
The Australian Federal Police (AFP) arrested a 33-year-old government IT contractor from the Upper North Shore Killara suburb of Sydney, New South Wales, for allegedly running a shadow mining scheme using the government's computing systems.
According to the AFP press release, the man "abused his position as an IT contractor to manipulate programs to use the processing power of the agency’s computer network for crypto currency mining."
The covert cryptomining operation netted the Australian Government employee an estimated AUD$9000 worth of cryptocurrency and it concluded with him being scheduled to appear today in the Sydney Local Court (Downing Centre) to face charges.
An Australian Government employee will face Sydney Local Court today over his role in allegedly modifying his agency’s computer systems to mine crypto currency for personal gain. https://t.co/Cr7NcYtih7
— AFP (@AusFedPolice) May 20, 2019
As the AFP statement says, the IT contractor is charged with:
- Unauthorised modification of data to cause impairment, contrary to section 477.2 of the Criminal Code Act 1995 (Cth)
- Unauthorised modification of restricted data, contrary to section 478.1 of the Criminal Code Act 1995 (Cth).
"Australian taxpayers put their trust in public officials to perform vital roles for our community with the utmost integrity," stated Acting Commander Chris Goldsmid, Manager Cybercrime Operations.
Also, "Any alleged criminal conduct which betrays this trust for personal gain will be investigated and prosecuted," with public office abuse being a particularly serious matter.
If found guilty, the alleged shadow mining operator who purportedly modified the government agency’s computer systems to run a cryptomining operation for his personal gain could face for the two charges maximum penalties of 10 and two years of prison time.
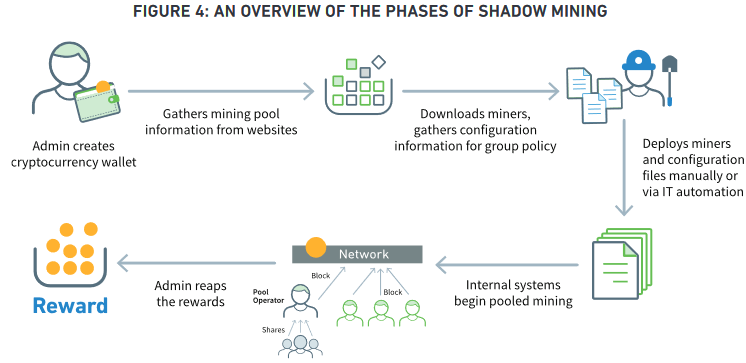
Shadow mining describes the process through which malicious insider take advantage of their company's computing resources to stealthily mine for cryptocurrency.
"To be successful and remain undetected, shadow mining depends on deliberately configuring security systems to function incorrectly," as explained by Exabeam in a report from early-April.
"This makes an organization less secure, introduces software that consumes additional resources, increases the attack surface, and makes affected computers less reliable."


Comments
APlusBruce - 4 years ago
"If found guilty, the alleged shadow mining operator who purportedly modified the government agency’s computer systems to run a cryptomining operation for his personal gain could face for the two charges maximum penalties of 10 and two years of prison time."
I am assuming 10 thousand in penalties and 2 years prisons time.
SamSepiol - 4 years ago
Why assume?
He is facing two different charges.
He could face 10 years for the first charge (Unauthorised modification of data to cause impairment, contrary to section 477.2 of the Criminal Code Act 1995 (Cth)) and two years for the second charge (Unauthorised modification of restricted data, contrary to section 478.1 of the Criminal Code Act 1995 (Cth)).
APlusBruce - 4 years ago
yea i missed the link where it had more on the case. Thanks for telling :)
NickAu - 4 years ago
Knowing the Aussie courts he will probably get 100 hours of community service