
The frequency of business email compromise (BEC) scams has increased year over year and so did the value of attempted thefts, reaching a monthly average of more than $300 million.
The number is drawn from the suspicious activity reports (SARs) received every month since 2016, which increased from 500 to more than 1,100 in 2018.
The Financial Crimes Enforcement Network (FinCEN) compiled statistics about BEC incidents occurring over the past two years and identified the most common types of targets along with the destination intended for the stolen funds and the techniques used by the scammers.
The latest report from Internet Crime Report from FBI's Internet Crime Complaint Center (IC3) informs BEC scams were responsible for most of the losses generated by cybercrime.
Companies lost $1.2 billion to this sort of cybercriminal activity that aims to obtain funds by posing as a customer or upper management personnel in a company in order to trick key individuals in the organization into wiring funds to an attacker-control bank account.
Statistics are dire
FinCEN's analysis describes the broader picture of BEC scams stating that while scammers tried to steal in 2016 an average of $110 million per month the value in 2018 grew to $301 million.
According to these numbers, last year alone cybercriminals endeavored to rob companies of more than $3.6 billion.
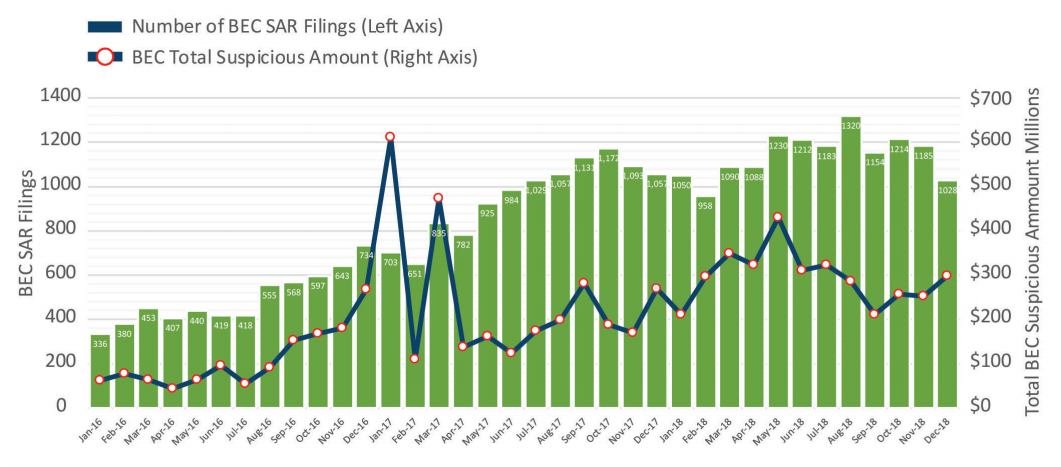
"In 2016, financial institutions filed nearly 6,000 BEC-related SARs with an average transaction total of $110 million per month. In 2017, the number of BEC-related SARs increased to over 11,000 with a monthly average of $241 million. In 2018, the number of BEC-related SARs rose to nearly 14,000 filings, averaging $301 million in suspicious transactions per month" - FinCEN
Most common victims
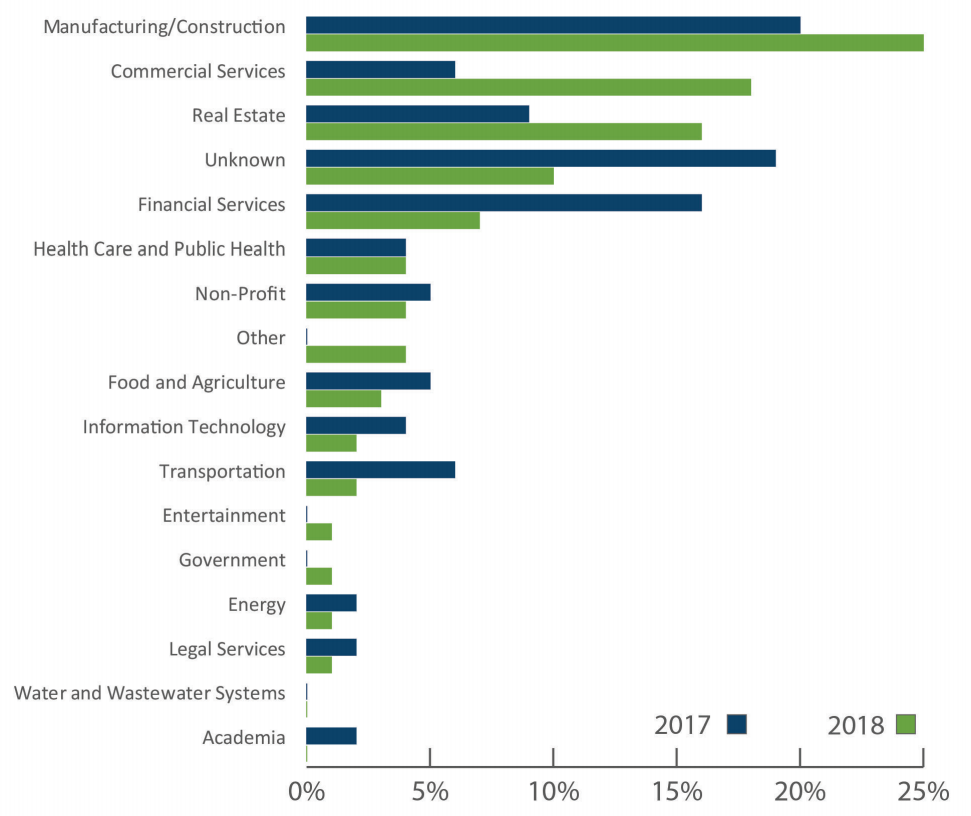
The organization's assessment shows that companies in the manufacturing or construction business were the most frequent targets of email account compromise attacks, accounting for 25% of the victims.
Commercial entities offering professional services like landscaping, retail, restaurants, and lodging became more attractive targets, with 18% of the attacks being aimed at them.
