
2020 U.S. presidential campaigns are not using proper email security according to research from Californian-based email threat protection firm Agari.
Their analysis shows that most of the political campaigns of current major party candidates for next year's U.S. presidential elections (polling at 1% or higher as per Real Clear Politics) are failing to implement proper Domain-based Message Authentication, Reporting and Conformance (DMARC) policies to protect their donors and voters from phishing attacks that could lead to fraud.
Domain administrators can employ DMARC to protect the users who receive forged emails by enabling policies that will redirect them into the Junk folder (’p=quarantine’), or reject it completely (’p=reject’). For domains where DMARC is used by only the ‘p=none’ policy is enabled, the spoofed emails will go through, but the admin of the impersonated domain will also be alerted.
As the Department of Homeland Security’s Binding Operational Directive 18-01 on how to enhance email and web security states, "setting a DMARC policy of 'reject' provides the strongest protection against spoofed email, ensuring that unauthenticated messages are rejected at the mail server, even before delivery."
Agari's research shows that only 4 out of the 13 candidates are properly utilizing the REJECT policy in DMARC, which leaves them and their donors open to phishing attacks.
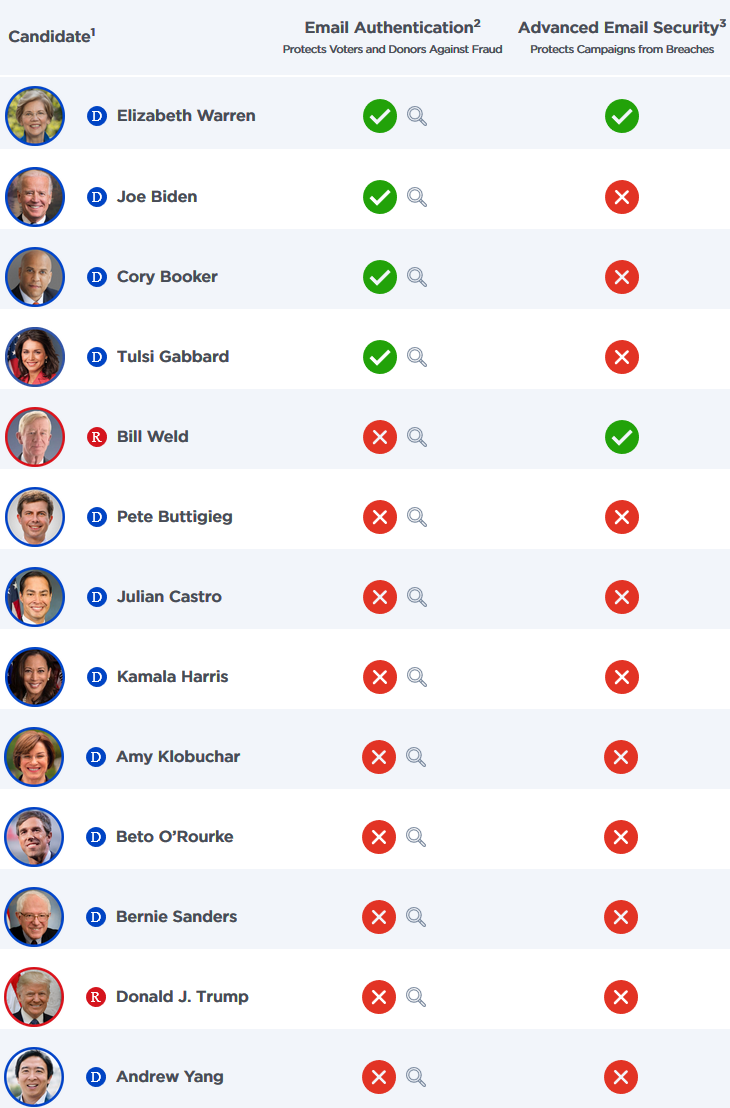
Advanced email security is also not used by the vast majority of campaigns, with Advanced Threat Protection or Secure Email Gateways not being used for Google Suite and Microsoft Office 365 email accounts as a measure against potential security breaches.
Out of the 13 political campaigns analyzed by Agari's research team, only Elizabeth Warren's and Bill Weld's campaigns have implemented advanced email security protections for their campaigns' emails, with Warren's campaign being the only one out of the list properly secured.
"Only one candidate has completely secured her campaign against the types of email threats that will harm campaign staff, potential donors, and the public," says Agari. "Other candidates should also implement these controls to protect themselves against data breaches and impersonation scams."
Also, while Bill Weld's campaign is one of the two with advanced email security, a DMARC Reject policy is not used therefore the campaign's donors and Weld's voters are being exposed to email spoofing-based phishing attacks.
