
Video game companies are once again victims of the Winnti hacking group, who used new malware that researchers named PipeMon and a novel method to achieve persistence.
PipeMon is a modular backdoor identified earlier this year on servers belonging to several developers of massively multiplayer online (MMO) games.
Past activity catches up
Winnti activity has been detected as far back as 2011. Most of its victims are from the video game and software industry but the group also targeted organizations in the healthcare and education sectors.
The threat actor is well-known for supply-chain attacks, trojanizing software used by millions of users (Asus LiveUpdate, CCleaner) or in the financial sector (NetSarang).
Researchers at cybersecurity company ESET found in February a new backdoor associated with Winnti. Two variants of the malware were found on servers of multiple developers of massively multiplayer online (MMO) games from South Korea and Taiwan.
The security company knows of at least one instance where the threat actor was able to compromise a victim’s build system. Had they successfully infiltrated, Winnti could have planted malware inside the video game executable.
“In another case, the game servers were compromised, which could have allowed the attackers to, for example, manipulate in-game currencies for financial gain” - ESET
In a report today, ESET says that the pile of evidence discovered in these attacks points directly at Winnti. Despite the novelty of PipeMon, the backdoor was signed with a using a certificate belonging to a video game company that the threat actor attacked in 2018.
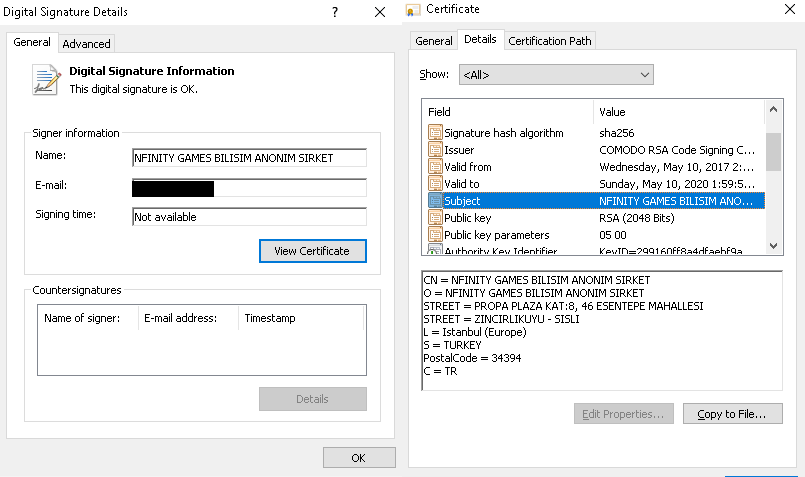
This confirmation is not alone. The hackers reused some command and control (C2) domains observed in other campaigns and a custom login stealer that was previously seen at other Winnti victims.
Staying active on the system
Of the two PipeMon variants discovered, the researchers could establish for only one how it installed and achieved persistence.
“PipeMon's first stage consists of a password-protected RARSFX executable embedded in the .rsrc section of its launcher” - ESET
To make sure that the malware remains active on the systems, Winnti used Windows print processors (DLLs) that convert spooled data from a print job into a format readable by a print monitor.
A malicious DLL loader drops where the print processors reside and registered as an alternative print processor. This is done by modifying one of the two registry values (the typo in the registry key does not impact installation):
HKLM\SYSTEM\ControlSet001\Control\Print\Environments\Windows x64\Print Processors\PrintFiiterPipelineSvc\Driver = “DEment.dll”
HKLM\SYSTEM\CurrentControlSet\Control\Print\Environments\Windows x64\Print Processors\lltdsvc1\Driver = “EntAppsvc.dll”
Next, the malware restarts the print spooler service to load the malicious process. Since the service starts every time the computer boots up, persistence is achieved.
ESET notes that a similar technique was seen with DePriMon downloader but the reseachers believe that the way PipeMon does it has not been documented before.
According to the research, PipeMon is a modular backdoor, each component being a DLL with different functionality.
They are encrypted on the disk and hidden under the innocuous-looking names below. Custom commands can load other modules on demand.
- banner.bmp
- certificate.cert
- License.hwp
- JSONDIU7c9djE
- D8JNCKS0DJE
- B0SDFUWEkNCj.logN
ESET notes that the updated variant for PipeMon was likely written from scratch, although they observed the same code structure.
For the past decade, Winnti has been developing its arsenal of malicious tools and carrying out attacks against a variety of targets. Its predilection for game companies and supply-chain attacks is still notable in its most recent activity.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now