
This week we saw mostly new variant of existing ransomware being released and nothing particular ground breaking released.
Of particular interest was a story released by ProPublica about how ransomware recovery companies just pay the ransomware developers rather than actually decrypting your files using their own in-house technology. It is a very interesting read for those who want to see the inner workings of the booming ransomware recovery industry.
I know a lot of people keep saying that ransomware is dead, but with all of the ransomware attacks hitting cities, large companies, and users, I think it's safe to say that ransomware may actually be seeing a resurgence.
Contributors and those who provided new ransomware information and stories this week include: @FourOctets, @DanielGallagher, @malwrhunterteam, @struppigel, @demonslay335, @fwosar, @malwareforme, @Seifreed, @PolarToffee, @jorntvdw, @GrujaRS, @JakubKroustek, @campuscodi, @Renee_Dudley, @jeffykao, @kerathink, @emsisoft, @Amigo_A, @n0x08, and @propublica.
May 11th 2019
New STOP Djvu variant discovered
Michael Gillespie found a new STOP Djvu variant that adds the .codnat extension to encrypted files.
New Dharma variants released
Jakub Kroustek found new variants of the Dharma Ransomware that append the .qbtex and the .yG extension to encrypted files.
New STOP Djvu variant discovered
Michael Gillespie found a new STOP Djvu variant that adds the .codnat1 extension to encrypted files.
May 12th 2019
WannaCry still present on 1.7 million machines
2 years after WannaCry and there’s still 1.7M machines with SMB exposed to the Internet!
May 13th 2019
New DrWeb Dharma variant released
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .drweb extension to encrypted files.
New STOP Djvu variant discovered
Michael Gillespie found a new STOP Djvu variant that adds the .bufas extension to encrypted files.
Wesker Encrypter discovered
Michael Gillespie found the Wesker Encrypter that does not add an extension but drops ransom notes name !!!INSTRUCTION_RNSMW!!!.txt.
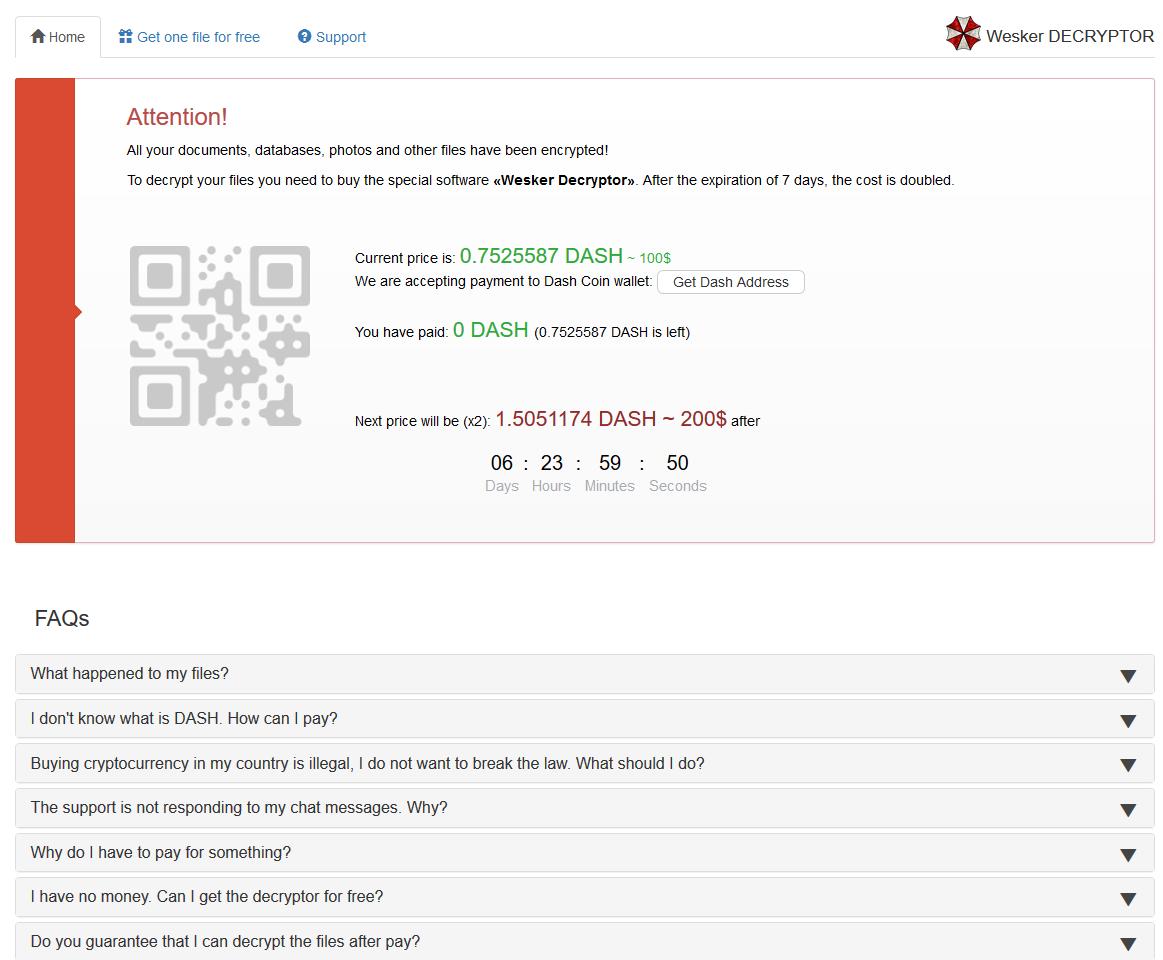
New ChaCha Ransomware variant
Michael Gillespie found a new ChaCha Ransomware variant that appends a random 6-7 char extension and drops a ransom note named DECRYPT-FILES.html.
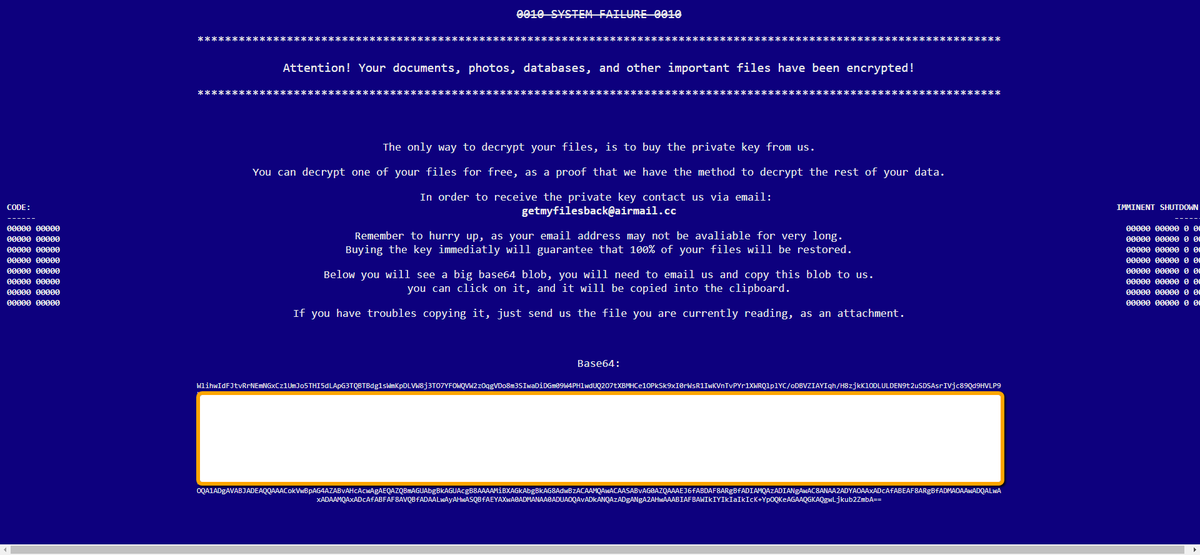
Non Ransomware discovered
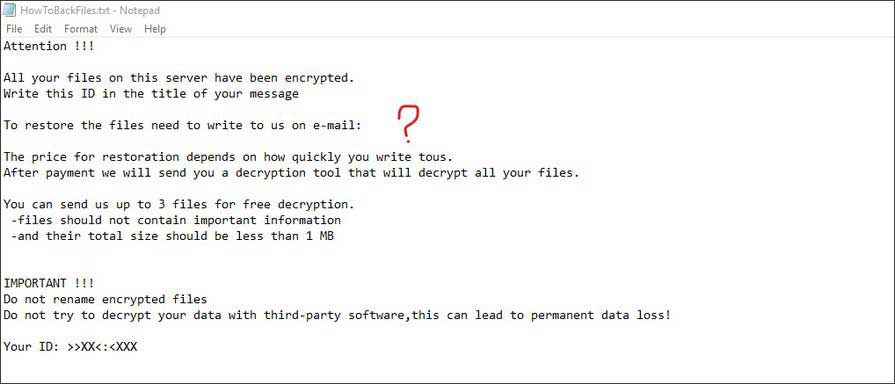
GrujaRS found the Non Ransomware that appends the .non extension and drops a ransom note named HowToBackFiles.txt. Possibly in-dev as the ransom note does not include an email address.
