
A decryptor for the STOP Ransomware has been released by Emsisoft and Michael Gillespie that allows you to decrypt files encrypted by 148 variants of the infection for free.
While the decryptor can recover files for 148 variants, it needs to be noted that anyone who was infected after August 2019 cannot be helped with this service. With that said, it may be possible to decrypt using an offline key, so even with these variants there may be some success.
STOP Ransomware
Last month we introduced you to the STOP Ransomware, which is the most widely distributed ransomware that is currently active. This ransomware is distributed by adware bundles that masquerade as software cracks, pirated games (warez), and free software downloads.
When a user installs one of these downloads, their computer will become infested with malicious browser extensions, click fraud trojans, adware, and the STOP Ransomware.
While the exact number of victims is hard to determine, there have been 116,000 submissions to ransomware identification site ID Ransomware related to this infection. This makes it the most submitted family of ransomware on the site followed by the Dharma Ransomware.
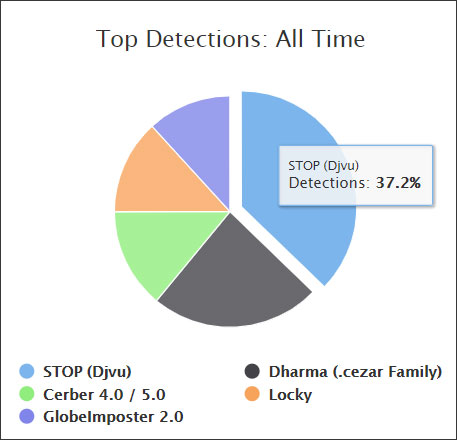
While there are some victims from the United States, most of the victims are from Europe, Asia, South American, and Africa. As expected, there are no victims from Russia, which is most likely due to language checks in the adware bundles.
The release of Emsisoft's STOP Ransomware decryption service is a huge achievement and will be a life saver for both the victims and the helpers on BleepingComputer.
Since the STOP Ransomware was released, this infection has had the most requests for help decrypting files that we have seen since TeslaCrypt. This has led to a monstrous STOP Ransomware support topic at BleepingComputer containing 526 pages of support requests.
Volunteers at BleepingComputer have worked tirelessly trying to help these victims, but in many cases it was in vain. With the release of this decryption service, victims can finally get help in recovering their files.
All support for this decryptor will be handled in the BleepingComputer STOP Support and Help topic, so please post there with any issues. Before posting, be sure to read Emsisoft's Frequently Asked Questions for answers to common questions.
How to decrypt STOP Djvu Ransomware encrypted files
Once again, if your files were encrypted after August 2019, then you are encrypted with a new version that the decryptor does not support and these instructions do not apply. You should instead download the decryptor to see if Emsisoft has been able to gain access to an offline key and if that will help with your files.
If you are using an older variant that you think is supported, before you can decrypt your files with Emsisoft's STOP Djvu Ransomware decryption service, confirm if you were encrypted with a supported extension. The list of supported extensions are:
.shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudet, .tfudeq, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote
If you are infected with the .puma, .pumas, or .pumax extensions of the earlier STOP Ransomware variants, you can skip all of the following steps and instead download the STOP Puma decryptor.
In order to use the service, you first need to find some encrypted files and their originals that match the following requirements and train the decryption service using them.
- Must be the same file before and after encryption
- Must be a different file pair per file type you wish to decrypt
- Must be at least 150KB
To be clear, for each file type (doc, docx, xls, xlsx, png, etc) you want to decrypt, you must also upload an encrypted and unencrypted pair in order to train the service. Once the service is trained with a file type, it can be used to decrypt all files on your computer of that same type.
The best way to find encrypted and unencrypted file pairs are to look for encrypted images or files that were downloaded from the Internet. That way you can download the original location so that you have an unencrypted version.
Once you have a pair of files, go to https://decrypter.emsisoft.com/submit/stopdjvu/ and upload the files using the page's form.
