
As the main events of this year's holiday shopping season are closing in, cybercriminals are also getting ready for the plunder by validating their stolen card details with low-value purchases on retailer's websites.
Two new such carding bots have been spotted exploiting top e-commerce platforms and card payment vendor APIs for websites or mobile apps.
Preparing for a shopping spree
With the deluge of data breaches, stolen payment card info is available in spades. Cybercriminals know that they can't rely on the cards indefinitely and that many become invalid in a short time.
Criminals need to test the validity of the cards before running larger fraudulent transactions or selling them. This process is automated through bots targeting smaller websites that typically lack anti-bot defenses.
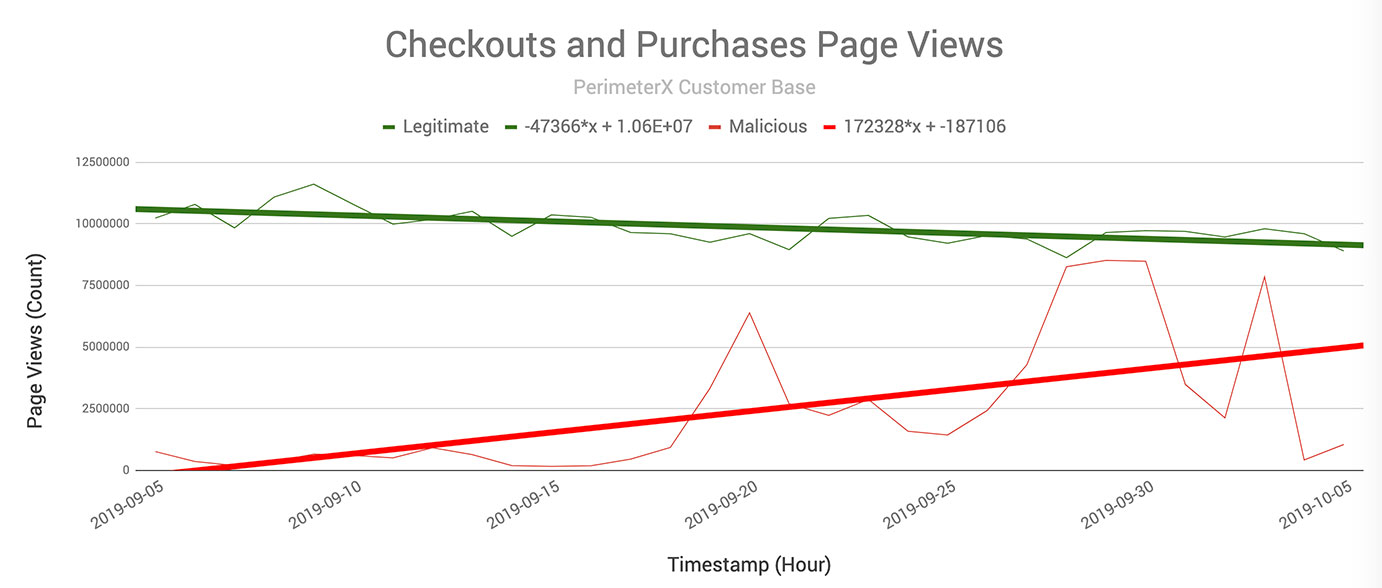
Researchers from PerimeterX web app security company found two such bots running carding attacks ahead of the holiday shopping season. Data from September shows that while legitimate traffic goes down, in expectation of events like Black Friday and Cyber Monday, malicious traffic skyrockets, sometimes increasing to over 700%.
Failing at mimicking human habits
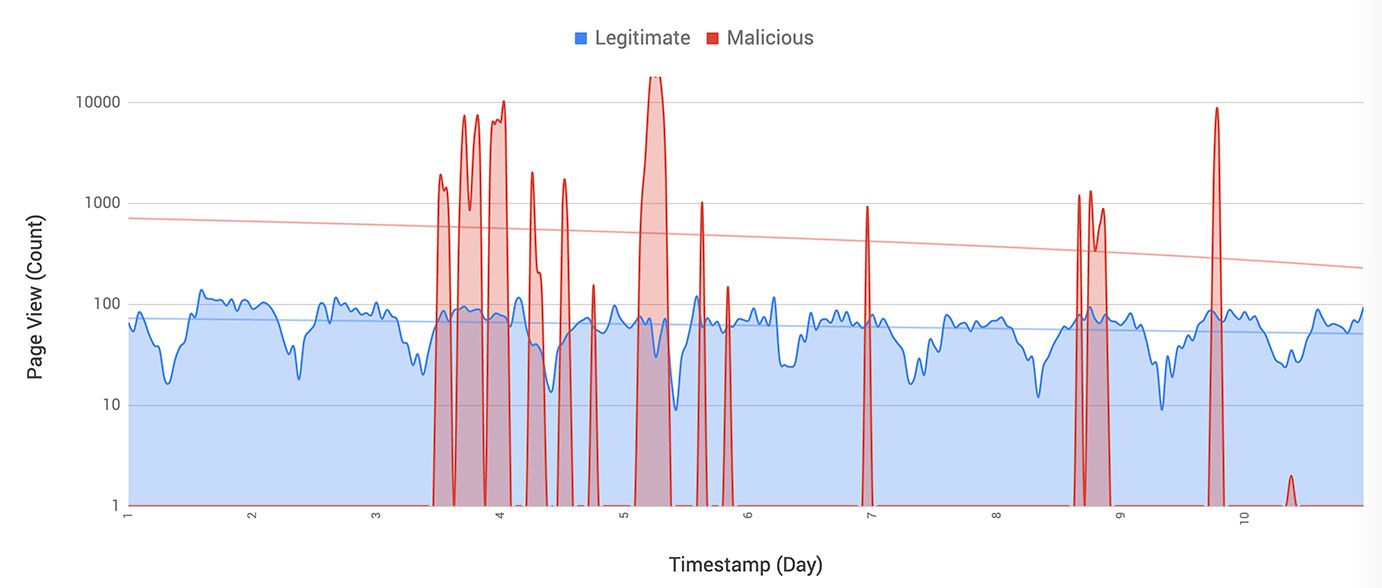
One of the bots detected by the company is called 'Canary.' It was observed in at least two attacks focused on a particular e-commerce platform used by thousands of businesses, the researchers say.
