
If you read the news, it's hard not to see that ransomware is far from dead and may be worse then ever.
Emboldened by large government payouts, ransomware developers are increasingly targeting cities, the enterprise, and charities where they can create large scale damage and thus potentially large-scale ransom payments.
It is no longer a playing field swamped with small players. While the smaller variants do exist, attackers are now performing more targeted attacks than ever with tried-and-true ransomware variants.
mayors
Organizations, colleges, charities, and local government need to make sure they have good backup policies in place, provide adequate phishing training, and secure their perimeter by removing remotely accessible remote desktop services.
Contributors and those who provided new ransomware information and stories this week include: @FourOctets, @Seifreed, @jorntvdw, @PolarToffee, @malwareforme, @struppigel, @DanielGallagher, @LawrenceAbrams, @demonslay335, @malwrhunterteam, @BleepinComputer, @fwosar, @Amigo_A, @State_Scoop, @Anomali, @IntezerLabs, @VirITeXplorer, @nao_sec, @petrovic082, @360TotalSec, @jeromesegura, @briankrebs, and @GrujaRS.
July 6th 2019
New .crash Dharma variant
Michael Gillespie found a new Dharma ransomware variant that appends the .crash extension.
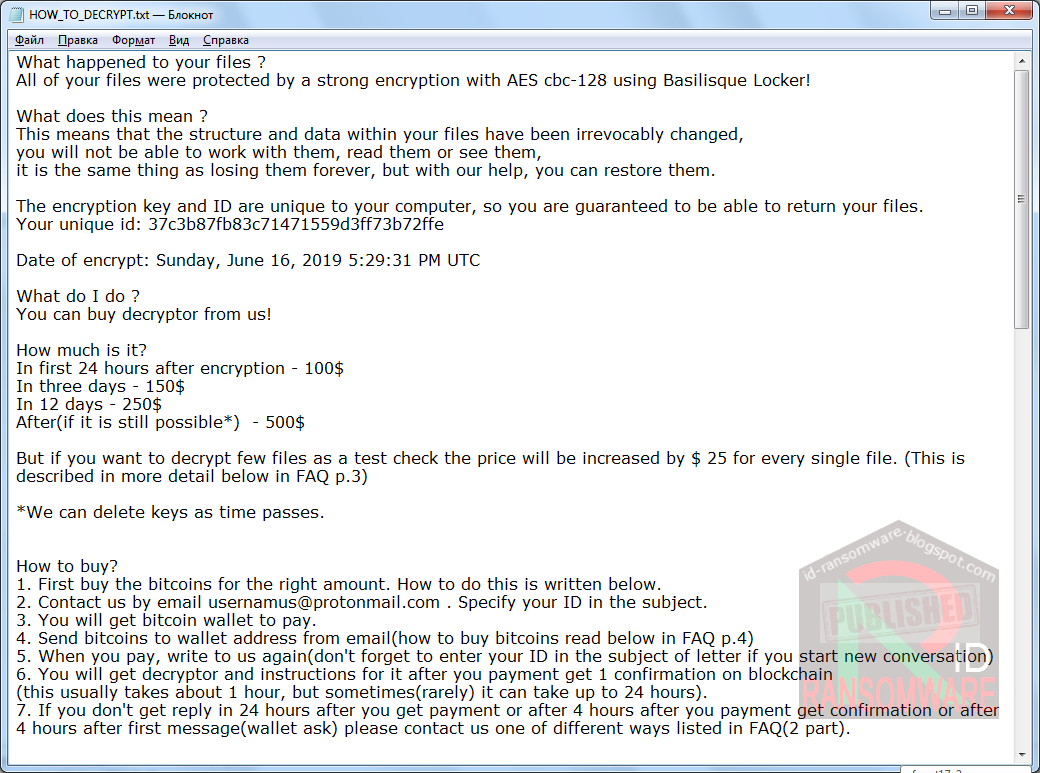
New Basilisque Locker discovered
Amigo-A found a new ransomware called Basilisque Locker that appends the .basilisque@protonmail_com extension and drops a ransom note named HOW_TO_DECRYPT.txt.
