
Microsoft issued a warning about an active spam campaign that tries to infect Korean targets with a FlawedAmmyy RAT malware distributed via malicious XLS attachments.
The Microsoft Security Intelligence Twitter account explained in a thread that a currently active campaign "employs a complex infection chain to download and run the notorious FlawedAmmyy RAT directly in memory."
Attacks will start after the victims open the attached .xls file that "automatically runs a macro function that runs msiexec.exe, which in turn downloads an MSI archive. The MSI archive contains a digitally signed executable that is extracted and run, and that decrypts and runs another executable in memory."
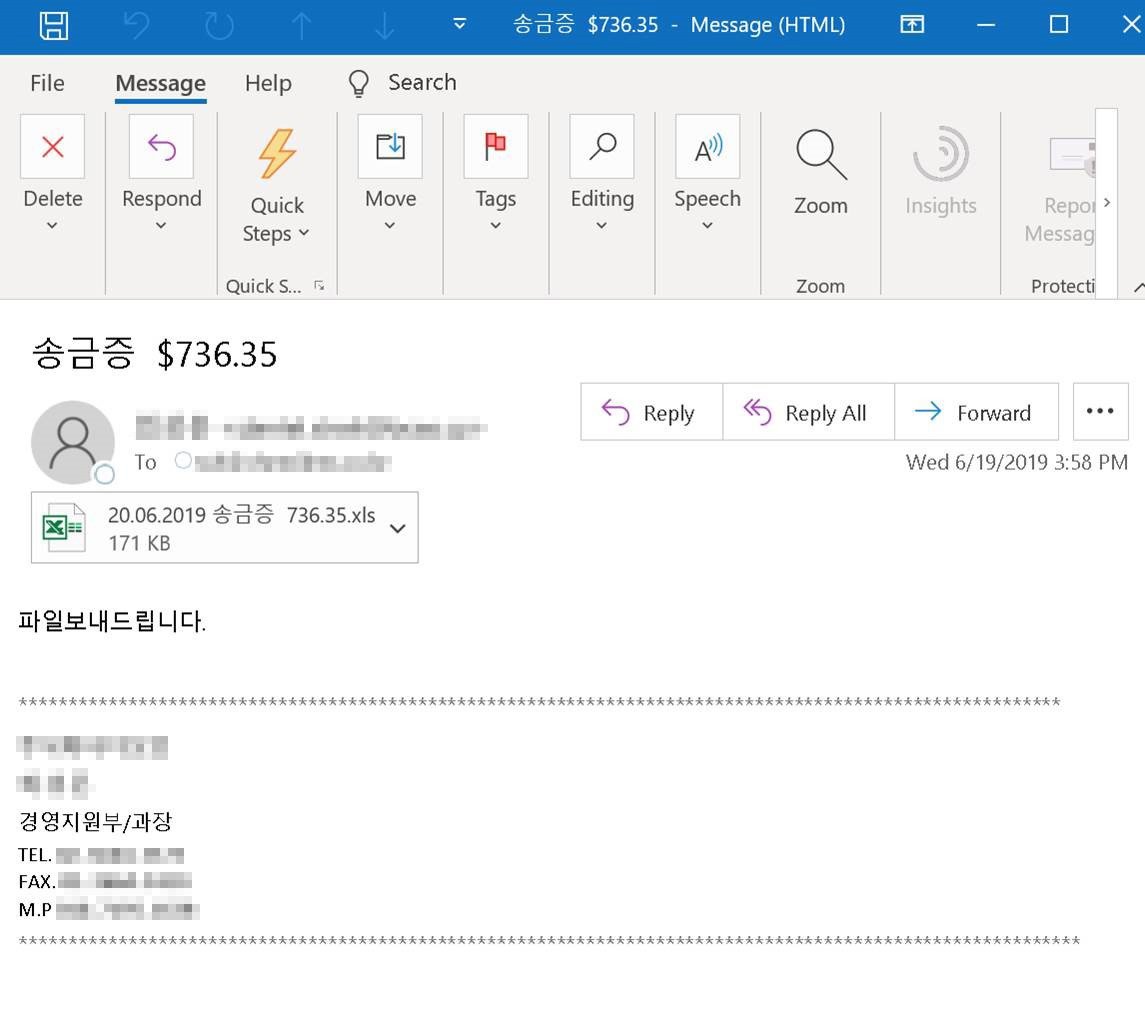
The executable will proceed to download and decrypt yet another malware payload named wsus.exe and digitally signed on June 19. This is the dropper which will decrypt and launch the attack's final malicious payload directly into the compromised computer's memory.
As discovered by Microsoft Security Intelligence, the payload is the FlawedAmmyy remote access Trojan, one of the favorite tools of a cybercriminal group named TA505 by Proofpoint which started dropping as part of spam campaigns targeting retailers and financial institutions. [1, 2, 3]
Just a week ago, Trend Micro's threat analysts detected a similar campaign to the one just observed by Microsoft, delivering the FlawedAmmyy RAT via malicious .XLS attachments and targeting South Korean users, and attributed to the TA505 group.
Security researcher Vitali Kremez tweeted about several FlawedAmmyy samples delivered via other spam campaigns, digitally signed using code signing certificates from Thawte [1, 2].
Microsoft Security Intelligence issued another warning on June 7 about a malspam campaign delivering RTF attachments designed to exploit the Microsoft Office and Wordpad CVE-2017-11882 vulnerability.
While the CVE-2017-11882 vulnerability was patched by Microsoft two years ago, Redmond's security researchers state that the exploit is still actively being used in attacks, with "increased activity in the past few weeks."
Microsoft provides a full list of indicators of compromise (IOCs) including hashes of the digitally signed executables used in the campaign and of the FlawedAmmyy RAT HERE and HERE.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now