Unlike financial organizations, which fell in the rankings from 16% to 9%, real estate firms turned out to be more tempting, representing 16% of the BEC scam victim pie.
Most of the wire transfers from BEC fraud are domestic, FinCEN observed. In 73% of the cases the beneficiary is in the U.S. and only 27% of the transactions have a foreign destination.
This does not mean that the majority of the threat actors are US-based. These figures likely reflect the fact that cybercriminals use money mules to withdraw the money, which is later distributed across the cybercriminal network and typically ends up abroad.
Top BEC methods
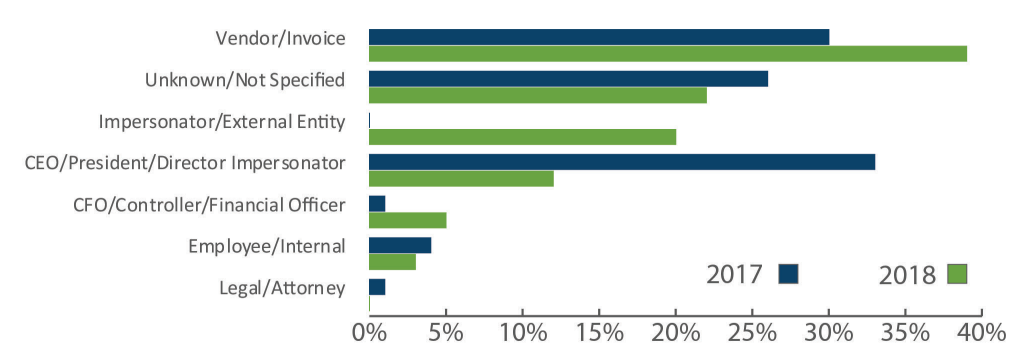
Crooks have different tactics to attain their goal. In 2017 they used to impersonate company CEOs, which have sufficient authority to instruct individuals in charge of making payments to wire money to a specific account.
This approach dropped from 33% to 12% in 2018, indicating that fraudsters are adapting and looking for new ways to play their tricks.
Last year they seemed to prefer impersonating customers and vendors, and used fake invoices in an attempt to get paid. They are also adjusting the sums according to the industry sector tackled.
"The average transaction amount for BECs impersonating a vendor or client invoice was $125,439, compared with $50,373 for impersonating a CEO" - FinCEN
One example in the report is of a Lithuanian man who used fake invoices to defraud multinational companies of at least $100 million; the money was wired to overseas accounts he controlled.
Although the instructions for transferring the money are done over email, scammers need to prepare the message so that it does not raise any suspicions.
For this, they rely on various malware designed to steal the necessary info for perpetrating the attack. Spyware is the common threat as it steals the data necessary to break into email accounts.
However, the trend seems to change. Nigerian fraudsters, who are skilled in the scamming business, started to shift to remote access tools that provide a higher set of capabilities.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now