May 14th 2019
New Dharma variants released
Jakub Kroustek found new variants of the Dharma Ransomware that append the .jack and .PLUT extensions to encrypted files.
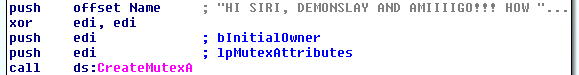
JSWorm Ransomware sends a shoutout to researchers
The JSWorm Ransomware sent a shoutout in its code to MalwareHunterTeam, S!Ri, and Amigo-A.
Possible new Desktop Ransomware variant
GrujaRS found a new ransomware that could be a variant of the Desktop Ransomware. This ransomware prepends the Locked. string to encrypted file's names.
May 15th 2019
THE TRADE SECRET: Firms That Promised High-Tech Ransomware Solutions Almost Always Just Pay the Hackers
As ransomware attacks crippled businesses and law enforcement agencies, two U.S. data recovery firms claimed to offer an ethical way out. Instead, they typically paid the ransom and charged victims extra.
New DDOS Dharma variant released
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .DDOS extension to encrypted files.
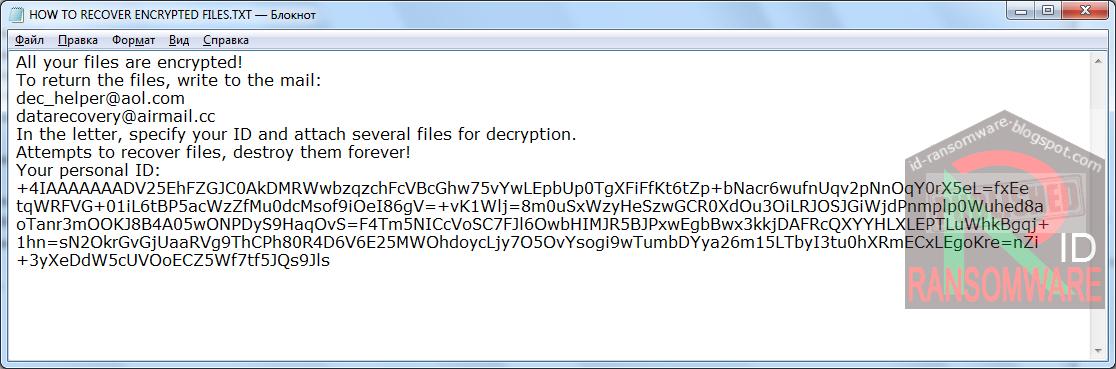
New Oops Scarab Ransomware variant
Amigo-A found a new Scarab Ransomware variant that appends the .Oops extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.
