A phishing campaign has been discovered that doesn't target a recipient's username and password, but rather uses the novel approach of gaining access to a recipient's Office 365 account and its data through the Microsoft OAuth API.
Almost all Microsoft Office 365 phishing attacks that we see are designed to steal a user's login name and password by impersonating a Microsoft login landing page.
In a phishing campaign discovered by threat intelligence and mitigation firm PhishLabs, attackers are no longer targeting a user's login credentials, but are now using Microsoft Office 365 OAuth apps to hijack a recipient's account.
"This attack method is unique in that it's effectively malware targeting a victim's Office 365 account. It's highly persistent, will completely bypass most traditional defensive measures, and is difficult to detect and remove unless you know what you're looking for. It's really quite clever, and extremely dangerous," PhishLabs' Michael Tyler told BleepingComputer in conversations.
Attack gives access to more than email
For those not familiar with OAuth, it is a open authentication and permission standard that is commonly used by security software, social sites, and cloud services to allow third-parties to access a user's account and perform actions on their behalf.
OAuth apps gain permission by displaying a "Permissions requested" dialog that shows what permissions the third-party is requesting and then asks the user to accept the request.
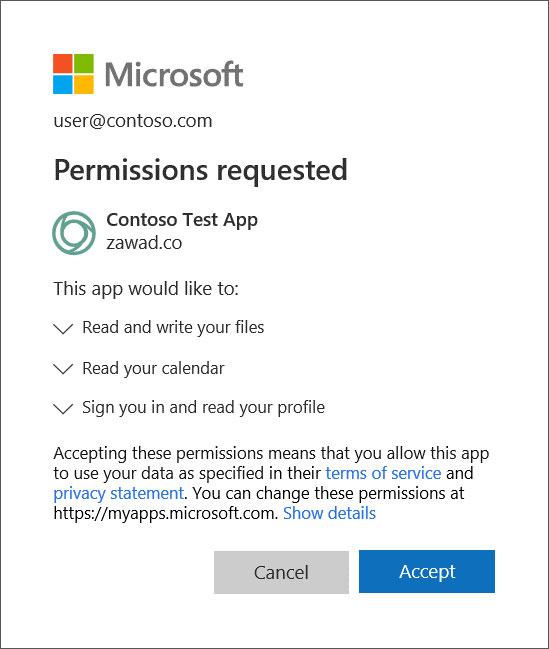
If the user accepts the app's request, a security token associated with the user will be sent to the app developer, which allows them to access the user's data and services from their own servers and applications
According to the report by PhishLabs, these OAuth phishing emails are pretending to be shared OneDrive or SharePoint files that contain a link to the shared document.

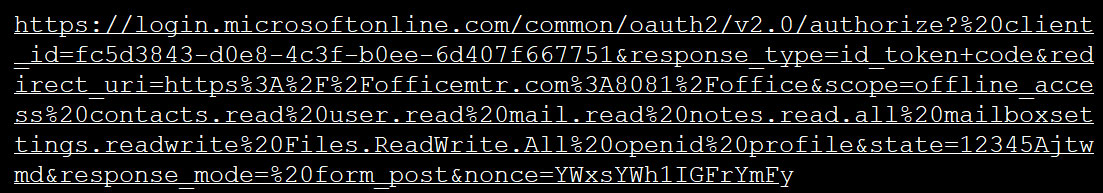
This link leads to a legitimate Microsoft URL that is used to display permission requests for OAuth apps. This URL, shown below, will attempt to give an OAuth app hosted at the site officemtr.com a variety of permissions to your account.
Before showing the OAuth app dialog, Microsoft will first ask the user to login to their Office 365 account using their normal login credentials. Once again, this is a legitimate Microsoft request and the attackers are not getting access to your login name or password.
Once a user logs in, they will be shown a 'Permissions requested' dialog for the 'O365 Access' app that asks the user to allow the app to have permission to various data and actions on the user's account.
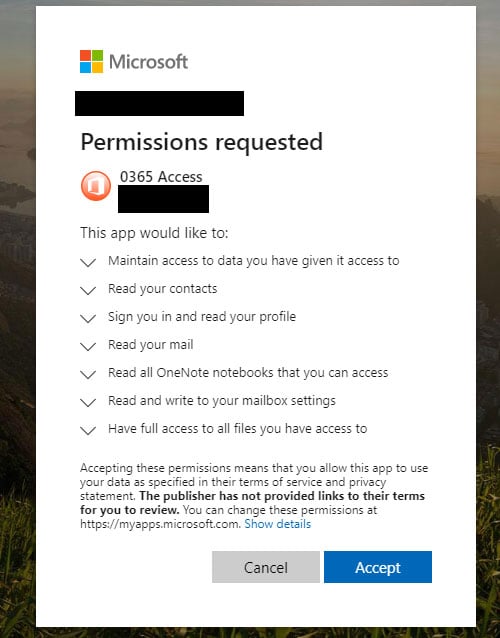
If a user accepts the request, the attacker now has the following permissions to the target's Office 365 account:
- Maintain access to data you have given it access to - "When a user approves the
offline_accessscope, your app can receive refresh tokens from the Microsoft identity platform token endpoint. Refresh tokens are long-lived. Your app can get new access tokens as older ones expire." - Read your contacts - "Allows the app to read user contacts."
- Sign you in and read your profile - "Allows users to sign-in to the app, and allows the app to read the profile of signed-in users. It also allows the app to read basic company information of signed-in users."
- Read your mail - "Allows the app to read email in user mailboxes. "
- Read all OneNote notebooks that you can access - "Allows the app to read OneNote notebooks that the signed-in user has access to in the organization."
- Read and write to your mailbox settings - "Allows the app to create, read, update, and delete user's mailbox settings. Does not include permission to directly send mail, but allows the app to create rules that can forward or redirect messages."
- Have full access to all files you have access to - "Allows the app to read, create, update, and delete all files the signed-in user can access."
These permissions give the attacker full access to a user's OneNote notebooks, stored files, and the ability to read their email and contacts, but it does not have the ability to actually send email.
With that said, the attackers have a huge amount of access to a victim's account, which is most likely being used to conduct reconnaissance that will be used in even more targeted attacks.
Tyler told BleepingComputer that this new phishing method is not being used often and is most likely highly targeted due to the amount of resources required to conduct the attack.
"We've seen significantly fewer attacks leveraging this tactic than typical phishing campaigns. This is a new attack tactic that requires a significant amount of effort and knowledge by the attacker to carry out, so it is likely that this campaign is very targeted in scope to minimize the risk of exposure."
Checking for malicious OAuth apps
As Office 365 OAuth apps can give attackers complete access to an Office 365 account, they can be used for a variety of attacks. For example, a proof-of-concept ransomware was created that utilized an OAuth app to encrypt email in a test Office 365 account.
For this reason, PhishLabs suggests that Office 365 administrators restrict the ability for users to install Apps that are not whitelisted by the administrator.
The security firm also suggests Office 365 admins use the following guidelines:
- Incorporate content into your end user Security Awareness Training that teaches how to examine ALL aspects of an email for red flags, not just URLs and sender’s address, as these may not be sufficient in phishing attacks where legitimate services are abused.
- Incorporate remediation steps for this attack method into your incident response plan. Traditional methods of remediating compromised Office 365, such as password changes, clearing sessions, or activating multi-factor authentication (MFA), are not effective for this attack method.
- Proactively review Apps or add-ins installed across your environment. For further information see Microsoft's tutorial on investigating risky apps.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now