July 7th 2019
A City Paid a Hefty Ransom to Hackers. But Its Pains Are Far From Over.
More than 100 years’ worth of municipal records, from ordinances to meeting minutes to resolutions and City Council agendas, have been locked in cyberspace for nearly a month, hijacked by unidentified hackers who encrypted the city’s computer system sand demanded more than $460,000 in ransom.
New .php and .dqb Dharma variants
Jakub Kroustek found new Dharma variants that append the .php and.dqb extensions.
July 8th 2019
New .save Dharma variant
Jakub Kroustek found new a Dharma variant that append the .save extension.
New .kick Dharma variant
Michael Gillespie found a new Dharma ransomware variant that appends the .kick extension.
New GarrantyDecrypt variant
Michael Gillespie found a new GarrantyDecrypt Ransomware variant that appends the .popoticus extension.
New .lokas STOP Djvu variant
Michael Gillespie found a new STOP Djvu variant that appends the .lokas extension to encrypted files.
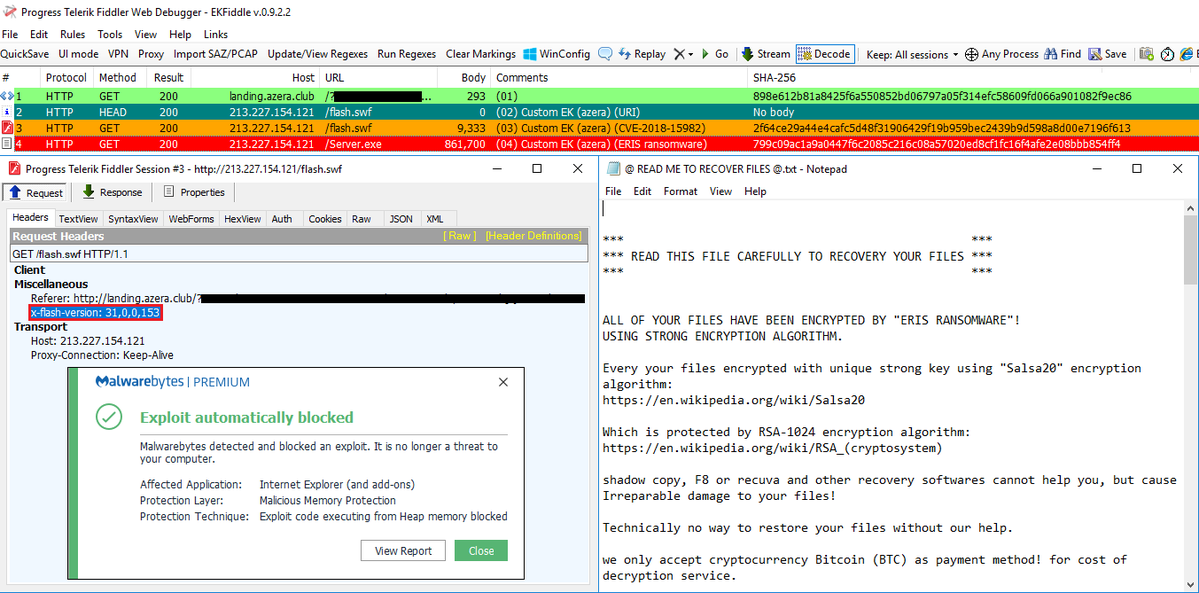
Custom exploit kit pushing the ERIS Ransomware
Jérôme Segura found a custom exploit called Azera pushing the ERIS Ransomware.
Who’s Behind the GandCrab Ransomware?
The crooks behind an affiliate program that paid cybercriminals to install the destructive and wildly successful GandCrab ransomware strain announced on May 31, 2019 they were terminating the program after allegedly having earned more than $2 billion in extortion payouts from victims. What follows is a deep dive into who may be responsible for recruiting new members to help spread the contagion.
