couldn't upload our own Linux VM images for analysis.
The dashboard allows you to upload a virtual machine image in the Elf Core Dump of Physical Memory (.core), LiME image (.lime), Raw Physical Memory Dump (.raw), Hyper-V Memory Snapshot (.vmrs) formats.
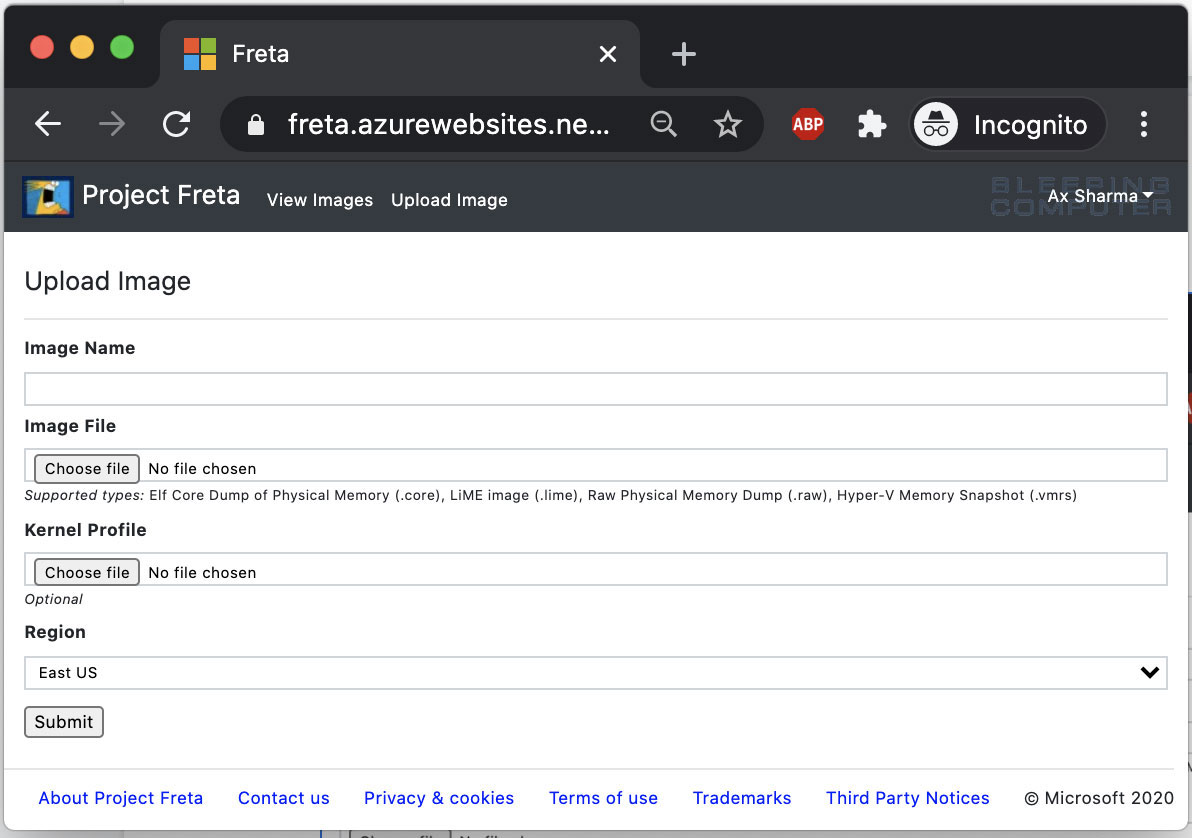
Source: BleepingComputer
Once submitted, Project Freta will perform an analysis of the image and list any discovered potential rootkits.
Of course, in a real-world large scale cloud operation, tasks like uploading VM snapshots and analyzing detailed reports need to be done in bulk.
A Freta API makes it possible to do bulk uploads for analysis, and Microsoft has released source code for API integration on their GitHub repository.
In addition to offering a novel security forensics tool for their customers, data gathered from a “democratization effort” like Project Freta provides tremendous value for Microsoft as it gives them insight into the makeup of a wide range of VM cloud instances.
At this time, Project Freta is only available for Linux images, Microsoft hopes to add support for Windows and AI-based decision-making in the future.
"A great deal of development lies ahead for Project Freta: adding support for Windows, extending our automated program analysis capabilities, and experimenting with AI-based decision-making for novel threat detection," Microsoft stated.


Comments
jdally987 - 3 years ago
Oh yeah I'd just love to let Microsoft within a 25-mile radius of my Linux systems, can't wait for the next Embrace-Extend-Extinguish Windows®-"For Linux®" Innovation®®® to install with root permissions!
(I know it's for cloud images but...)