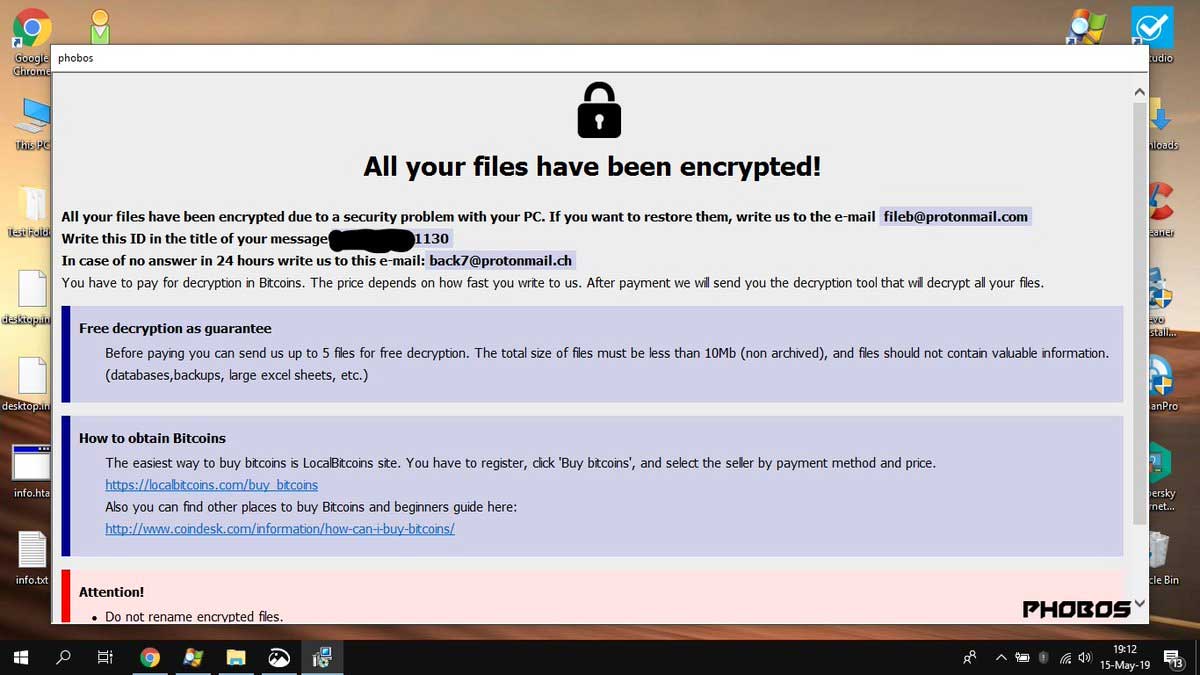
New Mamba Phobos Ransomware variant
GrujaRS found a new Phobos Ransomware variant that appends the .mamba extension to encrypted files.
May 16th 2019
New Cry Dharma variant released
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .cry extension to encrypted files.
New STOP Djvu variant discovered
Michael Gillespie found a new STOP Djvu variant that adds the .dotmap extension to encrypted files.
The Reality Of Ransomware
"About 1.5 million ransomware attacks occur annually, putting individuals and corporations in a no-win situation. ProPublica technology reporter Renee Dudley joins host Krys Boyd to explain how these attacks work, how firms can sometimes recover the stolen data, and how sometimes the solution is just to pay up.Her recent story on the topic is a joint investigation with The Guardian."
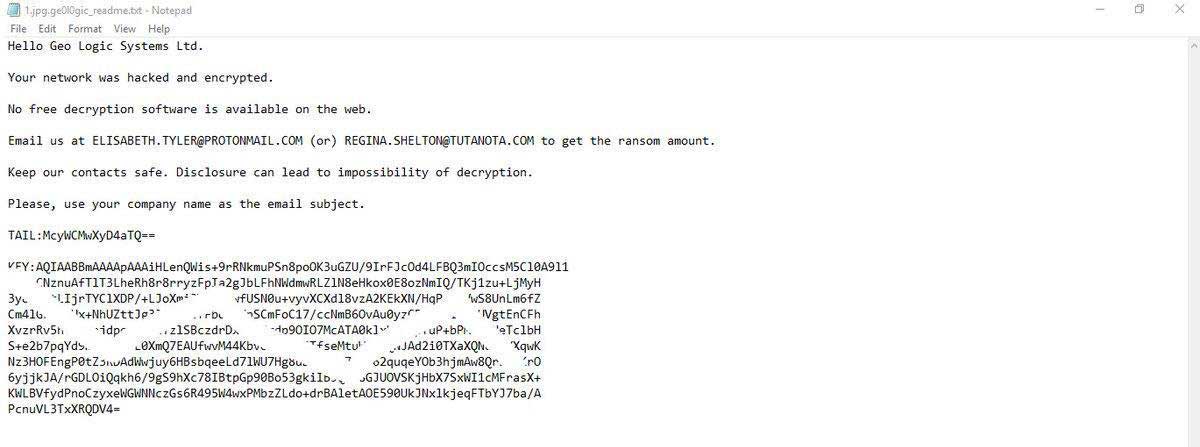
New Ge0l0Gic Ransomware
GrujaRS found the Ge0l0Gic Ransomware that appends the .ge0l0gic extension and drops a ransom note named .ge0l0gic_readme.txt.
