
A new version of the 16Shop phishing kit has been observed in the wild, with more than 200 URLs loading login aimed at collecting login information from Amazon customers.
16Shop is a sophisticated commercial product that features protection against unlicensed use and against research attempts. It can also adapt the phishing templates to the type of device they load on.
A previous variant of the phishing kit observed since November 2018 targeted Apple users via malicious emails accompanied by a PDF file that redirected to a page asking for Apple account data, including payment card details.
Researchers at McAfee noticed in May 2019 a new strain of the tool that focused on Amazon users, as revealed by the PHP code for 16Shop.
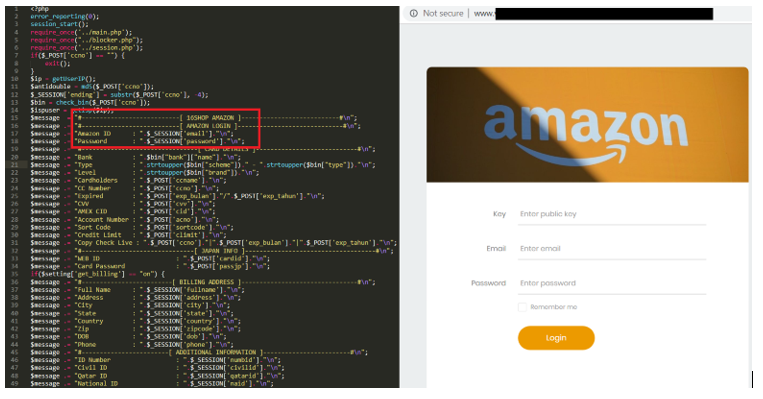
In a blog post today, Oliver Devane and Rafael Pena surmise that phishing is likely the method used to lure victims into loading the fake login pages.
In the case of the Apple campaign, a typical email from the threat actor urged the recipient to check the information associated with their account.
The request was motivated by an alert that someone is logging in and making possibly unauthorized changes. A similar email may be used with Amazon customers.
The report details that the social media account of the group believed to be behind 16Shop changed the profile picture to something that shared elements from Amazon's official logo.

Of the 200 URLs McAfee observed to serve the phishing kit, all of them have been marked as malicious, indicating extensive use of the threat in the wild.
"The group responsible for 16Shop kit continues to develop and evolve the kit to target a larger audience." - McAfee
The Amazon version of 16Shop seems to be the original development from its creators, unlike the pirated variants that come with a backdoor.
The cracked release has a local configuration file so contacting the author's server is no longer required for the API-driven validation process.
However, this free pass does not come without a price. Researchers at Akamai discovered that these copies include code that creates a second communication channel via the Telegram messaging app.
The cracker implemented this functionality so they receive the same data the kit's operator gets from the victims. The code is highly obfuscated, so it becomes clear that the purpose was to double-cross anyone foolish enough to believe that they got 16Shop for free.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now