
Image: Midjourney
The Treasury Department's Office of Foreign Assets Control (OFAC) has sanctioned four Iranian nationals for their involvement in cyberattacks against the U.S. government, defense contractors, and private companies.
OFAC also announced sanctions against two front companies—Mehrsam Andisheh Saz Nik (MASN), formerly Mahak Rayan Afzar, and Dadeh Afzar Arman (DAA)—for the Iranian Islamic Revolutionary Guard Corps Cyber Electronic Command (IRGC-CEC), an Iranian Armed Forces service that coordinates the country's cyber warfare campaigns.
Two of the sanctioned cybercriminals, Alireza Shafie Nasab and Reza Kazemifar Rahman targeted U.S. organizations while employed by MASN. Kazemifar also attacked the Department of the Treasury in spear phishing campaigns.
A third sanctioned Iranian, Hosein Mohammad Harooni, targeted the Treasury Department and other U.S. entities using spear phishing and various social engineering operations.
Komeil Baradaran Salmani, the fourth Iranian sanctioned on Tuesday, was linked to attacks against U.S. orgs coordinated by MASN, DAA, and other IRGC-CEC front companies and IRGC services like the Iranian Organization for Electronic Warfare and Cyber Defense (EWCD).
Although the Iranian threat actors are still at large, today's sanctions have frozen all U.S.-based assets and interests tied to designated individuals and entities.
Entities at least 50% owned by blocked persons are also subject to freeze, and transactions involving their assets are prohibited without OFAC authorization, while financial institutions and other organizations dealing with sanctioned individuals and companies also risk exposure to sanctions or enforcement actions.
The State Department is also offering rewards of up to $10 million for information on Kazemifar, Salmani, and Harooni, as well as the MASN and DAA IRGC-CEC front companies.
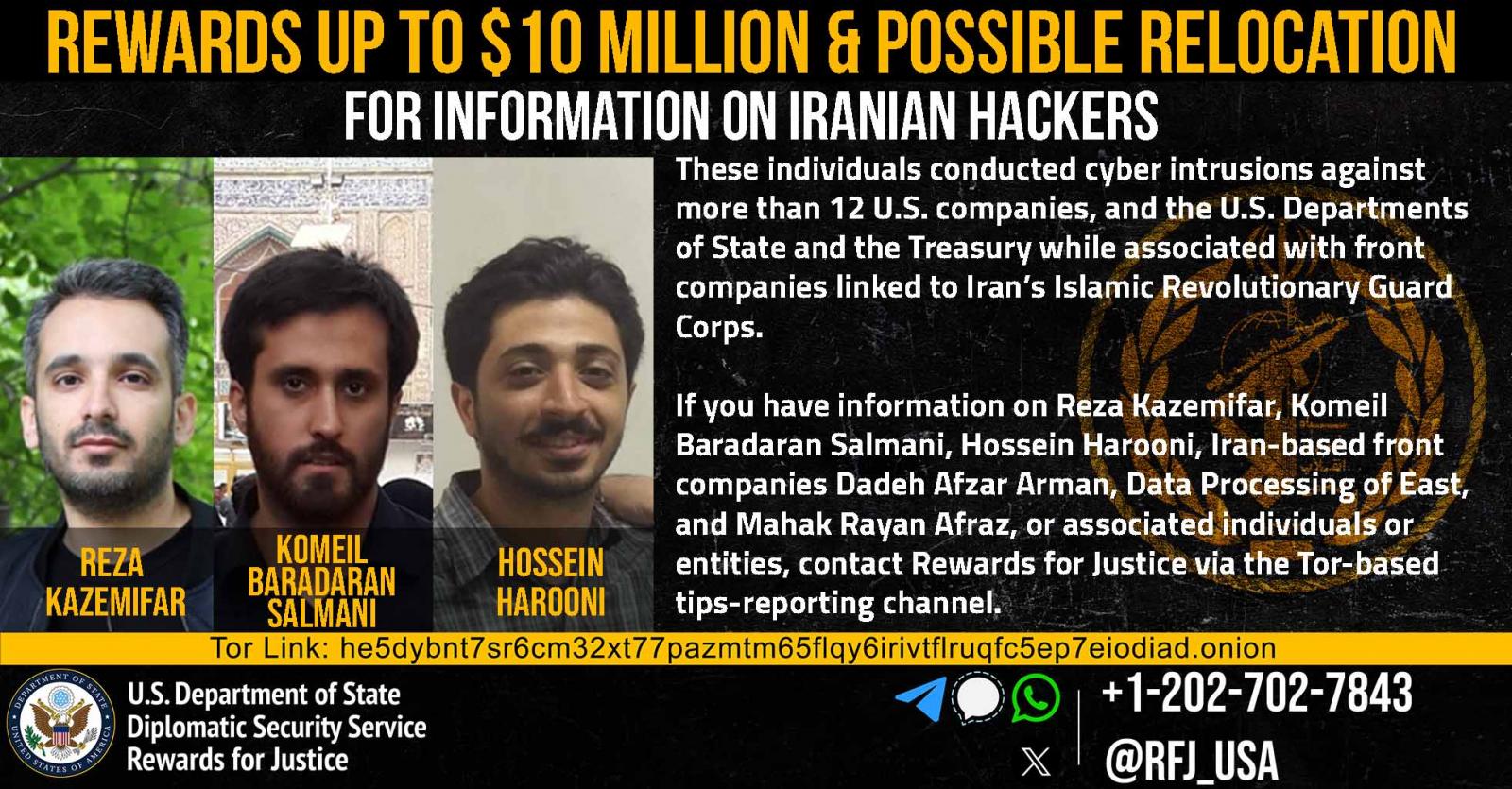
Today, the Justice Department also unsealed indictments charging Kazemifar, Salmani, and Harooni for their involvement in a cyber campaign targeting U.S. government agencies, including the U.S. Departments of State and Treasury, and private entities, mainly cleared defense contractors, between 2016 and 2021.
Alireza Shafie Nasab was also indicted in February for attacking U.S. defense contractors and other companies as part of the same multi-year cyber campaign.
"During their campaigns against one victim, the group compromised more than 200,000 employee accounts. In another campaign, the conspirators targeted 2,000 employee accounts," the Justice Department said.
"These defendants are alleged to have engaged in a coordinated, multi-year hacking campaign from Iran targeting more than a dozen American companies and the U.S. Treasury and State Departments," added Attorney General Merrick B. Garland.
The Treasury Department also sanctioned the head of IRGC-CEC, Hamid Reza Lashgarian, and IRGC-CEC senior officials Mahdi Lashgarian, Hamid Homayunfal, Milad Mansuri, Mohammad Bagher Shirinkar, and Reza Mohammad Amin Saberian in early February for their involvement in recent cyberattacks against U.S. critical infrastructure.



Comments
ZeroYourHero - 1 week ago
Oh no, sanctions! Poor Reza Kazemifar's $76.15 in Bank of America has been frozen. He will certainly regret his actions I tell you.