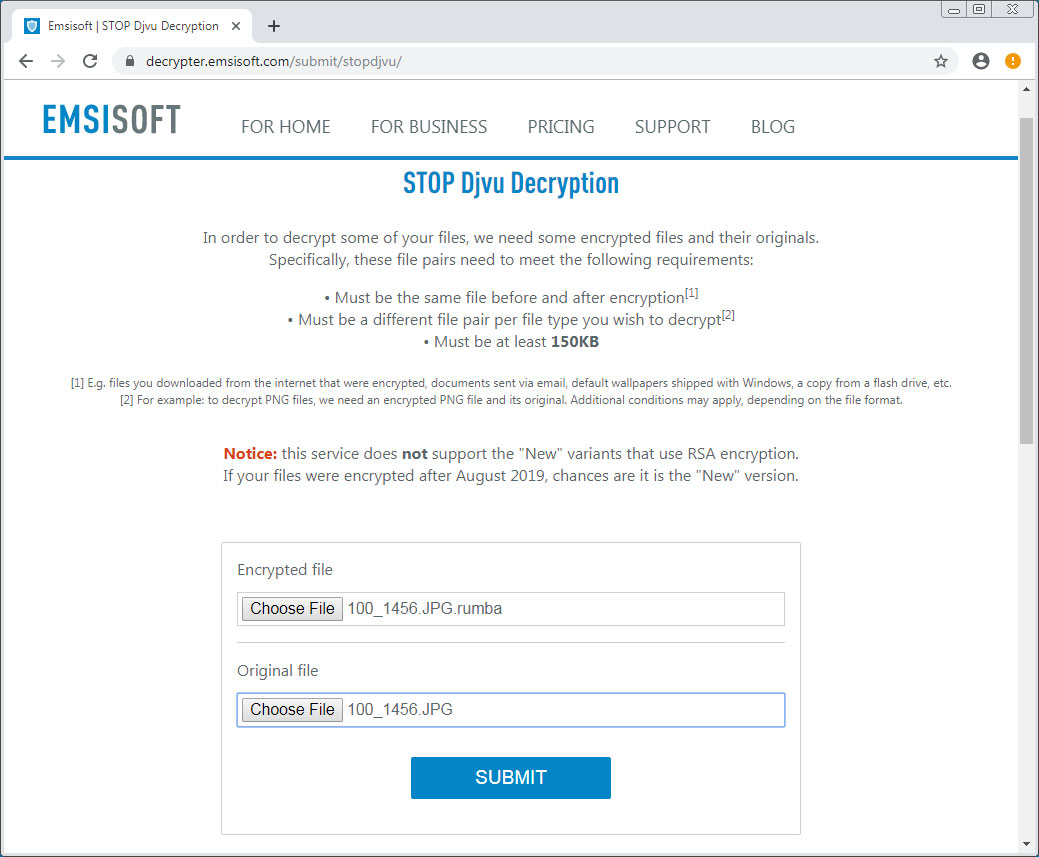
After pressing the SUBMIT button, it will change to a rotating circle to show that it is processing your files. Please be patient at this point as it may take some time to complete.
When done, the service will tell you if the files were properly processed, and if so, will provide a link to the decryptor.
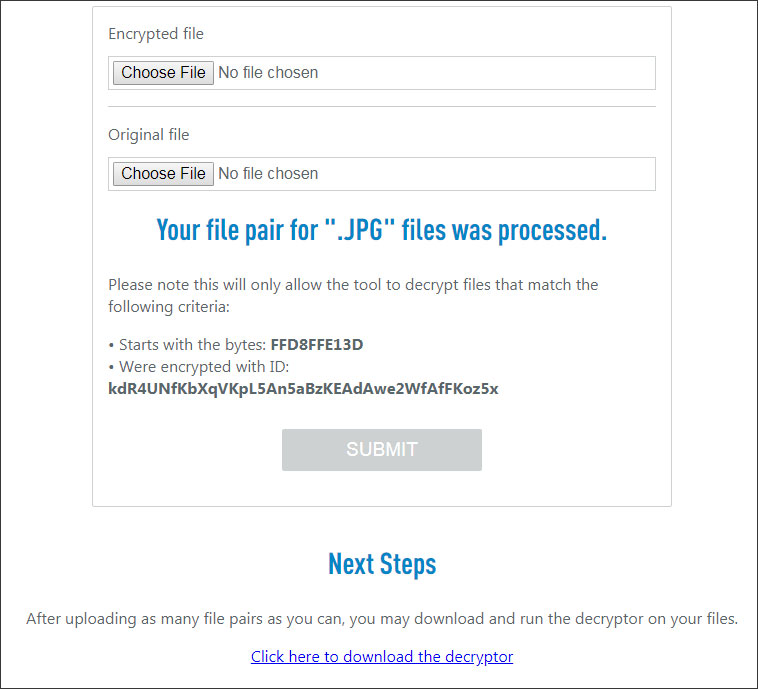
Click on the link to download the STOP Decryptor and then double-click on it to launch the program. As this decryptor requires a working Internet connection, please make sure you are connected before proceeding.