July 9th 2019
Rig Exploit Kit Pushing Eris Ransomware in Drive-by Downloads
The RIG exploit kit has been spotted distributing the new ERIS Ransomware as its payload. Using the RIG exploit kit, vulnerable victims will find that the ransomware is installed on their computer without their knowledge simply by visiting a web site.
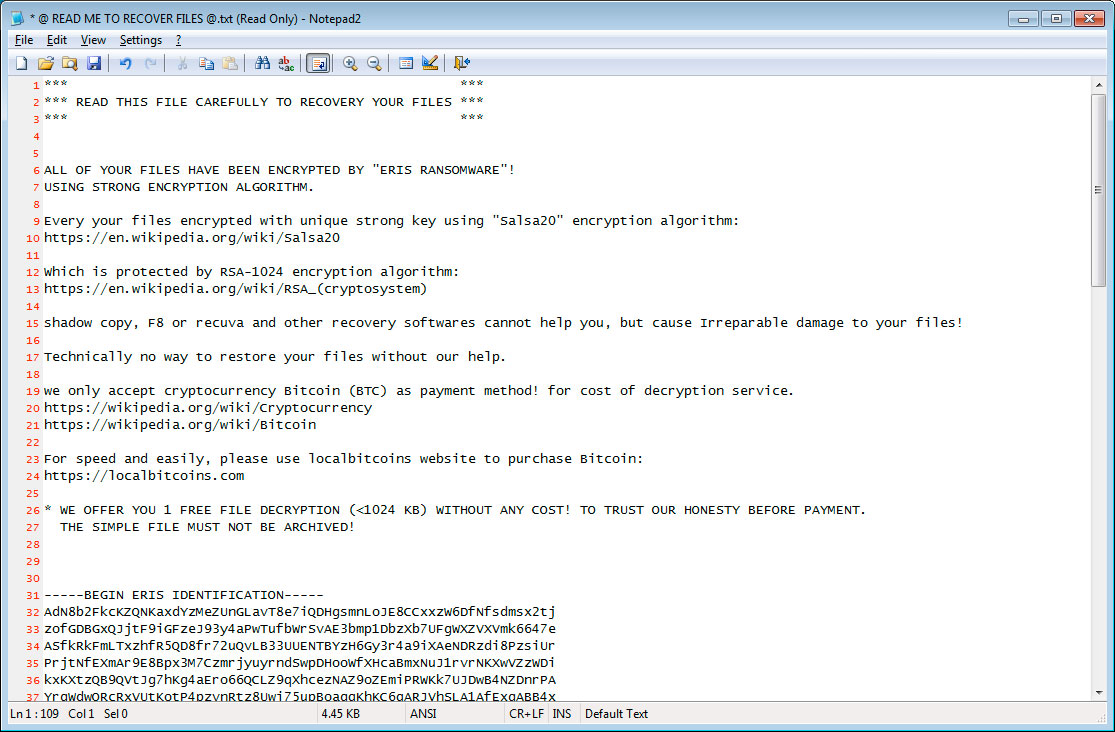
Ransomware REvil - Sodinokibi: Technical analysis and Threat Intelligence Report
The authors of Sodinokibi ransomware, even if they are the first versions of their creation, seem to have a long experience in this threats of cyber-crime.
Some researchers have identified the similarities with GandCrab ransomware, whose project was shut down in beginning June. It seems that Sodinokibi ransomware is the right candidate to fill the hole left behind GandCrab.
Qihoo 360 releases a GandCrab v5.2 decryption tool
Previously, 360 Total Security intercepted all aspects of the attack and fully supported the powerful killing of the entire series of GandCrab ransomware. Nowadays, 360 Total Security launch the decryption tool for GandCrab v5.2, which means that 360 Total Security have supported GandCrab ransomware 4.0/5.0/5.0.2/5.0.3/ 5.0.4/5.1/5.2 full range of decryption, users who have been infected can successfully decrypt the file without paying for the ransom!
Crown Ransomware discovered
Petrovic discovered a new ransomware called Crown that appends the .CROWN extension to encrypted files.
