
A new threat actor is using email to impersonate government agencies in the United States, Germany, and Italy to deliver ransomware, backdoors, and banking Trojans through malicious attachments.
Since the end of October, Proofpoint researchers detected a new threat actor who has been impersonating the United States Postal Service, the German Federal Ministry of Finance, and the Italian Revenue Agency in malicious spam campaigns that deliver a variety of malware.
"Between October 16 and November 12, 2019, Proofpoint researchers observed the actor sending malicious email messages to organizations in Germany, Italy, and the United States, targeting no particular vertical but with recipients that were heavily weighted towards business and IT services, manufacturing, and healthcare," Proofpoint stated in a report published today.
Multiple campaigns targeting Germany
Through October and into November, 2019, this threat actor has targeted Germany with malspam that impersonates the German Federal Ministry of Finance called "Bundeszentralamt fur Steuern",
These emails pretend to be a notification that the user is owed a tax refund and contains malicious Word document attachments that state they have information on how to request a refund.
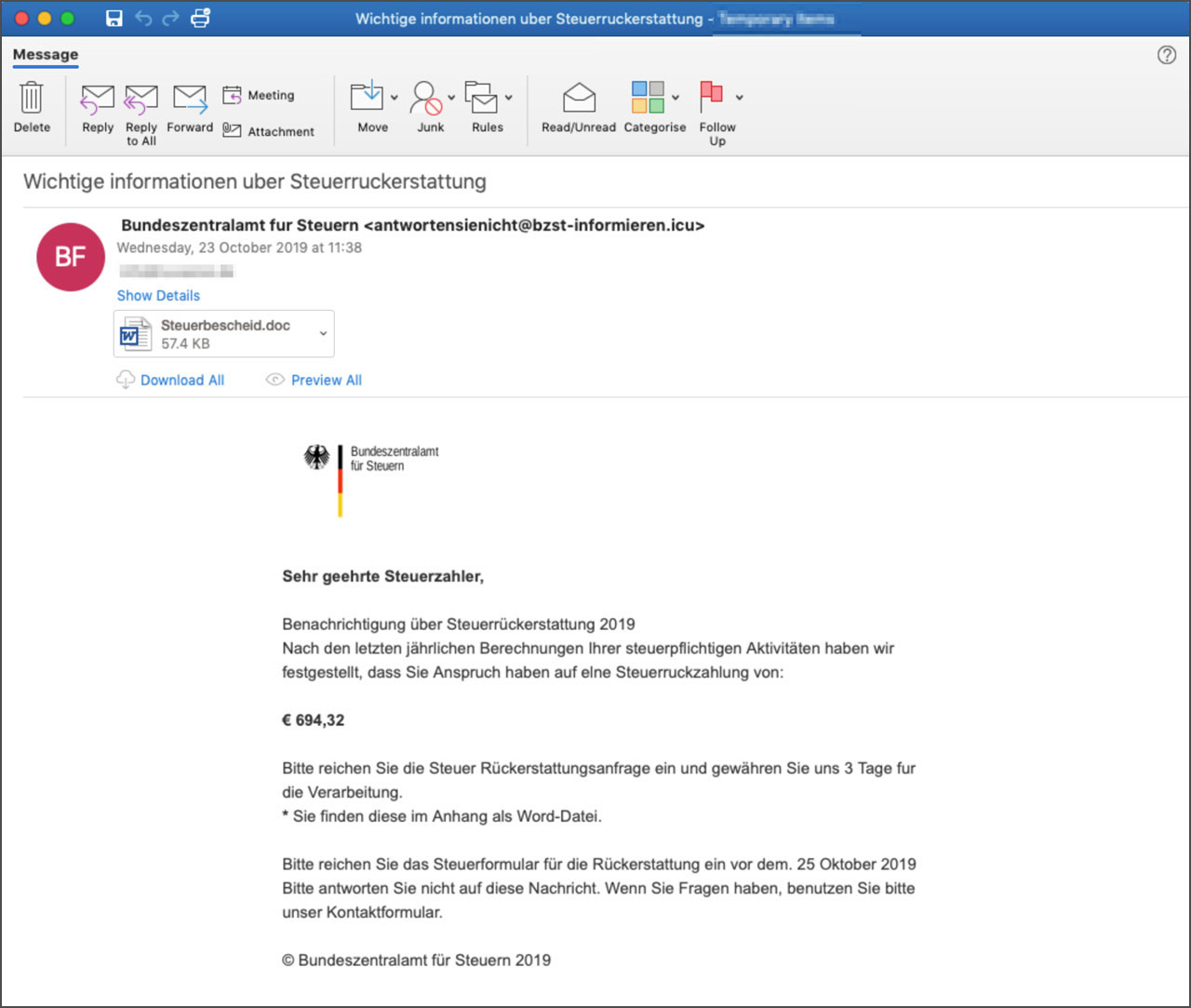
If a user opens this attachment and enables its macros, Proofpoint states that Cobalt Strike, a legitimate pentesting tool commonly used by attackers as a backdoor, as well as the Maze Ransomware will be installed on the victim's computer.