When launching the program, it will display a UAC prompt asking if you would like to allow the program to make changes to your computer. At this prompt, you should click on the Yes button.
A license screen and a small instruction screen will then be displayed. Please read through both of these screens and acknowledge them to continue.
The main decryptor screen will now be displayed with the C:\ drive already selected to be decrypted.
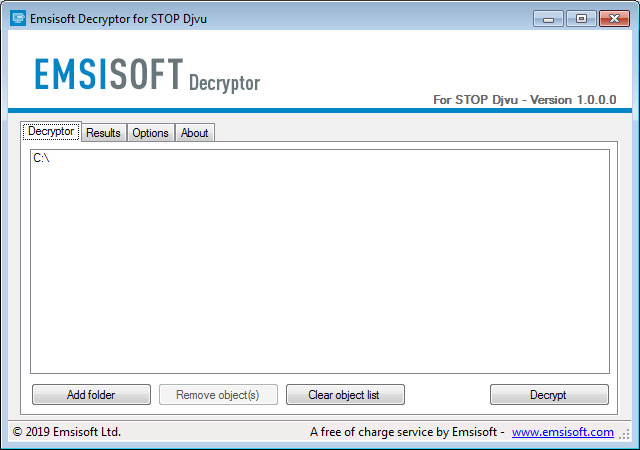
Add the folders you wish to decrypt or go with the default selection of the entire C:\ drive and click on the Decrypt button.
The decryptor will begin to decrypt all file types that you used to train the service.
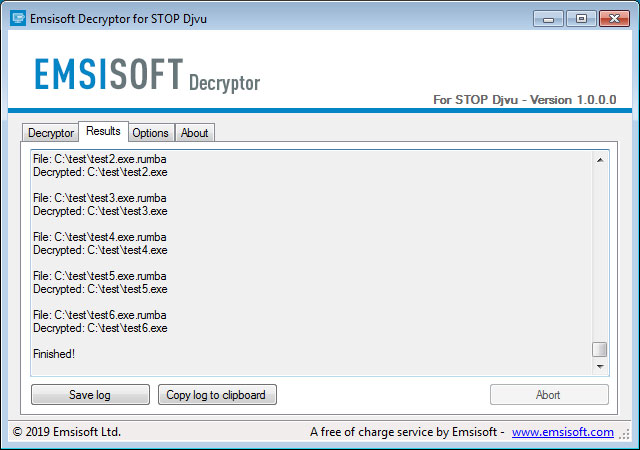
While decrypting, if the decyrptor is unable to decrypt a particular file type, you need to train the service by uploading encrypted and unencrypted pairs of those files. Once you do so, you then click on the Decrypt button again to have it handle that particular file type.
For those who need help getting started using the decryptor, please first read this Frequently Asked Questions and if that does not help, feel free to ask in our STOP Ransomware Support and Help topic.


Comments
cybercynic - 4 years ago
The list of old version supported extensions includes a number of new variant extensions at the end.
Edit: It's been corrected. Great article.
Amigo-A - 4 years ago
I agree, need to add (update!) a complete list of supported extensions. In the new program and on the Emsisoft website there is no such information.
Amigo-A - 4 years ago
Thank you for the article. Just in time!
Mitang - 4 years ago
.peta extension Rensomware Decrepter tool ofline or online
Mitang - 4 years ago
.peta extension Rensomware Decrepter tool ofline or online
HONEY342 - 4 years ago
I m getting following error
Unable to decrypt file with ID: vvcUqAj5YB2BS5IX9qrL1eywKLxNA0KIByGlCpU7
hai85dory - 4 years ago
Hi, the program failed to decrypt my file and i got the follwing error
10419.jpg.ndarod
Error: Unable to decrypt file with ID: vj17sXPslJ3S7AKuSRgTp3vhiAsb78p43AGZL9iV
please Heeeeeeelp
yanvist - 4 years ago
Help My Brother :
File: D:\tes\1952347-1366x768-[DesktopNexus.com].jpg.besub
Error: Unable to decrypt file with ID: 6X3S8WgBkgJRZL0YetoC6qY0qvR2ILHNJayTdMWk
Finished!
ruthay - 4 years ago
I did not see.waiting on this list :( I was hit with it back in April 2018. I'll keep holding on to hope! Yall rock!
