
Update May 23: A HCL spokesperson sent the following official statement following BleepingComputer's request for comment:
HCL Technologies takes data security extremely seriously. As soon as this incident was reported, HCL took immediate action to block the inadvertent access. Based on our investigation of this specific issue, we have determined that no sensitive employee or customer data was accessed, compromised or exposed in any way, per any applicable privacy regulations. We remain deeply committed to the values of trust and transparency that underpin our relationship with our employees and customers. If there is any further information relevant to this incident, we will provide an update.
IT service and consulting company Hindustan Computers Limited (HCL) exposed a huge trove of employee and business information via publicly accessible pages and web interfaces hosted on multiple subdomains.
HCL is an Indian company in the Forbes Global 2000 list with over 200 Fortune 500 customers and more than 600 from the Forbes Global 2000 list, as well as operations across 40 countries, covering a large array of industries from IT services, banking, and automotive to telecom, capital markets, and media [1, 2].
According to UpGuard, the exposed public data "included personal information and plaintext passwords for new hires, reports on installations of customer infrastructure, and web applications for managing personnel."
The exposed data was first discovered by UpGuard's research team on May 1 when a document freely downloadable and containing customer keywords was detected on an HCL domain, which subsequently led to the discovery of "other publicly accessible pages with personal and business data."
Given that the pages containing the leaked data were hosted on multiple HCL subdomains and could only be accessed via a web interface, the researchers finalized their analysis oft he exposed information only after five days.
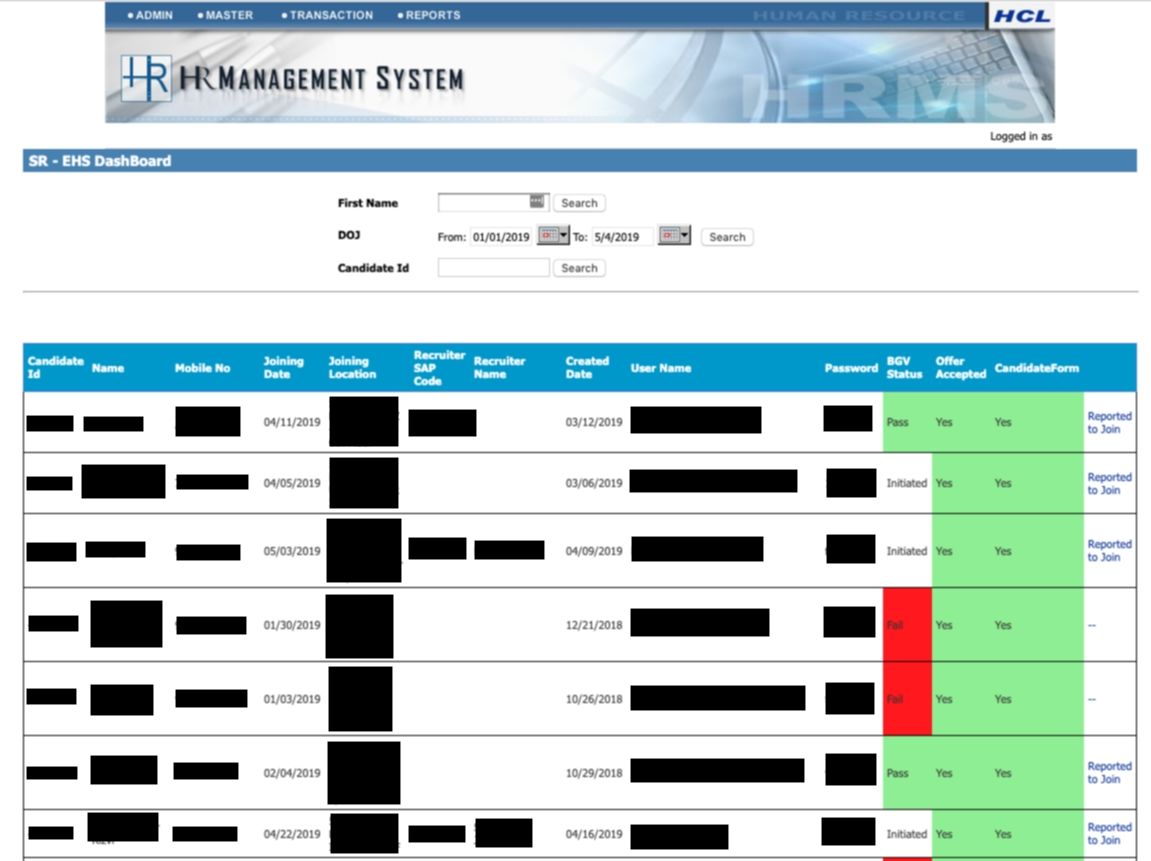
After further analyzing the leaked information, UpGuard found a dashboard used to managed newly hired personnel records with 364 records.
The oldest were from 2013, but over two hundred records were from 2019. In fact, 54 of the records were for people who joined on May 6, 2019. The exposed data included candidate ID, name, mobile number, joining date, joining location, recruiter SAP code, recruiter name, created date, user name, cleartext password, BGV status, offer accepted, and a link to the candidate form. Among those data points, the most obvious risk is that the passwords could be used to access other HCL systems to which these employees would be given access.
