
A critical privilege escalation vulnerability found in the WordPress SEO Plugin – Rank Math plugin can allow attackers to give administrator privileges to any registered user on one of the 200,000 sites with active installations if left unpatched.
Rank Math is a WordPress plugin described by its developers as 'the Swiss army knife of WordPress SEO' and designed to help website owners to attract more traffic to their sites through search engine optimization (SEO).
The plugin comes with a setup wizard that configures it via a step-by-step installation process and features support for Google Schema Markup (aka Rich Snippets), keyword optimization, Google Search Console integration, Google keyword rank tracking, and a lot more.
Everyone is a WordPress admin
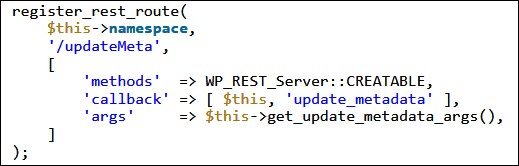
The Rank Math privilege escalation vulnerability was found by Defiant's Wordfence Threat Intelligence team in an unprotected REST-API endpoint.
Successfully exploiting this bug "allowed an unauthenticated attacker to update arbitrary metadata, which included the ability to grant or revoke administrative privileges for any registered user on the site," according to Defiant QA engineer Ram Gall.
To make things even worse, attackers could also lock admins out of their sites by revoking their administrator privileges seeing that a lot of WordPress websites have a single admin user.
"Note that these attacks are only the most critical possibilities," Gall explains. "Depending on the other plugins installed on a site, the ability to update post, term, and comment metadata could potentially be used for many other exploits such as Cross-Site Scripting (XSS)."
Second vulnerability found in another REST-API endpoint
The researchers also discovered a second vulnerability that made it possible for unauthenticated attackers "to create redirects from almost any location on the site to any destination of their choice."
The bug was found in one of Rank Math's optional plugin modules that would help users to create redirects on their WordPress websites.
"This attack could be used to prevent access to all of a site’s existing content, except for the homepage, by redirecting visitors to a malicious site," according to Gall.
The development team released Rank Math 1.0.41 on March 26, a patched version with fixes for the REST API security issues reported by Defiant's research team on two days earlier on March 24.
As at least one of these two vulnerabilities is seen as critical, Rank Math users are strongly recommended to update to the latest version 1.0.41.2 that contains fixes for both issues.
WordPress sites under siege
Since the start of 2020, attackers have been attempting to take over WordPress websites by exploiting recently patched or zero-day bugs in plugins installed on hundreds of thousands of sites.
In late February attacks on tens of thousands of WordPress sites abusing critical bugs including a zero-day in multiple plugins were spotted by researchers while being used that could have lead to backdoors being planted and rogue admin accounts being created.
Hackers have also tried to compromise or wipe WordPress sites by exploiting vulnerable plugins with an approximated number of 1,250,000 active installations, as well as several bugs in the WordPress GDPR Cookie Consent plugin used by over 700,000 websites.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now