GT500 - 4 years ago
Everyone who needs help should either ask in the STOP Ransomware Support Thread on BleepingComputer, or contact Emsisoft directly via their forums or e-mail:
https://www.bleepingcomputer.com/forums/t/671473/stop-ransomware-stop-puma-djvu-promo-drume-help-support-topic/
https://support.emsisoft.com/forum/83-help-my-files-are-encrypted/
https://help.emsisoft.com/en/1916/email/
FluffyCow - 4 years ago
Thank you very much for your work! (.cezor files can be decrypted)
Orika - 4 years ago
Hello
#Help
My computer was infected with ransomware. All files in filename .lokf
Please help. Thank you
Demonslay335 - 4 years ago
New Djvu. Read the FAQ: https://support.emsisoft.com/topic/32045-about-the-stopdjvu-decrypter/
bankhamz - 4 years ago
help me .lokf
File: C:\Users\HP\Pictures\S__107331591.jpg.lokf
Error: Unable to decrypt file with ID: oSK4sJCwHYXheXNQ8q9zCU1ngjEkh8u3TDk8VY1K
please help
Demonslay335 - 4 years ago
New Djvu. Read the FAQ: https://support.emsisoft.com/topic/32045-about-the-stopdjvu-decrypter/
rupan_debnath - 4 years ago
My files got encrypted by ransomware virus. extension is .hets. The txt file contains a personal ID: (which is not the key obviously) 0189jYs9d8TwbCMGuw5Ei5PlymKj0pldFtsUYeGxci3YGlbt1,
I want a tool to decrypt my files. How to go? further the application "decrypt_STOPDjvu" downloaded from site is not getting installed. Don't understand how to install it. It gives error " The application was unable to start correctly (0xc000007b). click OK to close the application.
Don't you think I become helpless? -- Please help.
Demonslay335 - 4 years ago
The decryptor does not install; it is a stand-alone application you just run.
Read the FAQ. If you are having issues just getting the program to run, then it is an issue with your .NET Framework being corrupted or severely outdated.
https://support.emsisoft.com/topic/32045-about-the-stopdjvu-decrypter/
hoanganhtruong77 - 4 years ago
Hello!
All my files have been added .righ and _readme file attached with the content: ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What happens you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-WGsuBCnd3C
Price of private key and decrypt software is $ 980.
Discount 50% available if you contact us first 72 hours, that's price for you is $ 490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
datarestorehelp@firemail.cc
Reserve e-mail address to contact us:
datahelp@iran.ir
Your personal ID:
0190Asd374y5iuhldhyvYOS8IRH3tB2Ql3HofBtjKCe7U5XdVNaOrpOc3
Please support me!
_alena - 4 years ago
same here, my pc infected at 5pm 7/12/2019 all file goes to .righ files LOL
_alena - 4 years ago
0190Asd374y5iuhldwbSRsMKomPauAIeKj7CaTQpuoYHB60Y6JLAhL5D0
Nadar - 4 years ago
Hi, the program failed to decrypt my file and i got the follwing error
Unable to decrypt file with ID: woQlAJQXqTcUWExHL7PhjpeXOztekzTPlsBXt8dv
Please help me out
Rmasput - 4 years ago
Hai,
Starting...
File: C:\Users\R. Masput\Documents\apple.txt.hets
Error: Unable to decrypt file with ID: QiXDMGBveMMkHdyEtSAkTZIotCca0j0l3tH4AhAc
File: C:\Users\R. Masput\Documents\d439d980e376baba6373df8edad072a6.jpg.hets
Error: Unable to decrypt file with ID: QiXDMGBveMMkHdyEtSAkTZIotCca0j0l3tH4AhAc
Please help me!
Demonslay335 - 4 years ago
You have New Djvu, read the FAQ... we cannot help you.
https://support.emsisoft.com/topic/32045-about-the-stopdjvu-decrypter/
R-K - 4 years ago
Those international ransomware cyberterrorists must be living in Russia.
