Researchers stressing the code related to Qualcomm's implementation of the secure execution area on mobile devices found a new vulnerability that could allow access to critical data.
Top smartphone brands like Samsung, LG, or Motorola rely on Qualcomm's implementation of the Trusted Execution Environment (TEE) based on the TrustZone technology from ARM to store and handle sensitive information in a secure area inside the main processor.
TEE runs at the same time as the Android operating system and executes only trusted code completely shielded from user-installed apps.
Trusted apps (trustlets) running in TEE are also isolated from each other through software and cryptography; they receive from regular apps outside this space commands for various purposes (fingerprint recognition, decryption, payment).
Not exactly a low-hanging fruit
Due to the tight control and restrictions available, access to data in Qualcomm’s “Secure World” is deemed extremely difficult. However, security researchers from Check Point figured out a way to do it.
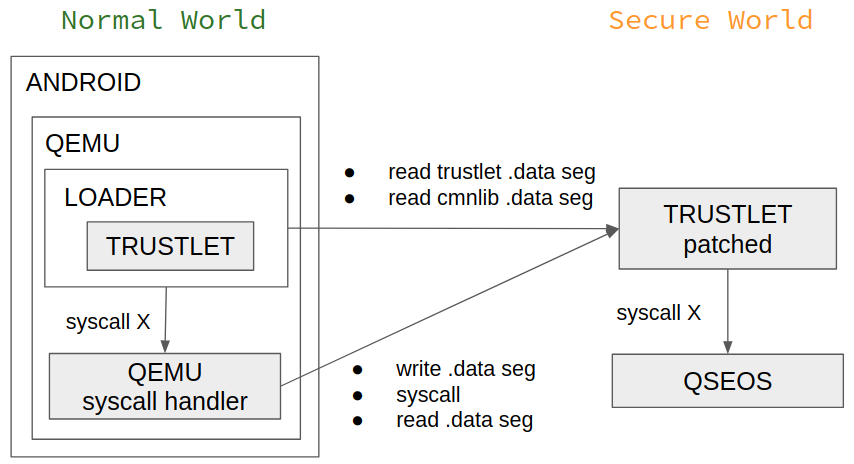
After four months of investigating, they managed to execute a trustlet in the "normal world," and loaded in the "secure world" a modified variant they needed to communicate to.
Running a trustlet (signed ELF file) in the "normal world" was possible with the help of a loader that, among others, handled the memory allocation based on the start addresses and data segments dumped from the "secure world" loading the trustlet.
A series of problems listed below was solved by patching the target trusted app ('prov') before it loaded in the "secure world:"
- Detect base addresses of a trustlet and cmnlib in the Secure world.
- Dump data segments of a trustlet and cmnlib (library that has the signed ELF format as a trustlet and also loads in memory).
- Execute a trustlet’s syscall in the Normal world.
The next step is to load a modified trustlet in the secure area without breaking the chain of trust. An exploit chain of two older vulnerabilities (CVE-2015-6639 and CVE-2016-2431) allowed loading the trustlet (widevine) in the safe zone and patching it to pass the QSEOS verification on a Nexus 6 device.
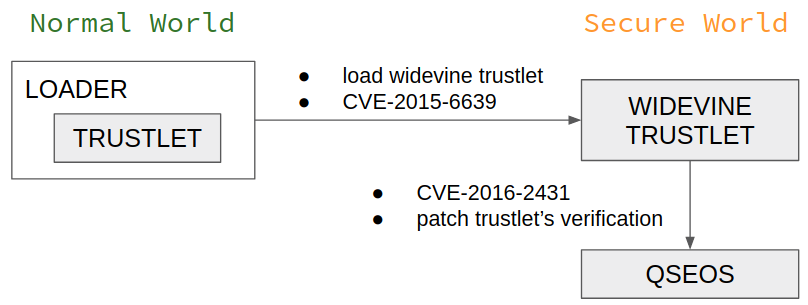
"The target of our attack is the trustlet verification algorithm. We want to “nop” the QSEOS code responsible for calculating the hash block’s signature or for comparing the actual hashes of the segments with the verified ones."
The exploit enabled the researchers to replace the hash block after the verification but before it was used to validate the segments, Slava Makkaveev writes in a report today.
The result of this is the ability to "manually calculate the hash block of a patched trustlet and push it instead of the original one," thus passing verification.
The effort paid off as the researchers could run a trusted app in the normal environment, load in the trusted zone a signed variant, and the emulator could communicate with it.
With this setup, the researchers were able to start fuzzing the trustlet in search of exploitable vulnerabilities. This endeavor led to the discovery of CVE-2019-10574, reported to Qualcomm in June and reproducible on Moto G4/G4 Plus (XT1643 and XT1640).
Check Point was also ran their fuzzer on trusted code running on Samsung and LG devices. This way they found four vulnerabilities in code implemented by Samsung (patched three), one in Motorola devices, one in LG devices (now patched), and another related to LG. All code was sourced by Qualcomm, though.
The chip maker did not patch right away, Check Point informs. The cybersecurity company says that they were notified only yesterday that the flaw has been addressed.
Update [11/15/2019]: A Qualcomm representative contacted BleepingComputer saying that the company patched the flaws discovered by Check Point. CVE-2019-10574 (rated medium) impacting Keymaster trustlet was addressed in early October, Qualcomm says, while the one affecting Widevine (rated critical) was patched in November 2014. Both fixes were delivered to OEM partners at those times.
"Providing technologies that support robust security and privacy is a priority for Qualcomm. The vulnerabilities publicized by Check Point have been patched, one in early October 2019 and the other in November 2014. We have seen no reports of active exploitation, though we encourage end users to update their devices with patches available from OEMs" - Qualcomm spokesperson
Check Point's research was initially presented at Recon in Montreal in June this year.


Comments
chilinux - 4 years ago
Which Android security patch level addresses this? I can't find CVE-2019-10574 listed in either the October or November 2019 Android Security Bulletins. Those bulletins contain entries for Qualcomm components including closed source ones. Is Qualcomm bypassing inclusion in the Google official bundle of monthly security updates by working with OEMs directly? If that is the case, I would be worried that some companies that are used to the official method of doing things from Google might get missed. Otherwise, is it possible this patch won't actually be available until the December 2019 patch level? Because of how slow some companies are, like Motorola, it might be a while before the official over the air updates are actually applied to fix this issue.