
Researchers unearthed a new and highly prolific malware framework used by its creators to generate over one billion fraudulent ad impressions over a time span of just three months.
The attackers used the framework as part of three different ad fraud techniques for boosting their Google AdSense revenue with the help of a malicious browser extension which would produce AdSense impressions out of thin air, while also stealthily watching Twitch streams and generating fake YouTube likes in the background.
"The framework is designed to pad statistics on social sites and ad impressions, creating revenue for its operators who are using a botnet to attack the content and advertising platforms by spreading the malware and targeting browsers including Google Chrome, Mozilla Firefox, and Yandex’s browser," found the Flashpoint researchers who discovered the ad fraud framework.
Malicious extension deployment
Victims' web browsers are infected using a multi-stage approach, starting with an "Installer" module that will set up and configure the malicious browser add-on and achieve persistence on the targets' computer using a scheduled task.
In the next stage, another framework module named "Finder" will start collecting the victim's browser cookies and credentials, sending them to its masters' command and control infrastructure as ZIP archives.
This is the module that will also communicate with a secondary C2 server that will send in the frequency to be used for collecting and exfiltrating data from the infected web browsers.
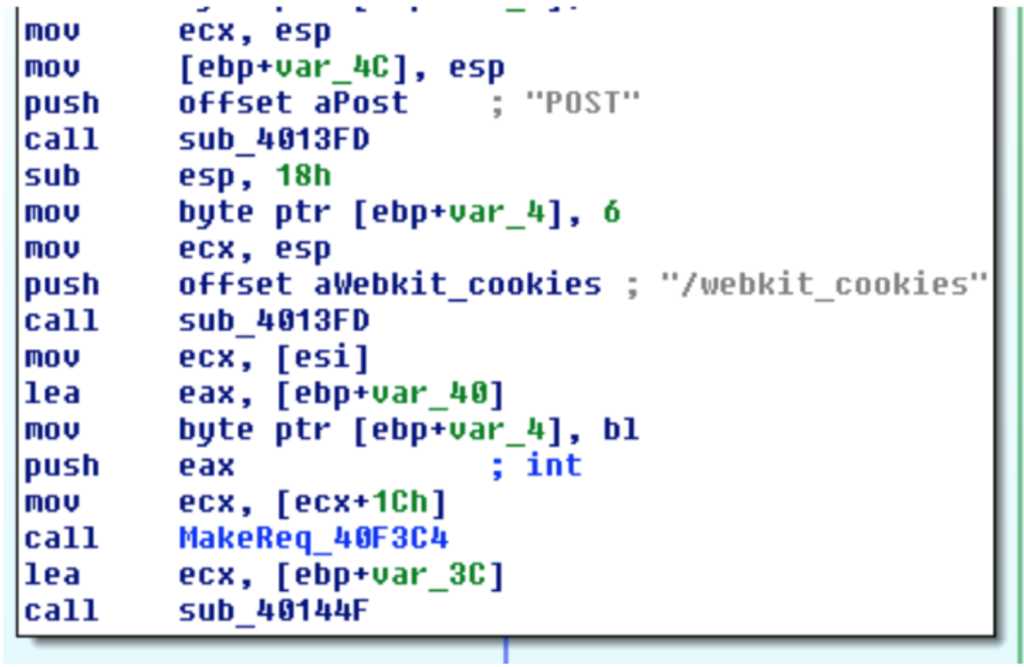
A third malware framework module is used by the attackers dubbed "Patcher" was also used to install the malicious browser extension by an early version of the ad fraud framework, with latest versions having bundled it with the Installer module.
"The extension is essentially set up to inject scripts into web pages, which will then handle further functionality depending on the page," says Flashpoint.
Malicious ad fraud framework capabilities
After the browser is successfully compromised by installing the framework's extension, it will immediately start generating web traffic and injecting ads within the websites visited by its victims.
The malicious add-on is also used by its operators to inject several script variants designed to hunt down and replace ad-related code on web pages, as well as report ad clicks and various other types of data to its C2 servers.
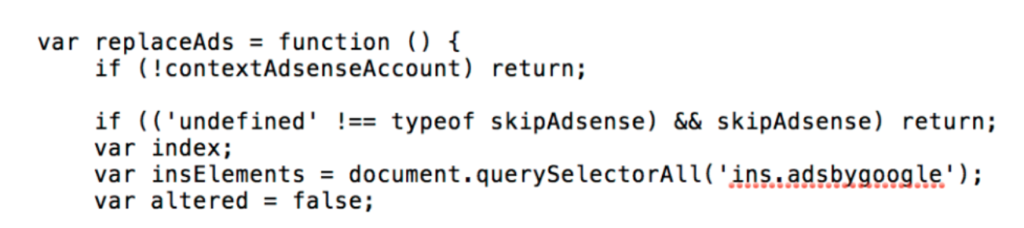
However, the framework will also make sure that it doesn't mess with Google domains, as well as several porn and Russian websites, checking a built-in blacklist for sites where injecting scripts and ads should be avoided to evade detection.
The malicious activity surrounding this fraudulent AdSense campaign is focused on a handful of countries, with Russia, Ukraine, and Kazakhstan being the most prominent examples.
The backend of the botnet created using this ad fraud-focused malware framework uses a massive database that will cycle the data sent by the bots to the C2 infrastructure, getting rid of the old — potentially no longer useful — collected data to make space for fresher cookies and newly stolen credentials.
"The data is stored for a few months before being wiped or reset. A number of views are set up revolving around generating statistics on the bots and their activities," found the Flashpoint researchers.

The Flashpoint research team provides a full list of indicators of compromise (IOCs) in CSV and MISP JSON formats, including SHA256 hashes for over 1400 malware samples, as well as eight of the domains used in the AdSense fraud campaign and Snort rules designed to detect related malicious activity.
During January, two sets of fake Android apps [1, 2] with over 17 million installs found on Google's Play Store were found to flood their users' devices with highly intrusive full-screen adverts whenever the user unlocked the device or every 15/30 minutes.
These apps, signed using different codesign certificates and published under different developer names, also hid from view not allowing the victims to uninstall them while displaying ads programmatically on the infected Android devices.
Another mobile click-fraud campaign from December 2018 made use of 22 Android apps to trick advertisers into paying the operators the higher advertising price that came with displaying the ads on Apple's iPhone 5 to 8 Plus devices.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now