UPI - 4 years ago
For unsupported variants or any other ransomware that only encrypts part of the file JPEG-Repair can help repair JPEGs. An intact reference file is required. In short JPEG-repair allows you to merge the image data from the JPEG that was not encrypted with the header of the valid reference file. This video shows the repair process: https://youtu.be/k7KB7uUoOrU, the blog post is here: https://www.disktuna.com/repairing-jpegs-encrypted-by-ransomware-stop-djvu/
rfrodrigo - 4 years ago
Hi, can you help me? All my files were encrypted by ransomware with extension name: ".adame".
Thank you.
Demonslay335 - 4 years ago
No. That is Dharma; not decryptable.
Rolando20202020 - 4 years ago
HOLA A TODOS SOY NUEVO UN VIRUS ME ATACO Y TODOS MIS ARCHIVOS TIENEN LA EXTENSION (NPSK) ALGUIEN ME PODRIA AYUDAR? SALUDOS...
Roiz - 4 years ago
Hola buenos dias me podrian ayudar no me funciona con la extension PDFF ya he intentado de todo porfavor de su ayuda
Wilodan - 4 years ago
Hola por favor necesito su ayuda mi PC se infecto con un virus Ransomware la extensión es .opqz y no puedo abrir ningún documento mil gracias saludos.
ninovisk - 4 years ago
Hello
#Help
My computer was infected with ransomware.
All files in filename .PIDON
Please, I NEED HELP!
ninovisk - 4 years ago
Hello, i,m from Brazil and use google translator, please!
#Help
My computer was infected with ransomware.
All files in filename .PIDON
Please, I NEED HELP!
Demonslay335 - 4 years ago
Follow the instructions in the article... you need to provide encrypted/original file pairs in order to decrypt your other files of the same type.
ninovisk - 4 years ago
where can i send these files? my hd is still saved with the hope of a way to get them back.
Thanks!
Demonslay335 - 4 years ago
Literally... read the article. The instructions are very clear what to do and where to go...
TrungTo - 3 years ago
Hello any one know ransomware .mzlq and how recover data ( all Jpeg and JPG )
leonardo3898 - 3 years ago
File: E:\Alexis\Universidad\2do Año\Maquinaria\Arado de mancera-tipos de arados.pdf.usam
No key for New Variant online ID: D7aoaM418lIVxiUTO4UUVNwLjIbBOaQF3hHg65d9
Notice: this ID appears to be an online ID, decryption is impossible
me salio este error ademas que muchos de estos estan en terminacion .USAM
setyo108 - 3 years ago
help me
File: D:\1x\Asset 2.png.maas
No key for New Variant online ID: 4rw0eC8T1cKj1GC5wk3UOnePPpNaSY9oEIMDReru
Notice: this ID appears to be an online ID, decryption is impossible
Micho135 - 3 years ago
Hi folks. Thanks for you good job on helping affected users, like me in this case. I got the ".VARI" ransomware, which seems to be new. At time of decryptong with STOP/DJVU I got this mesage:
No key for New Variant online ID: xlfeKKv6B4FJVImCXTavL4FdkkKOctulsHWzcNK3
Notice: this ID appears to be an online ID, decryption is impossible
I could rename a .TXT.VARI file and found inside the online ID and then some Hexadecimal numbers between {} Could this be the Key for decryption? How the key look likes and how I can use it. Than in advance
Demonslay335 - 3 years ago
That's just the filemarker the malware uses to identify whether it has encrypted that file already. It's the same for everyone since the first versions. It has nothing to do with the key... your key is an RSA private key that only the criminals have on their servers.
CarlosLizandro - 3 years ago
What can I do for this?
Error: Unable to decrypt Old Variant ID: QRVBhUIDcq20zoqRYQI49PQ1I0u5qW0VH81ZjIIL
First 5 bytes: 255044462D
Demonslay335 - 3 years ago
Read the article and FAQ... the decryptor can only decrypt files with the same first 5 bytes as what you have supplied it. To decrypt PDFs, you have to provide the site with an encrypted PDF and its original.
CarlosLizandro - 3 years ago
"Read the article and FAQ... the decryptor can only decrypt files with the same first 5 bytes as what you have supplied it. To decrypt PDFs, you have to provide the site with an encrypted PDF and its original."
But how can I obtein the original file?, if they are encrypted?
diditzaja - 3 years ago
All your files have been encrypted with MARS Virus.
Your unique id: 3F393ECDA3C94C76AE1100E0103D64D2
Our virus encrypted 12590 of your office files (xls, xlsx, doc, docx, ppt, pptx, odt, ods, pdf, dwg, psd, dbf, fpt, php, cdr, mdb, accdb).
