
Tor Browser 8.5.3 has been released to fix a Sandbox Escape vulnerability in Firefox that was recently used as part of a targeted attack against cryptocurrency companies. As this vulnerability is actively being used, it is strongly advised that all Tor users upgrade to the latest version.
When starting Tor Browser, it should alert you if a new version is available. If you would like to perform a manual check, you can do so by going to Tor Browser menu -> Help -> About Tor Browser.
Unfortunately, like the previous release, the Android version of Tor Browser 8.5.3 will not be available until the weekend as part of the Tor team who handles the Android signing token is away at an event.
Tor 8.5.3 can be downloaded from the Tor Browser download page and from the distribution directory.
The full changelog for Tor Browser 8.5.3 is:
Tor Browser 8.5.3 -- June 21 2019
* All platforms
* Pick up fix for Mozilla's bug 1560192
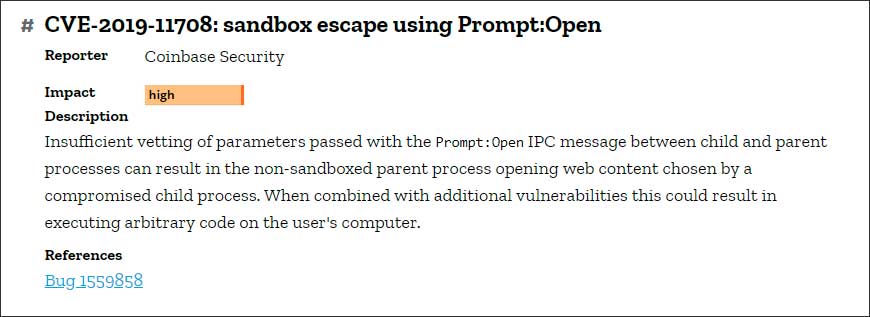
Sandbox Escape vulnerability fixed
This week it was discovered that two Firefox zero-day vulnerabilities were used as part of targeted attacks against cryptocurrency firms. The two vulnerabilities used in the attack are a remote code execution vulnerability chained with a sandbox escape vulnerability.
Yesterday, the Tor Project released Tor 8.5.2 to fix the RCE vulnerability, and today's release of 8.5.3 fixes the Sandbox Escape vulnerability in the bundled Firefox browser.
"This release includes an important security update in Firefox, a sandbox escape bug, which combined with additional vulnerabilities could result in executing arbitrary code on the user's compute"
When these two vulnerabilities were chained together, they were able to download and install information-stealing Trojans on a victim's computers as well as remote access to the computer's network.
Due to this, it is imperative that users install this update immediately.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now