The researchers also stated that the campaign targeted IT support companies, which may have been an attempt to get backdoor access to an MSP so that the Maze Ransomware could be pushed out to the MSP's clients.
Further campaigns in October and November continued to target German recipients with similar phishing emails, with one campaign impersonating the German internet service provider 1&1 Internet AG.
Impersonating the Italian Ministry of Taxation
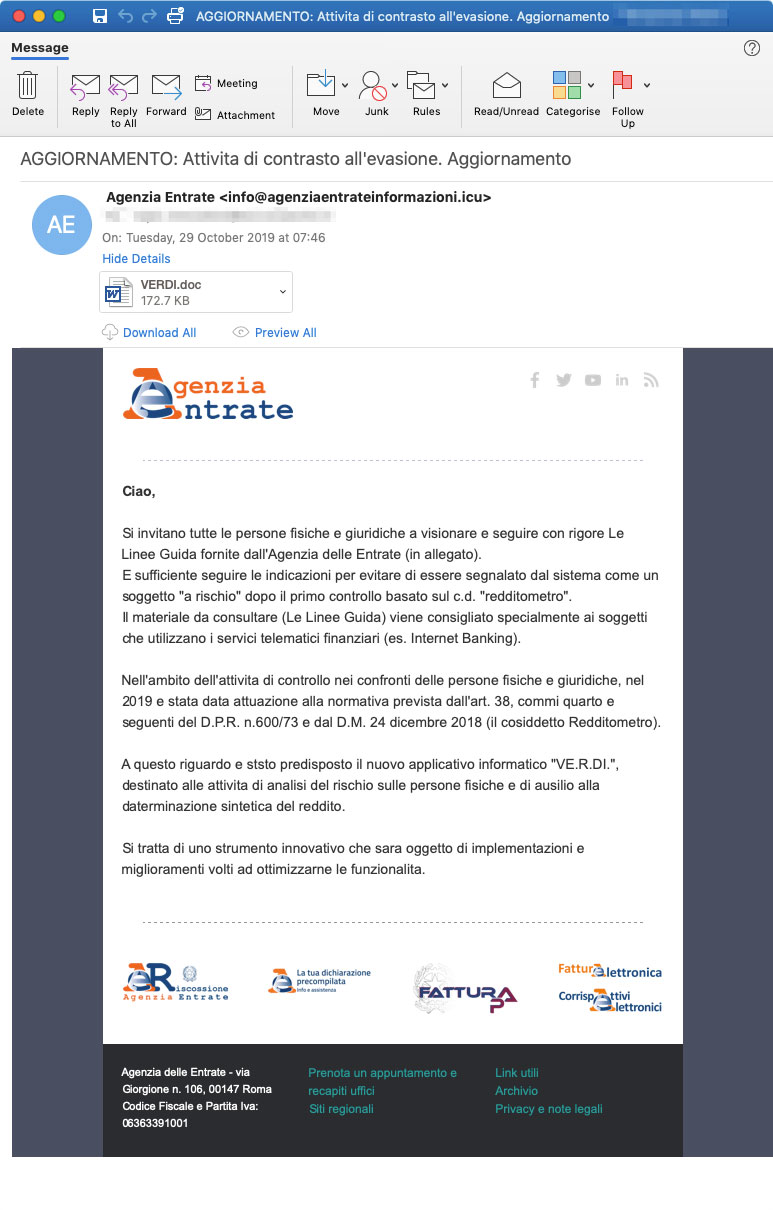
On October 29th, Proofpoint detected a new campaign from this threat actor, but this time targeting users in Italy by impersonating the Italian Revenue Agency, or the Agenzia delle Entrate,
This email pretends to be about new tax and revenue guidelines that business and consumers must follow and advises recipients to open the attachment VERDI.doc to read about them.
