
Microsoft is rolling out Microsoft Forms proactive phishing detection to improve the product's security by blocking phishing attacks from abusing surveys and forms created using the app.
Microsoft Forms is part of Microsoft's Office 365 cloud-based subscription service and it allows users to create surveys, quizzes, and polls designed to collecting feedback and data online.
"In order to make Forms a more secure service, we are going to enable automatic phishing detection to prevent our customers from losing sensitive data via phishing forms," says an update to the Microsoft 365 Roadmap.
The new feature uses automated machine reviews to "proactively detect malicious password collection in forms and surveys" in an attempt to block phishers from abusing the Microsoft Forms app to create phishing landing pages.
Users can also report Forms-based phishing
Just in case Microsoft Forms' automated phishing attack detection fails to detect a phishing attempt, users can also report it to Microsoft with the help of the "Report abuse" link under "Submit" button at the bottom of the form.
"If you suspect a form or survey you've received is attempting to collect passwords or other sensitive information in Microsoft Forms, report it to help prevent yours and other's private information from getting compromised," states Microsoft.
Redmond also recommends never providing sensitive info via online surveys or forms as the best approach for protecting oneself from phishing attacks.
Microsoft Forms phishing on the rise
This change couldn't have come at a better time seeing that phishing campaigns abusing Microsoft Forms are an ongoing trend among scammers since the app was released back in June 2016, with new attacks being spotted and reported more and more often. [1, 2, 3, 4]
Until now, people targeted by Microsoft Forms-based phishing did not have a way to report this type of attack to Redmond's Microsoft Spam Analysis and Microsoft Phishing Analysis teams.
The recommended way to do it according to Microsoft Security team would be to pick one of the methods described in a support document describing how to send spam, non-spam, and phishing scam message samples to Microsoft for analysis.
#Phishing @Office @OfficeFrance https://t.co/gO2I5sTk69 maybe it could be close in less than 3 days, Thanks @malwrhunterteam pic.twitter.com/FZl0DNFojk
— Yves Agostini (@yvesago) March 31, 2017
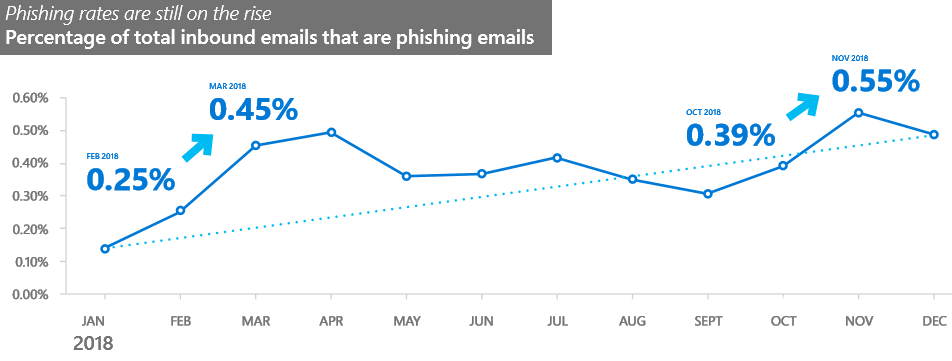
As per Microsoft's Security Intelligence Report (SIR) Volume 24 published in March, phishing attacks, on the whole, have seen an astounding 250% increase in 2018, with scammers moving to multiple points of attacks during the same campaign, switching between domains and servers when sending phishing e-mails and hosting phishing forms.
These results were the outcome of scanning and analyzing over 470 billion email messages sent and received by Office 365 customers, which gave the company bird's eye view over the evolution of phishing trends and methods.
Microsoft services heavily targeted by phishers
Microsoft's Azure Blob Storage object storage solution for the cloud is also abused by crooks [1, 2] to host phishing forms to take advantage of the fact that it will automatically get signed by an SSL certificate from Microsoft.
This makes Azure Blob Storage-based phishing the ideal method of creating phishing forms that directly target Microsoft services such as Office 365, Azure Active Directory, Outlook and a whole slew of other Microsoft logins.
While users who want to detect phishing attacks are advised to check the URL of login forms they are asked to fill in, phishing campaigns that use Azure Blob Storage render this piece of advice almost worthless.