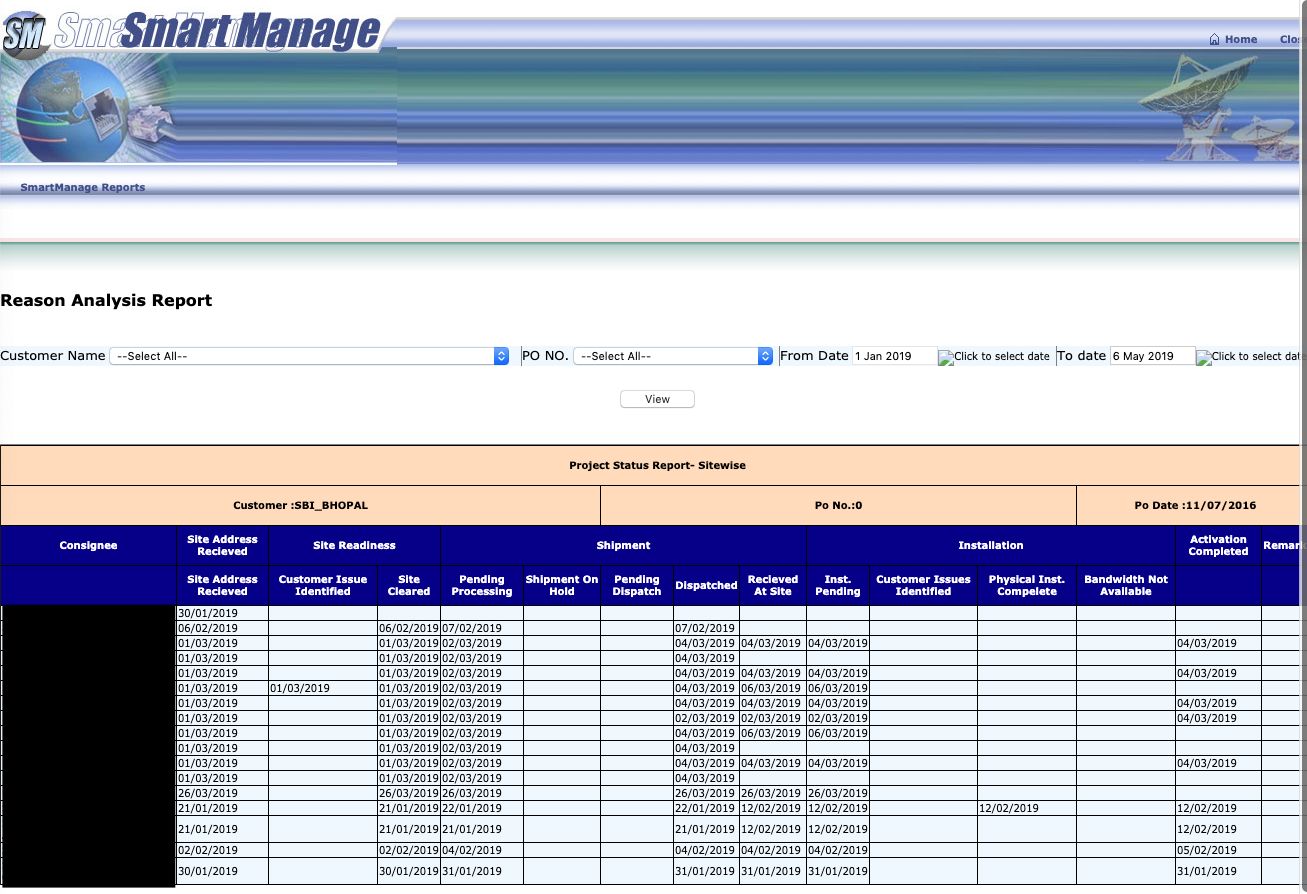
The researchers found even more leaked information on other pages which did not require authentication to be accessed, ranging from "names and SAP codes for over 2,800 employees" and "a field where SAP codes and names could be used to look up and 'deactivate' employees" to customer installation reports and project data managed using the SmartManage reporting system.
And the stream of exposed data did not stop here. UpGuard also unearthed a database of internal analysis reports listing 5700 incident records, weekly customer reports which contained roughly 18,000 entries, as well as installation reports going back to 2016.
No response to data leak notifications but data got secured
UpGuard sent a notification detailing the nature of the leaked data, two of the publicly accessible pages, and a list containing subdomains exposing business info to HCL’s Data Protection Officer but did not get any reply.
The next day, on May 7, even though the UpGuard's team saw that the two pages that were sent in as part of the data leak notification were now secured and required authentication to be accessed, all other pages that weren't included in the notice sent to HCL were still unprotected.
"The analyst sent a followup email linking to other pages with HCL data, and on the next day, May 8, the analyst confirmed that those pages were also no longer accessible to anonymous users," says UpGuard.

While HCL did not establish any sort of communication channels with the company reporting the data leak to their Data Protection Office, UpGuard report concludes that "business leaders should also note the effectiveness of HCL’s response."
Although HCL did not answer the data exposure notifications, it "advertised how to report exposures to them and acted promptly toward a remedy. In a world where data loss of some kind is inevitable, effective incident response like this is a vital capability."
BleepingComputer also reached out to HCL for an official statement but had not heard back at the time of this publication.
Image credits: dtuluu / Composition: BleepingComputer


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now