You can buy decryption for 1 000$ in Bitcoins.
But before you pay, you can make sure that we can really decrypt any of your files.
The encryption key and ID are unique to your computer, so you are guaranteed to be able to return your files.
To do this:
1) Send your unique id 3F393ECDA3C94C76AE1100E0103D64D2 and max 3 files for test decryption to mars_dec@outlook.com or anton_ivan_8989@mail.ru
2) After decryption, we will send you the decrypted files and a unique bitcoin wallet for payment.
3) Be careful! Fakes are possible in Telegram, never pay until you receive test files after decryption!
4) After payment ransom for Bitcoin, we will send you a decryption program and instructions. If we can decrypt your files, we have no reason to deceive you after payment.
or do this(If you have not received a reply by email):
1) Download and install Telegram Messanger: https://desktop.telegram.org/ (for Windows, Linux, macOS)
2) Find user mars_dec
3) Send your unique id 3F393ECDA3C94C76AE1100E0103D64D2 and max 3 files for test decryption.
4) After decryption, we will send you the decrypted files and a unique bitcoin wallet for payment.
5) Be careful! Fakes are possible in Telegram, never pay until you receive test files after decryption!
6) After payment ransom for Bitcoin, we will send you a decryption program and instructions. If we can decrypt your files, we have no reason to deceive you after payment.
FAQ:
Can I get a discount?
No. The ransom amount is calculated based on the number of encrypted office files and discounts are not provided. All such messages will be automatically ignored. If you really only want some of the files, zip them and upload them somewhere. We will decode them for the price of 1 file = 1$.
What is Bitcoin?
read bitcoin.org
Where to buy bitcoins?
https://bitcoin.org/en/buy
https://buy.moonpay.io
or use google.com
Where is the guarantee that I will receive my files back?
The very fact that we can decrypt your random files is a guarantee. It makes no sense for us to deceive you.
How quickly will I receive the key and decryption program after payment?
As a rule, within a few hours, but very rarely there may be a delay of 1-2 days.
How does the decryption program work?
It's simple. You need to copy the key and select a folder to decrypt. The program will automatically decrypt all encrypted files in this folder and its subfolders.
I will complain about your Telegram account and mailbox's..
God help you. You won't find us anyway. But many people will be deprived of any opportunity to recover their files.
please help me(
junior_hardware - 3 years ago
It was three days ago that I had my computer attacked by the .igdm ransomeware and all my files are hijacked, however, I have already done several researches and methods to break the .igdm encryption, but without success. Has anyone here ever held their files hostage to the .igdm ransomeware and managed to break its encryption?
Demonslay335 - 3 years ago
You're not going to break it. It is cryptographically secure. Anyone claiming to break the encryption is a scammer; there are dozens of them out there.
zakizac - 2 years ago
i have .djvu variant , i submitted many .jpeg and .mov files in the portal but i could decrypt just 35% of my files , why other pictures and videos with the same extension are not decrypted ? (5 first bit maybe ?)
zakizac - 2 years ago
i have .djvu variant , i submitted many .jpeg and .mov files in the portal but i could decrypt just 35% of my files , why other pictures and videos with the same extension are not decrypted ? (5 first bit maybe ?)
hosseinhm11 - 1 year ago
help me
.truke
Your personal ID:
105ASdiuew74yiljfgdRuZtojFDVoy0Y1BLwyqQh5VHQxkuH6yhTvNBqQZ4
joseegs29 - 1 year ago
<p>hola, podrían ayudarme por favor, estoy desesperado, perdì información muy valiosa mis imágenes y videos están encriptados con la terminación (.kruu) espero puedan ayudarme, muchas gracias</p>
<p>Translated to English: </p>
<pre class="tw-data-text tw-ta tw-text-large" data-placeholder="Translation" dir="ltr" id="tw-target-text" style="text-align:left">
<span class="Y2IQFc" lang="en">Hello, could you please help me, I am desperate, I lost very valuable information, my images and videos are encrypted with the ending (.kruu) I hope you can help me, thank you very much</span></pre>
Naing - 1 month ago
my pc attack .ldhy ransomware
please decryptor help me?
Your personal ID:
0849ASdw0yWTYD4t9BDgknYGG6ux40MNNhGqJ2u95uq4xtPF