Federal Election Commission giving a helping hand
However, there is still time for security improvements, especially since a U.S. Federal Election Commission (FEC) ruling from yesterday part of Advisory Opinion 2019-12 said that privately-held email security companies now are allowed to provide services at little or no cost to political campaigns.
The Commission approved an advisory opinion in response to a request from Area 1 Security, Inc. The Commission concluded that Area 1’s proposal to offer cybersecurity services to federal candidates and political committees under a low- to no-cost pricing system is permissible under the Act and would not result in prohibited in-kind contributions because Area 1 would offer the services in the ordinary course of business and on the same terms and conditions as offered to similarly-situated non-political clients.
This would make it possible for them to assist 2020 presidential candidates with properly protecting their campaigns from email-based attacks such as the ones launched by Russian hackers during the 2016 U.S. Presidential elections.
The FEC also responded to Area 1 Security's request of offering "anti-phishing services to qualified federal candidates and political committees under its “low or no cost” pricing tier," stating that charging them a $1,337 fixed fee per year is OK "because doing so would be in the ordinary course of Area 1’s business and on terms and conditions that apply to similarly situated non-political clients."
"Today’s decision ensures the next President of the United States will be decided by the voters, not cyber criminals or nation-state influencers," says Agari's Chief Marketing Officer Armen Najarian.
"It is our full expectation that the cyber attacks against the 2020 U.S. presidential candidates will be more aggressive than we’ve seen before, because these attackers continue to move away from content-based techniques and towards identity-based attacks, which many cybersecurity technologies cannot detect."
Agari told BleepingComputer that it "had made an offer to provide our technology to all campaigns at no charge. The FEC has approved doing so through the Defending Digitial Campaigns (DDC) initiative. We are actively working the DDC to make our cybersecurity software and services available at no cost."
Also, Agari said that it offers services at no charge for all candidates to "ensure that 2020 U.S. presidential campaigns are protected from nation-state attacks and other types of email fraudsters so that it is the U.S. citizens who determine the next president of the U.S., not cybercriminals."
Govt agencies and tech firms also afflicted by improper email security
Incorrectly implemented DMARC for phishing protection and Secure Email Gateways not being used to properly secure email accounts against attacks are also plaguing privately-held tech companies and government agencies as shown by two studies from March 2019 and October 2018, respectively.
In the case of tech companies, only around 10,5% of them have properly implemented the DMARC email authentication protocol according to an industry report from Valimail.
Although 51% of the 525 global tech firms examined implemented DMARC, 3,6% configured it incorrectly and about 35% correctly set it up but, unfortunately, don't use enforcement, thus exposing themselves to attacks based on email spoofing because of mail flow visibility exposure.
Also, 10,5% (55 of the tested domains) have properly configured DMARC records that also set a policy designed to automatically block phishing attacks using email spoofing.
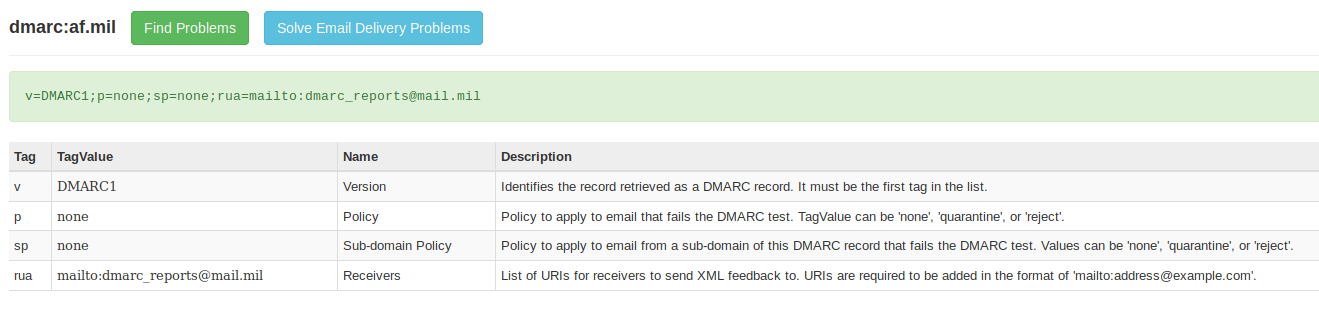
U.S. government agencies also fail to fully embrace DMARC email security policy as shown by an Agari report from October, with DMARC being present for 85% of the domains as required by the Department of Homeland Security (DHS), but only 74% of them having the ‘p=reject’ policy toggled on.
While this is "the fastest and most complete adoption of the DMARC standard for any industry in history" according to Agari, there were still issues with 278 domains from government agencies still not complying to DHS’ directive to enable the ‘reject’ policy in DMARC. Department of Defense, for instance, had a total of 32 out of 35 domains without a DMARC record.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now