
Image: Julian Hochgesang
Updated malware implants and a new backdoor named Okrum connected with the Ke3chang threat group operating from China have been found by ESET researchers while monitoring their operations between 2015 and 2019.
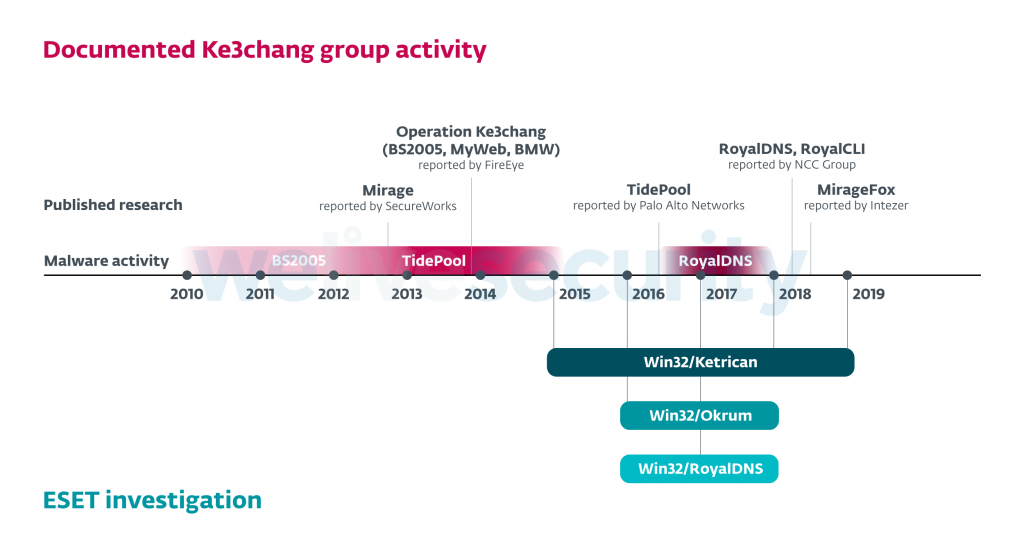
The cyber-espionage activities of the Ke3chang advanced persistent threat (APT) group (also known as Vixen Panda, Royal APT, Playful Dragon, and APT15) span over almost a decade, going as far as 2010 according to FireEye researchers.
The hacking group's main targets are entities from the oil industry and military, government contractors, as well as European diplomatic missions and organizations.
Ke3chang group activity
Ke3chang is known to have operated multiple campaign cyber-espionage campaigns, with one of them active from 2012 to 2015 having used a RAT-like malware dubbed TidePool which allowed the hacking group to collect info on its targets after exploiting the CVE-2015-2545 Microsoft Office vulnerability.
From 2016 to 2017, Ke3chang employed the RoyalCLI and RoyalDNS backdoors as part of campaigns targeting the UK government, attempting to steal military tech and governmental info as discovered by NCC Group's Incident Response team.
During 2018, Ke3chang started using yet another implant, the malware variant of the Mirage Remote Access Trojan (RAT) known under the name of MirageFox.
Ke3chang's new Okrum backdoor
The Okrum backdoor was first observed during December 2016, with ESET's telemetry data further recording it in action during attacks against "diplomatic missions in Slovakia, Belgium, Chile, Guatemala and Brazil throughout 2017."
Targeted machines are infected with the Okrum malware using a constantly changing architecture featuring multiple stages and components, with an installer component that loads one of the two loaders being used to drop the backdoor embedded within a PNG image file to avoid detection.
"The functionality of the Okrum backdoor is not unlike the other backdoors operated by the Ke3chang group The commands allow the attackers to download and upload files, execute binaries or run shell commands," ESET's researchers found. "The backdoor can also update itself to a newer version and can adjust the time it sleeps after each backdoor command."
After being succesfully dropped on a target's computer, the Okrum implant can gain admin right by calling the ImpersonateLoggedOnUser API and it will start collecting computer info such as computer name, user name, host IP address, primary DNS suffix value, OS version, build number, and architecture.
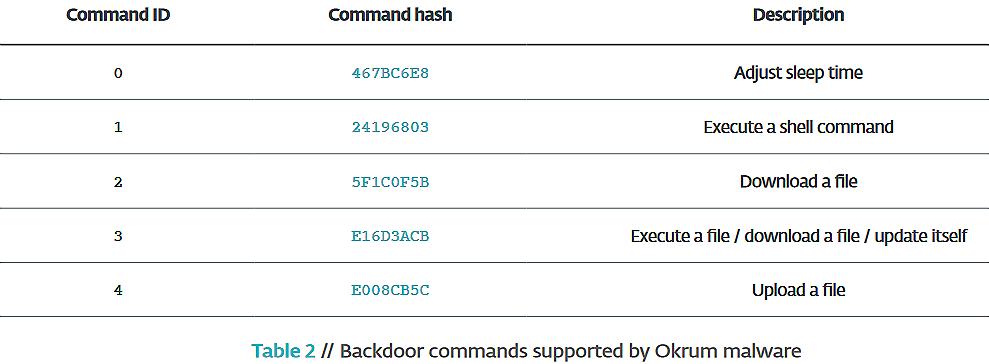
This data is sent to its command and control (C2) server to register the compromised machine in the attacker's database and it subsequently "starts a loop in which the compromised computer queries for a backdoor command and then interprets it locally."