ZQ Ransomware decryptor updated
Emsisoft has updated their ZQ Ransomware decryptor to support the w_unblock24@qq.com].ws variant.
May 17th 2019
New 4k Dharma variant released
Jakub Kroustek found a variant of the Dharma Ransomware that appends the .4k extension to encrypted files.
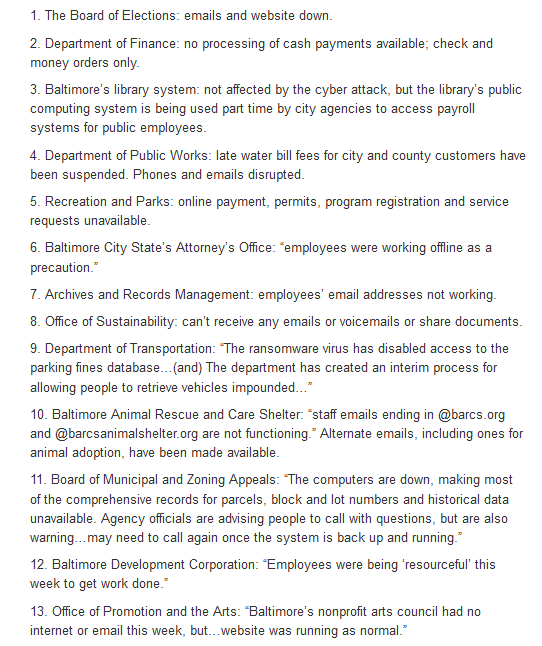
Baltimore Ransomware still affecting city services
Catalin Cimpanu states "A list of what's still down, almost 2 weeks after the attack:"
STOP Djvu Decrypter updated
Michael Gillespie released an update for his STOP Decrypter to support the offline IDs for the .shadow, .fordan, .codnat, and .dotmap extensions.


Comments
Amigo-A - 4 years ago
In addition, this "The Week in Ransomware" - the 150th !!!
Congratulations!!!
Amigo-A - 4 years ago
Non Ransomware when compared turned out to be a new variant of Blitzkrieg Ransomware
https://id-ransomware.blogspot.com/2019/05/blitzkrieg-ransomware.html
Ge0l0Gic Ransomware when compared turned out to be a new variant of IEncrypt Ransomware
https://id-ransomware.blogspot.com/2018/11/iencrypt-ransomware.html
IEncrypt, probably, related to the almost imperceptible and unidentified Streamer Ransomware. But I have samples, and your can explore in more detail.
https://id-ransomware.blogspot.com/2018/10/streamer-ransomware.html
Elvio - 4 years ago
I've been infected by this one in the last week
-----------------------------------------------------------------------------------------------------------
---=== Welcome. Again. ===---
[+] Whats Happen? [+]
Your files are encrypted, and currently unavailable. You can check it: all files on you computer has expansion 2k8q6.
By the way, everything is possible to recover (restore), but you need to follow our instructions. Otherwise, you cant return your data (NEVER).
[+] What guarantees? [+]
Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities - nobody will not cooperate with us. Its not in our interests.
To check the ability of returning files, You should go to our website. There you can decrypt one file for free. That is our guarantee.
If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key. In practise - time is much more valuable than money.
[+] How to get access on website? [+]
You have two ways:
1) [Recommended] Using a TOR browser!
a) Download and install TOR browser from this site: https://torproject.org/
b) Open our website: [Omitted]
2) If TOR blocked in your country, try to use VPN! But you can use our secondary website. For this:
a) Open your any browser (Chrome, Firefox, Opera, IE, Edge)
b) Open our secondary website: http://decryptor.top/186ED1ECFC6F7A07
Warning: secondary website can be blocked, thats why first variant much better and more available.
When you open our website, put the following data in the input form:
Key:
[Omitted key]
Extension name:
2k8q6
-----------------------------------------------------------------------------------------
!!! DANGER !!!
DONT try to change files by yourself, DONT use any third party software for restoring your data or antivirus solutions - its may entail damge of the private key and, as result, The Loss all data.
!!! !!! !!!
ONE MORE TIME: Its in your interests to get your files back. From our side, we (the best specialists) make everything for restoring, but please should not interfere.
!!! !!! !!!
---------------------------------------------------------------------------
According to ID Ransomware, this ransomware is called Sodinokibi