"Malicious bots, like the canary carding bot, increase stolen card validation activity with small-value transactions leading up to the holidays. Canary carding bots explore well-known platforms and test their vulnerabilities to carding attacks to exploit a potentially large number of e-commerce website users."
Researchers were able to detect a Canary bot attack based on technology discrepancies compared to what is normally seen with legitimate users.
A Safari browser version from 2011 changing IP addresses on a daily basis and spawning from cloud and colocation services was the telltale of the attack. Also strange "was not setting the request language and accepted content type."
However, the bot mimicked human behavior by creating a shopping cart, adding products to it, and including shipping information.
A second attack from this bot also relied on cloud services. Changing the IP address and the user agent to impersonate real users with different mobile devices occurred at a faster rate.
Products were added directly to the cart, without checking their pages first, and then jumping to checkout, a pattern inconsistent with typical human behavior.
Taking a shortcut
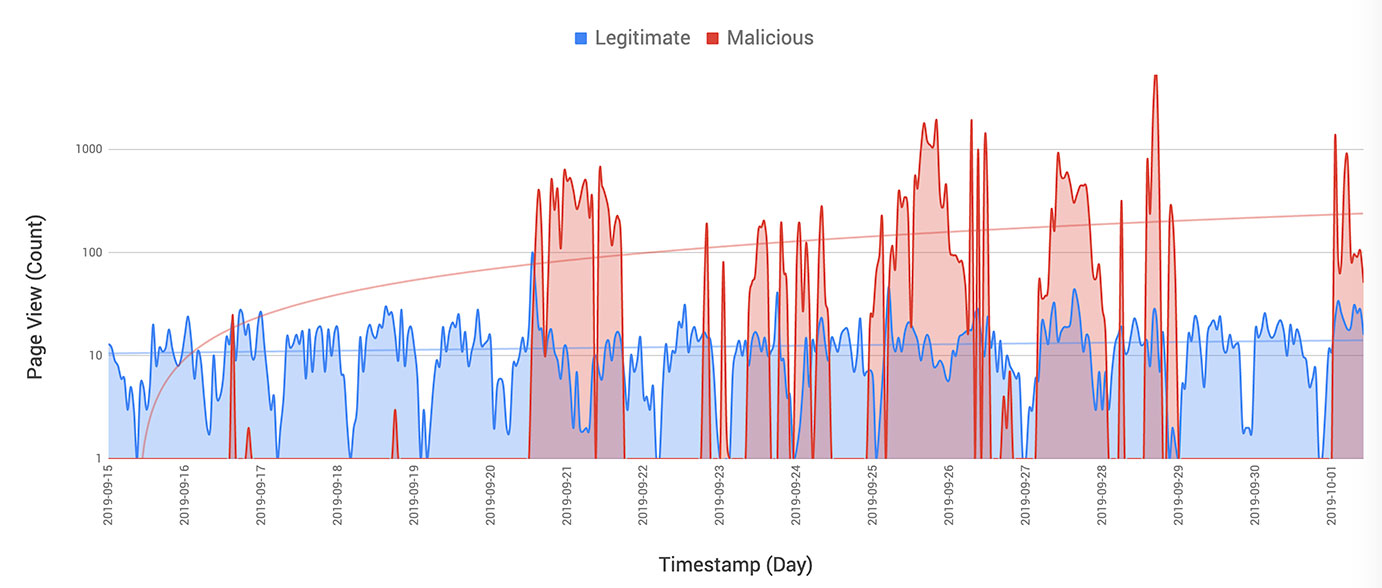
The second carding bot observed by PerimeterX is called 'Shortcut' because it tries to avoid the e-commerce website completely, thus evading detection and mitigation options.
"We have found that in some cases, the attackers are discovering paths with API calls that are unknown to even the website operators. In general, our researchers have seen an increasing trend in API endpoint abuse to validate credit cards on the web and on mobile applications."
This happens when external services handle payments. The third-party service checks the card through an API endpoint and returns an answer. This shortcut allows attackers to reach their goal without interacting with the website.
The method was used with three websites selling apparel, sportswear, and for grocery shopping. In all cases, a single path was used to verify the validity of the stolen cards.
Spotting carding bot activity
Multiple attackers may use the same tools as they have become quite popular for checking the validity of the card data. It is unlikely that these methods will be abandoned any time soon.
Despite attempts to mimic human behavior, the activity of carding bots of today is not too difficult to recognize. Payment attempts with an empty cart is one sign of malicious action as are an increased number of payment authorizations, a higher rate of chargebacks, or a lower than usual average value of the basket.
If these symptoms are backed by a common user agent, IP address, session, or device fingerprint, chances are a carding bot is at work.
One recommendation from PerimeterX is to deny access to the payment page if the cart is empty. While this does not stop all carding bots, it protects against the simpler ones. Stronger defenses should be implemented, though.
.jpg)

Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now