
U.S. Senator Ron Wyden sent a letter to the National Institute of Standards and Technology (NIST) Director Walter G. Copan urging the agency to develop and issue standards as part of a guidance framework for securely sharing sensitive documents over the Internet.
"Government agencies routinely share and receive sensitive data through insecure methods — such as emailing .zip files — because employees are not provided the tools and training to do so safely," says the Senator in the letter.
Broken sensitive data sharing process
Wyden's request was prompted by the widespread sharing of highly sensitive files packed as password-protected zip files via email in the government sector, with many of the people doing that this way the data is protected while in transit and after reaching the inbox.
However, as the Senator underlines in his letter, "many password-protected .zip files can be easily broken with off-the-shelf hacking tools. This is because many of the software programs that create .zip files use a weak encryption algorithm by default."
Johns Hopkins University Associate Professor Matthew D. Green confirmed the issue in a Twitter thread, saying that "Right now on many ancient versions of Windows, when you 'encrypt' (password protect) a ZIP file using the OS default utility, you get encryption using the legacy ZIP scheme, which is totally broken."
In addition, the PKZIP stream cipher vulnerable to a known plaintext attack causing this issue is "the default ZIP encryption algorithm on Windows XP and (ugh) current versions of MacOS. To Microsoft’s credit, they removed it on more recent versions of the home version of Windows."
Insecure data sharing channels a possible national security threat
Wyden also stated in the request sent to the NIST that this vulnerable sensitive data sharing workflow represents a conceivably disastrous threat seeing that high-profile data breaches and cyber attacks by foreign state actors are a continuous menace to the U.S. national security.
"The government must ensure that federal workers have the tools and training they need to safely share sensitive data," also argued the Senator in his letter.
"To address this problem, I ask that NIST create and publish an easy-to-understand guide describing the best way for individuals and organizations to securely share sensitive data over the internet."
Green added that "there’s a huge opportunity here if NIST responds and asks the community for proposals" with "a huge opportunity for smart people in this field to come up with something much better."
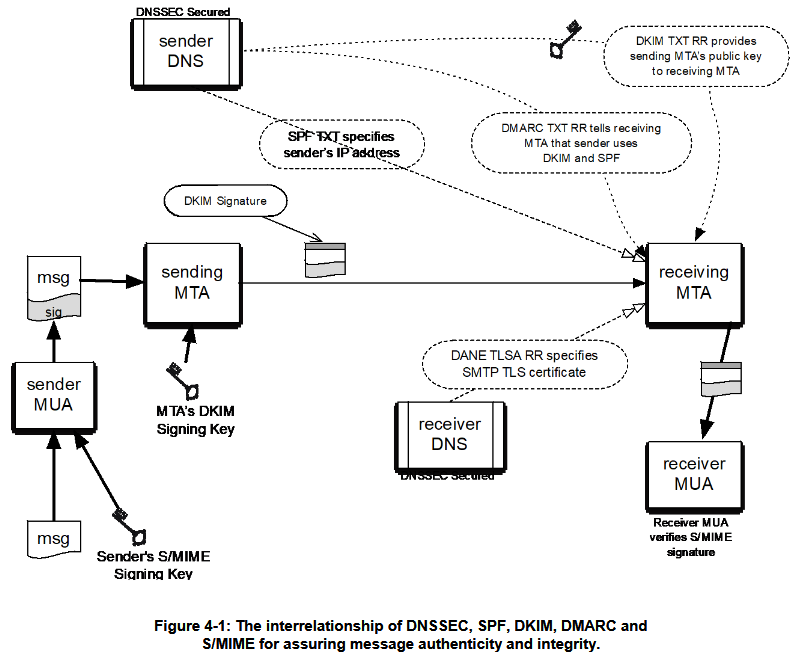
Email content security NIST recommendations
A foundation is already there seeing that NIST released a "Trustworthy Email" publication on February 26 which provides recommendations on how to reduce "the risk of spoofed email being used as an attack vector" and "of email contents being disclosed to unauthorized parties."
"These recommendations cover both the email sender and receiver," as explained by NIST, with Section 5 of the publication covering "server-to-server and end-to-end email authentication and confidentiality of message contents. This includes email sent over Transport Layer Security (TLS), Secure Multipurpose Internet Mail Extensions (S/MIME) and OpenPGP."
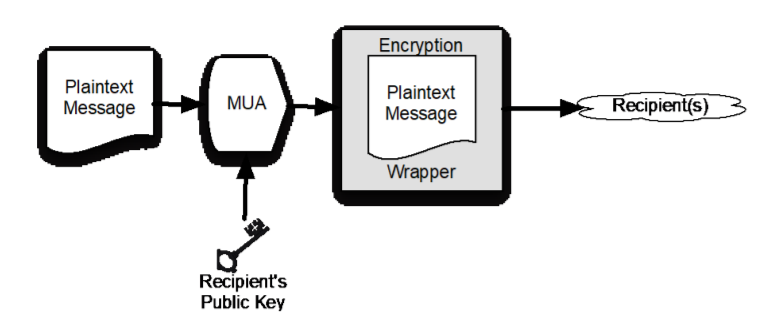
While NIST presents both S/MIME and OpenPGP as options for securing email content, the agency provides the following recommendation to federal organizations: "Do not use OpenPGP for message confidentiality. Instead, use S/MIME with a certificate that is signed by a known CA."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now