
Over 12,000 unsecured MongoDB databases have been deleted over the past three weeks, with only a message left behind asking the owners of the databases to contact the cyber-extortionists to have the data restored.
Although not on this scale, these types of attacks targeting publicly accessible MongoDB databases have happened since at least early-2017 [1, 2, 3, 4]. Attackers looking for exposed database servers using BinaryEdge or Shodan search engines delete them and demand a ransom for their 'restoration services'.
While Mongo Lock attacks also target remotely accessible and unprotected MongoDB databases, deleting them, and then demanding a ransom in order to get the content back, this campaign does not seem to request a specific ransom amount. Instead, email contact is provided, most likely to negotiate the terms of data recovery.
Sanyam Jain, an independent security researcher and the one who found the wiped databases, provided a very reasonable explanation for this, saying that "this person might be charging money in cryptocurrency according to the sensitiveness of the database."
The contact notes left behind
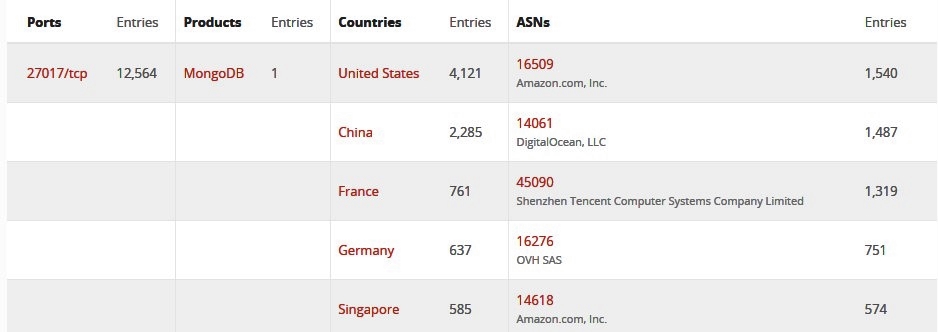
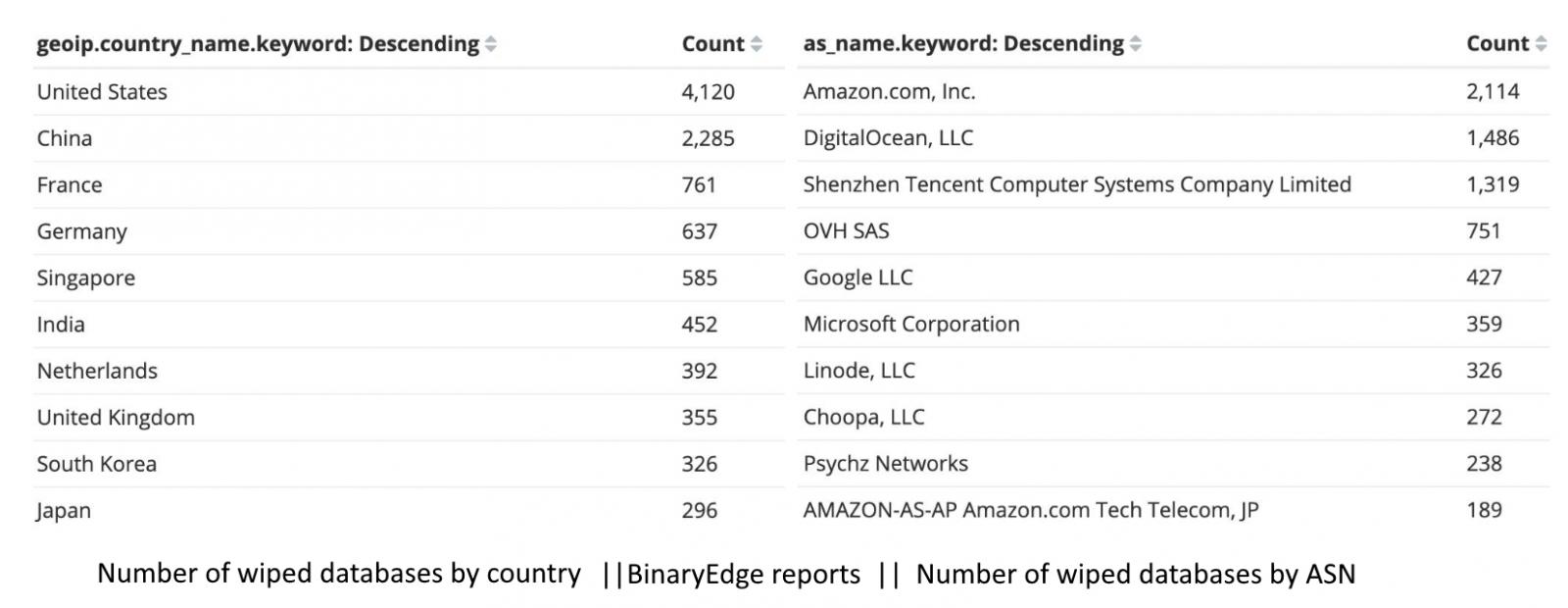
The 12,564 unprotected MongoDB databases wiped by Unistellar were found by the researcher using BinaryEdge (Shodan reports a smaller number of 7,656 databases, probably because of blocked queries).