Okrum will also send a campaign name to its C2 server to allow the operators to keep track of the multiple operations they're coordinating, with three monikers (i.e., finance, green7, and rehake) having been used by the samples analyzed by ESET.
"The Okrum backdoor supports only basic commands, which indicates it is either a first-stage backdoor, or, more likely, the malware operators execute more complicated commands manually," as detailed by ESET's white paper, a known technique used by APT15 during their attacks as per reports from NCC Group and Intezer Labs researchers.
After getting a foothold on a victim's system, the Ke3chang actors will use and abuse a wide variety of other tools to achieve their goals, from password dumpers and network sessions enumerators to keyloggers.
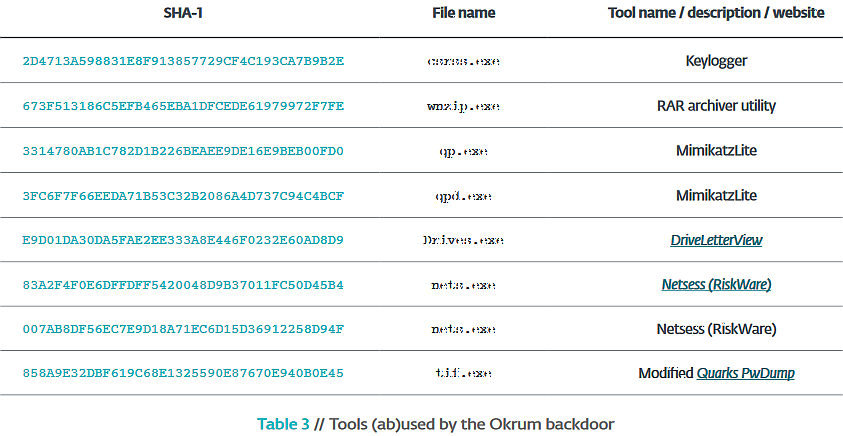
"Similar utilities were observed being used by other Ke3chang malware, which is described in the next section. For example, a Ketrican backdoor from 2017 used NetSess, NetE, ProcDump, PsExec, RAR archiver utility, and Get-PassHashes," explains the ESET research team.
The Ketrican backdoors
While observing the activities of the Ke3chang group in 2015, ESET's researchers also detected malware related to the BS2005 backdoors found by FireEye researchers while analyzing operation Ke3chang and to the TidePool malware seen by Palo Alto Networks' Unit 42 in 2016.
"We started connecting the dots when we discovered that the Okrum backdoor was used to drop a Ketrican backdoor, freshly compiled in 2017," says ESET. During the same year, the Ke3chang APT group also used updated versions of the RoyalDNS malware.
Updated versions of the Ketrican backdoor with some code improvements were used again during 2018 and 2019, targeting the same type of organizations from the years before.
All the Ketrican, Okrum, and RoyalDNS backdoors detected by ESET after 2015 are closely related to previous Ke3chang group activity, with the most prominent connections being that:
• Ketrican backdoors from 2015, 2017, 2018 and 2019 have all evolved from malware used in Operation Ke3chang
• The RoyalDNS backdoor detected by ESET in 2017 is similar to the RoyalDNS backdoor used in previously reported attacks
• Okrum is linked to Ketrican backdoors in that it was used to drop a Ketrican backdoor compiled in 2017
• Okrum, Ketrican and RoyalDNS target the same type of organizations; some of the entities affected by Okrum were also targeted with one or more of Ketrican/RoyalDNS backdoors
• Okrum has a similar modus operandi as previously documented Ke3chang malware – it is equipped with a basic set of backdoor commands and relies on manually typing shell commands and executing external tools for most of its malicious activity
"We started connecting the dots when we discovered that the Okrum backdoor was used to drop a Ketrican backdoor, compiled in 2017. On top of that, we found that some diplomatic entities that were affected by the Okrum malware and the 2015 Ketrican backdoors were also affected by 2017 Ketrican backdoors,” says ESET's Zuzana Hromcova, the researcher behind the discoveries. "The group remains active in 2019 – in March, we detected a new Ketrican sample."
ESET's research team provides a list of MITRE ATT&CK techniques at the end of their Ke3chang report and indicators of compromise (IOCs) as part of the OKRUM AND KETRICAN whitepaper, including malware sample SHA-1 hashes, and C2 server domains for the Ketrican, Okrum, and RoyalDNS backdoors.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now