A phishing campaign using Office 365 voicemail lures to trick them into visiting landing pages designed to steal their personal information or infect their computers with malware.
The phishing emails delivered by the operators behind this series of attacks use the old trick of reversing some of the text elements in the source code and rendering forward within the email displayed to the target, with a twist: this time it involves using Cascading Style Sheets (CSS).
Reversing text in an email's HTML code helps attackers bypass some automated text matching models used by Secure Email Gateways (SEG) use to differentiate between legitimate emails and phishing messages.
CSS tricks to scam email gateways
"Our primary finding is that CSS offers tools for mixing scripts like Arabic and Latin, which naturally flow in different directions on the page," Inky CEO Dave Baggett explains.
"Attackers can abuse this feature to make backwards text render forwards in an email, thereby hiding the text from the Secure Email Gateway (SEG) while preserving the normal appearance to the human recipient."
.png)
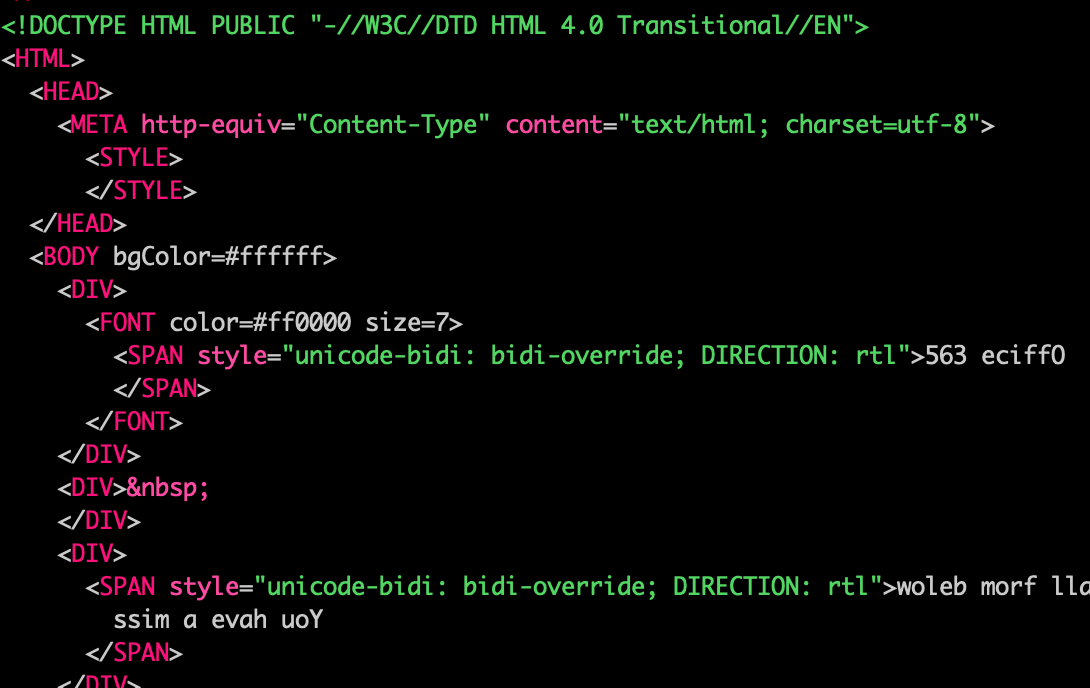
While the phishing sample Inky analyzed looked like an ordinary fake voicemail notification scam email, a second take revealed that the 'Office 365' logo was actually text-based and in the plain text source code it showed up as '563 eciffO,' a sure sign that something's not right.
The scammers used the unicode-bidi: bidi-override; DIRECTION: rtl CSS property to render that reversed text right-to-left so that it displays as 'Office 365' after it hits the target's inbox and the email is read.
This is a simple trick to circumvent SEG Bayesian statistical models that make use of text sequences for spotting phishing mail.
SEGs looking through the wrong window
"These models the workhorse of mail protection since the 90s learn, for example, that dollar signs in the subject line and 'make money fast!' in the body correlate with spam," Baggett explains.
"These models also learn to detect scam-indicative patterns like 'Office 365 ... voicemail.' While the presence of a pattern like this obviously doesn't guarantee a mail is bad, it may trigger the SEG to do a deeper analysis of the mail."
Since SEGs look at the actual source code of the phishing email to look for signs of malicious intent and the text that would tag the message as phishing is not present in HTML code, this CSS-based text reversing trick allows the attackers to derail SEGs' pattern match efforts.
This kind of tactic helps phishing attacks to pass through traditional SEGs which are designed to only analyze the raw HTML elements without rendering the email to learn the rendered content the end-user will see.
Old tricks for new dogs
To detect phishing attacks this or variations of this technique, SEGs should first render the email's HTML code to have access at both the source code and the final rendered email.
This way, they can compare between them and quickly notice any misdirection designed to conceal some text elements in phishing emails that could expose their malicious nature and prevent them from reaching the targets' inboxes.
Scammers have been using a similar trick in their spam emails as early as 2005 (1, 2, 3) or to camouflage malicious binaries as benign documents (1, 2), with Unicode right-to-left overrides character overrides (LTRO and RTLO) expressed as HTML entities being employed to reverse text in the emails' source code or in files' names.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now