Seeing that, at the moment, BinaryEdge indexes a little over 63,000 publicly accessible MongoDB servers according to Jain, it seems like the Unistellar attackers have dropped roughly 20% of the total.
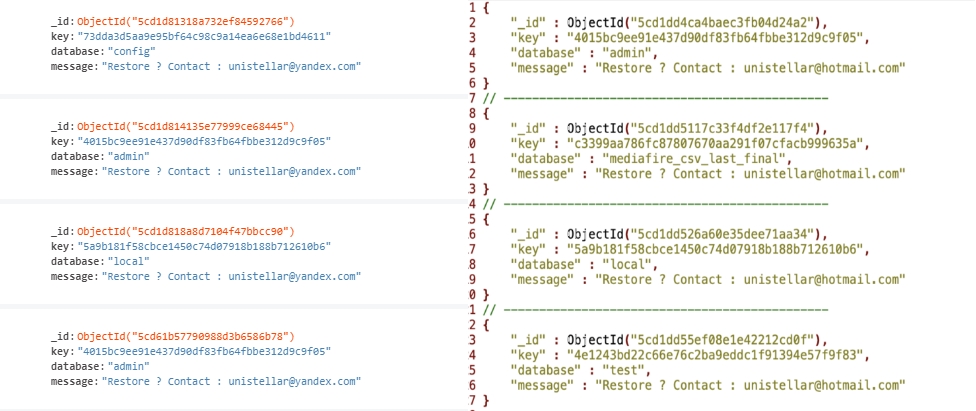
The researcher first noticed the attacks on April 24, when he initially discovered a wiped MongoDB database which, instead of the huge quantities of leaked data he was used to finding, only contained the following note: "Restore ? Contact : unistellar@yandex.com
As he later discovered, after dropping the databases, the cyber-extortionists leave behind ransom notes asking their victims to get in touch if they want to restore their data by sending an email to one of the following two email addresses: unistellar@hotmail.com or unistellar@yandex.com.
While the method used by the attackers to find and wipe databases in such large numbers is not yet known, the entire process is most probably completely automated.
After connecting to one of the publicly accessible MongoDB databases left unprotected on the Internet, the script or program used to do it is also configured to indiscriminately delete every unsecured MongoDB it can find, and then to add the ransom tables.
As Jain told BleepingComputer, the Unistellar attackers seem to have created restore points to be able to restore the databases they deleted.
Unfortunately, there is no way to track if their victims have been paying for the databases to be restored because Unistellar only provides an email to be contacted and no cryptocurrency address is provided.
BleepingComputer also tried to get in touch with Unistellar to confirm that the wiped MongoDB databases are indeed backed up and if any victims paid for their "restoration services" but got no response.
On May 1, Security Discovery researcher Bob Diachenko found an unprotected MongoDB database exposing 275,265,298 records of Indian citizens with detailed personally identifiable information (PII), left exposed unprotected on the Internet for more than two weeks.
The researcher "immediately notified Indian CERT team on the incident, however, database remained open and searchable until today, May 8th, when it got dropped by hackers known as ‘Unistellar’ group."
After the exposed MongoDB database got dropped by Unistellar, Diachenko discovered a note left behind, matching the ones Jain found on the other more than 12,000 wiped databases.
Securing MongoDB databases
These attacks can happen only because the MongoDB databases are remotely accessible and access to them is not properly secured. This means that the database owners can easily prevent such attacks by following fairly simple steps designed to properly secure their database instances.
MongoDB provides details on how to how to secure a MongoDB database by implementing proper authentication, access control, and encryption, and also offers a security checklist for administrators to follow.
More to the point, the two most important measures which will prevent the attacks are to enable authentication and to not allow the databases to be remotely accessible.


Comments
Bullwinkle-J-Moose - 4 years ago
"On May 1, Security Discovery researcher Bob Diachenko found an unprotected MongoDB database exposing 275,265,298 records of Indian citizens with detailed personally identifiable information (PII), left exposed unprotected on the Internet for more than two weeks.
The researcher "immediately notified Indian CERT team on the incident, however, database remained open and searchable until today, May 8th, when it got dropped by hackers known as ‘Unistellar’ group."
----------------------------
Unistellar, the Protectors of Privacy!
Would be fun to see all the servers/drives/databases leaking personal info wiped clean
Would be even more fun to watch the Companies getting wiped trying to explain that "they" are the real victims here
Or we could all wait and twiddle or thumbs waiting for the Guvmint to fix all these Privacy Leaks!
Bwahahahhahahhahhahhahahha