When it comes to the release of proof-of-concept (PoC) exploits, more security experts agree that the positives outweigh the negatives, according to a recent and informal Threatpost poll.
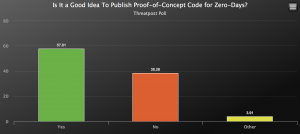
 Last week, Threatpost conducted a reader poll and almost 60 percent of 230 security pundits thought it was a “good idea” to publish PoC code for zero days. Up to 38 percent of respondents, meanwhile, argued it wasn’t a good idea.
Last week, Threatpost conducted a reader poll and almost 60 percent of 230 security pundits thought it was a “good idea” to publish PoC code for zero days. Up to 38 percent of respondents, meanwhile, argued it wasn’t a good idea.
The debate comes on the heels of PoC code being released last week for an unpatched remote-code-execution vulnerability in the Citrix Application Delivery Controller (ADC) and Citrix Gateway products. The PoC exploits, which were published to showcase how the vulnerability in a system can be exploited, raised questions about the positive and negative consequences of releasing such code for an unpatched vulnerability.
Some argued that the code can be used to test networks and pinpoint vulnerable aspects of a system, as well as motivate companies to patch, but others in the security space have argued that PoC code gives attackers a blueprint to launch and automate attacks.
Security Motivator
Many security experts point to the role of PoC code publication in motivating impacted companies and manufacturers to adopt more effective security measures. That was the argument of one such advocate, Dr. Richard Gold, head of security engineering at Digital Shadows, who said that PoC code enables security teams to test if their systems are exploitable or not.
“Rather than having to rely on vendor notifications or software version number comparisons, a PoC allows the direct verification of whether a particular system is exploitable,” Gold told Threatpost. “This ability to independently verify an issue allows organizations to better understand their exposure and make more informed decisions about remediation.”
In fact, up to 85 percent of respondents said that the release of PoC code acts as an “effective motivator” to push companies to patch. Seventy-nine percent say that the disclosure of a PoC exploit has been “instrumental” in preventing an attack. And, 85 percent of respondents said that a PoC code release is acceptable if a vendor won’t fix a bug in a timely manner.
When it comes to the recent Citrix vulnerability (CVE-2019-19781) for instance, advocates argue that, though PoC exploits were released before a patch was available, the code drew attention to the large amounts of vulnerable devices that were online. Citrix has also accelerated its patch schedule after PoC exploits were released (though there is no proof of correlation between this and the PoC exploit releases).
“As a result [of the Citrix PoC exploits], there has been a widespread effort to patch or mitigate vulnerable devices rather than leaving them unpatched or unsecured,” Gold stressed.
A Jump in Actual Exploits
On the flip-side of the argument, many argue that the release of the Citrix PoC exploits were a bad idea. They say attacks attempting to exploit the vulnerability skyrocketed as bad actors rushed to exploit the vulnerabilities before they are patched. In fact, 38 percent of respondents in Threatpost’s poll argued that PoC exploit releases are a bad idea.
Matt Thaxton, senior consultant at Crypsis Group, thinks that the “ultimate function of a PoC is to lower the bar for others to begin making use of the exploit.”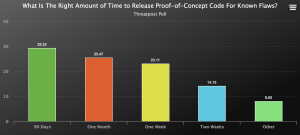
“I believe there are more negatives than positives to publishing proofs, and generally, it is not a good idea,” he told Threatpost. “In many cases, PoC’s are put out largely for the notoriety/fame of the publisher and for the developer to ‘flex’ their abilities.”
Joseph Carson, chief security scientist at Thycotic, told Threatpost that while he thinks PoC exploits can have a positive impact, “it is also important to include what defenders can do to reduce the risks such a methods to harden systems or best practices.”
“Let’s be realistic, once a zero-day is known, it is only a matter of time before nation states and cybercriminals are abusing them,” said Carson. “Sometimes they already know about the zero-day and have been abusing them for years.”
Respondents in the poll were also split about the right amount of time that’s appropriate to release PoC code after a flaw has been disclosed, with 29 percent arguing 90 days is the appropriate amount and others opting for one month (25 percent), one week (23 percent) or two weeks (14 percent).
This issue of a PoC exploit timeline also brings up important questions around patch management for companies dealing with the fallout of publicly-released code. Some, like Thaxton, say that PoC exploit advocates fail to recognize the complexity of patching large environments: “I believe the release of PoC code functions more like an implied threat to anyone that doesn’t patch: ‘You’d better patch . . . or else,'” he said “This kind of threat would likely be unacceptable outside of the infosec world. This is even more obvious when PoCs are released before or alongside a patch for the vulnerability.”
PoC Exploits Surge
At the end of the day, PoC exploits are continuing to be published. In fact, beyond the release of the Citrix PoC code, a slew of other PoC exploits were released last week, including ones for a recently patched crypto-spoofing vulnerability found by the National Security Agency (NSA) and reported to Microsoft; and another for critical flaws impacting the Cisco Data Center Network Manager tool for managing network platforms and switches.
Gold, for his part, argued that distinguishing a fine line between a theoretical vulnerability and a successful exploitation of a real system makes all the difference when it comes to PoC exploits versus active exploits.
“Once that threshold has been crossed, it is understood that attackers will most likely be exploiting this vulnerability in real attacks,” he said. “This often provided impetus to companies to patch their systems.”
Concerned about mobile security? Check out our free Threatpost webinar, Top 8 Best Practices for Mobile App Security, on Jan. 22 at 2 p.m. ET. Poorly secured apps can lead to malware, data breaches and legal/regulatory trouble. Join our experts from Secureworks and White Ops to discuss the secrets of building a secure mobile strategy, one app at a time. Click here to register.