Fraudsters are trying new things to bypass security controls in Office 365 and added a CAPTCHA page in the chain of redirects that ends on a phishing template for login credentials.
To lure potential victims to the malicious page, the threat actor sent them an email purporting to be from the Supreme Court and claiming to deliver a subpoena for a hearing.
Real CAPTCHA, real risk
This attack was not part of a massive campaign, as it was sent to a small number of individuals in targeted organizations, says Chetan Anand, co-founder of Armorblox.
By sending the message to just a few users, there is a good chance that the fraudulent attempt passes unnoticed. Combined with a domain name that has not been analyzed before (zero-day link), the email is likely to bypass protections.
Clicking on the alleged subpoena in the fraudulent message triggered a series of redirects that took the recipient to a working CAPTCHA page, typically used to determine if the user is human or a bot.
The presence of such a challenge-response test would likely make the user believe that the chain of events was legitimate. This is also one of the final steps and it mentions the victim’s name and the reason for the challenge.
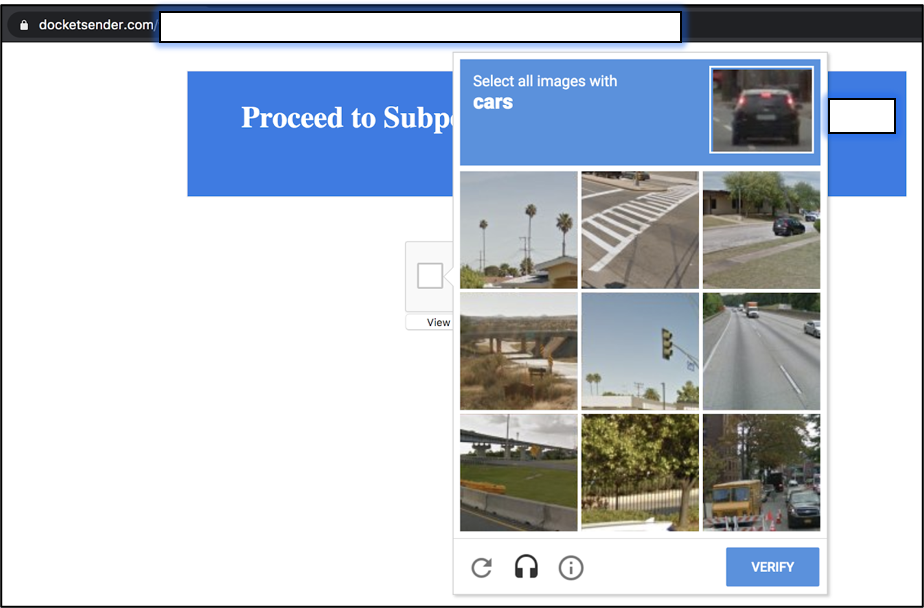
Despite some grammar mistakes, the challenge is real and has a test that users need to solve to prove their human condition.
Anand says that including a CAPTCHA makes it more difficult for security solutions that analyze URL redirection to reach the final destination and detect the attempt as malicious.
After going through the redirects and hoops, the user lands on the final phishing page, which is made to look like a valid Office 365 login screen. A look at the URL (invoicesendernow[.]com), though, shows that it is fake.
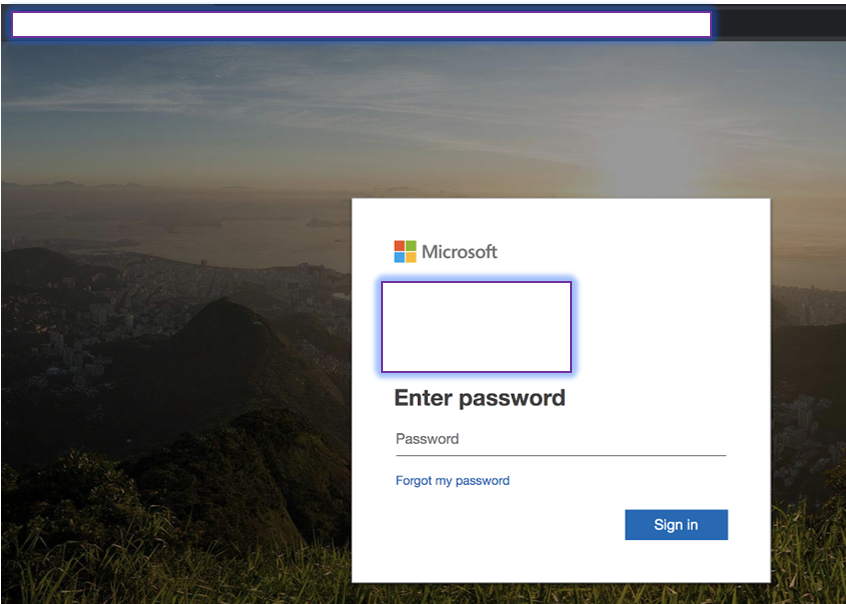
The actors put some effort into making this page look as credible as possible and save from some details, they were successful.
“This page would pass most eye tests during busy mornings, with people happily assuming it to be a legitimate Microsoft page. A closer look at the domain reveals that this is a lookalike page built specifically for the target.”
Users should be suspicious of messages about an urgent task and should take a closer look at the phrasing and grammar mistakes in the text. Before typing in login details, it is wise to check if the URL in the browser address bar matches the resource you're trying to access.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now