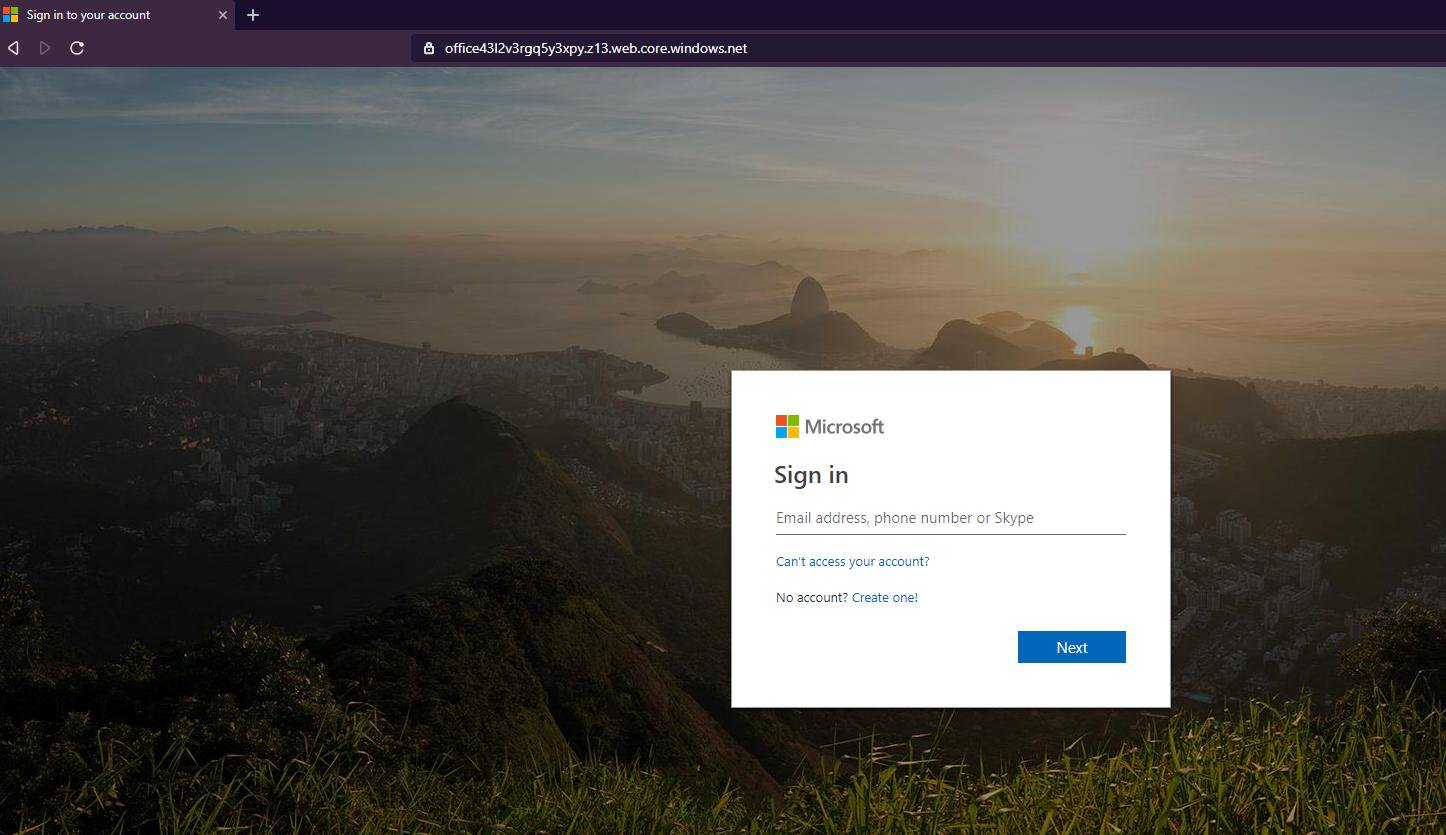
The only way to be sure that crooks aren't trying to steal your Microsoft credentials is to remember that official login forms will always be hosted by Microsoft using microsoft.com, live.com, or outlook.com domains, not on domains similar to https://1drive6e1lj8tcmteh5m.z6.web.core.windows[.]net.
Microsoft is also adding to the security capabilities of Office 365 periodically as shown by the inclusion of protection against malicious macros by extending the Antimalware Scan Interface (AMSI) to Office 365 client apps, as well as of more control over encrypted emails shared outside an organization.
A comprehensive list of security best practices for Office 365 provided by Microsoft on its documentation website will also help users "minimize the potential of a data breach or a compromised account."


Comments
JohnnyJammer - 4 years ago
A little hint that i use, block/filter any url with blob.core.windows.net and also web.core.windows.net in the envelope and header in your mail flow rules.
I must also note i am seeing a large number of .iqy extensions (Pointing to github and executing a powershell command) coming my way and also phishing using sway in office365 instead of forms.
Side note: Any one else having issues accessing urlquery.net, has it been shutdown or?