July 10th 2019
New eCh0raix Ransomware Brute-Forces QNAP NAS Devices
A new ransomware strain written in Go and dubbed eCh0raix by the Anomali Threat Research Team is being used in the wild to infect and encrypt documents on consumer and enterprise QNAP Network Attached Storage (NAS) devices used for backups and file storage.
How We Seized 15 Active Ransomware Campaigns Targeting Linux File Storage Servers
More eCh0raix news by Intezer who call this ransomware QNAPCrypt.
We at Intezer have detected and temporarily DoS’d the operation of a ransomware targeting Linux-based file storage systems (NAS servers).
New .BKP Dharma variant
Michael Gillespie found a new Dharma ransomware variant that appends the .BKP extension.
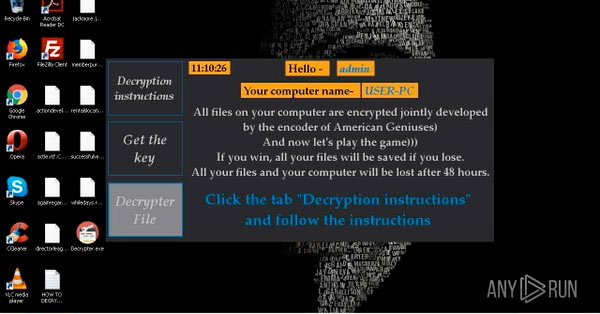
Wanna Dead Ransomware discovered
MalwareHunterTeam found a new ransomware called Wanna Dead that is based off of HiddenTear and does not encrypt anything.
Rodentia Ransomware discovered
MalwareHunterTeam found a new Jigsaw Ransomware variant called Rodentia Ransomware that does not encrypt anything.
New Nemesis Ransomware variant
GrujaRS found a new Nemesis Ransomware variant that appends the YOUR_LAST_CHANCE extension to encrypted files and drops a ransom note named _RESTORE FILES_.txt.
Westchester Library System Attacked By Ransomware Virus
A ransomware virus attack on the Westchester Library System is being investigated, an IT official said on Wednesday, July 10.
July 11th 2019
New HTML Dharma variant
Amigo-A has discovered a new Dharma ransomware variant that appends the .HTML extension to encrypted files and drops a ransom note named HOW_TO_DECRYPT.txt/
STOP Decryptor updated
Michael Gillespie updated his STOP DJvu decryptor to support the offline keys for the .cezor and .lokas extensions.
Mayors pass resolution against paying ransomware ransoms
The U.S. Conference of Mayors has passed a resolution calling on city leaders not to pay ransoms to their cyberattackers in the event ransomware attacks.
New Godes STOP Djvu variant
Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .godes extension.
New Bulba Ransomware
GrujaRS found a new ransomware called Bulba that appends the .Pox extension and drops a ransom note named HOW TO DECRYPT FILES.txt.
Northwest Indian College Hit with Ransomware
This week, the Northwest Indian College (NWIC) has been facing a cyberattack identified as the Ryuk ransomware virus. The outbreak has corrupted many internal files on our systems, including backups and legacy data.
July 12th 2019
Monroe College Hit With Ransomware, $2 Million Demanded
A ransomware attack at New York City's Monroe College has shutdown the college's computer systems at campuses located in Manhattan, New Rochelle and St. Lucia. Attackers are demanding $2 million ransom to restore their files.


Comments
Amigo-A - 4 years ago
Thank you!
Also has discovered a new YYTO Ransomware variant that appends the .mo7n extension to encrypted files and drops a ransom note named readme.txt
https://twitter.com/Amigo_A_/status/1149269000360202241
This version uses the new full extension format, which earlier not used.
Full extension: .id45678234@readme.txt.mo7n
The affected user asked help at a forum.
https://www.bleepingcomputer.com/forums/t/700744/
Zyflare - 4 years ago
Hi guys, I'm sorry if I'm making the post in the wrong area and I can't write english very well but I got a important file encrypted with my students grades. I lost a lot of files but I just couldn't have lost this one. Can someone please help me to recover this one file, please?