When the user opens the malicious document, it will state that it is encrypted using RSA encryption and that the user must enable the content in order to decrypt the file.
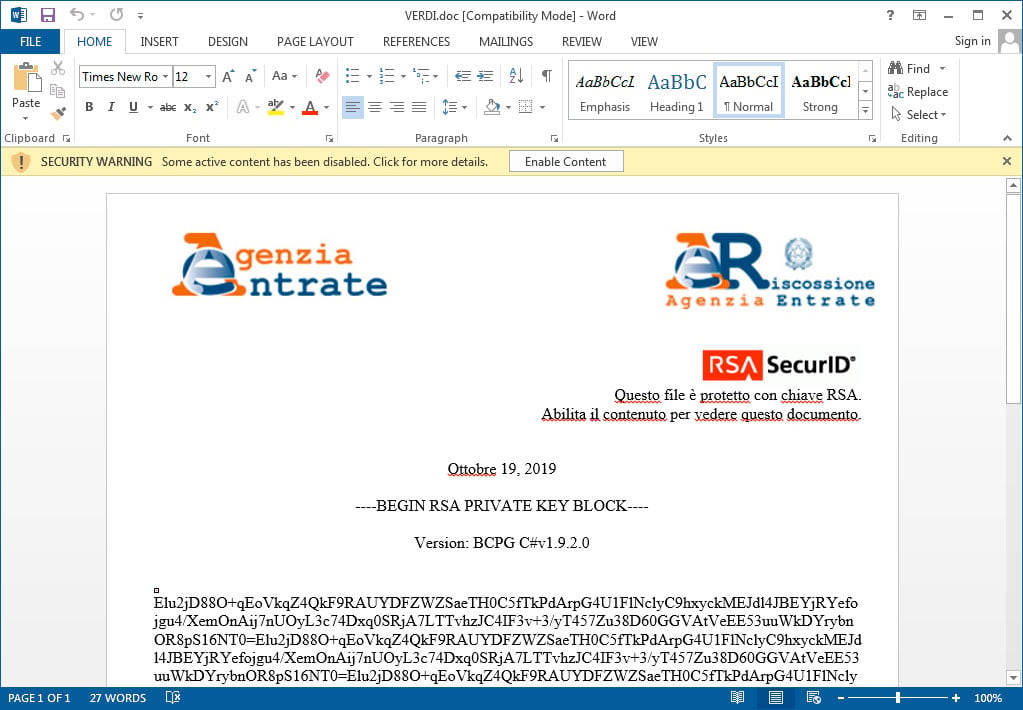
Once a user enables the content, the malicious macros execute that install the Maze Ransomware on to the victim's machine.

We reported on this campaign in detail when it occurred as it was quite large and was noticed by many security researchers.
Fake United States Postal Service deliver banking Trojans
Just recently, on November 12th, Proofpoint once again noticed a campaign from this same threat actor, but this time targeting the healthcare vertical in the USA.
In this campaign, the actor was sending emails that pretended to be from the United States Postal Service (USPS) that contained malicious Word doc attachments named "USPS_Delivery.doc".
Like the previous Italy campaign, this campaign's malicious documents pretended to be RSA encrypted and that the only way to view them was to "enable content".

If a user enabled the macros in this campaign, they would have the IceID banking Trojan installed on their computer, which will attempt to steal online banking credentials.
Impersonating govt agencies is successful
Using malspam campaigns that impersonate government agencies, convincing stolen branding, and look-alike domains to impersonate government websites have proven to be effective for this user.
"These spoofs are notable for using convincing stolen branding and lookalike domains of European taxation agencies and other public-facing entities such as Internet service providers. Most recently, the actor has attacked US organizations spoofing the United States Postal Service. The increasing sophistication of these lures mirrors improved social engineering and a focus on effectiveness over quantity appearing in many campaigns globally across the email threat landscape."
It is important to remember that government agencies will not communicate about sensitive information such as tax refunds via email.
If you receive an email with attachments that claims to be a government agency, it should immediately be considered suspicious and it is advised that you call the agency directly before opening any attachments or calling any numbers that may be listed.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now