It's a known fact that once your market share is big enough, the bad guys are going after you. Used to be that viruses and malware were only developed for Windows, but when Apple got to be a significant presence on the desktop...voila! There was specific malware developed for the Apple OSen.
Well, looks like KnowBe4 has made it there too, and we have "arrived" at this point. We received our first reports of real bad guy campaigns using our email training templates this email being used on Jan 9th. Here is an image:
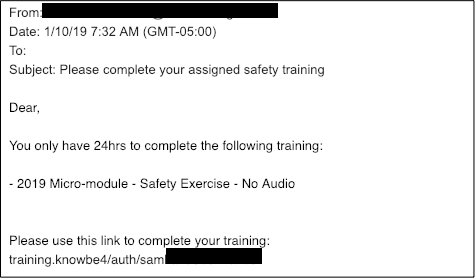
All emails in the wild followed this email template. In the email headers, we determined that these emails were being sent from a compromised account of a legitimate user of our platform.
We identified the origin of the email template via the—blacked out—SAML slug (which is a unique identifier for organizations to use to connect to KMSAT). The organization has been identified. They have a training campaign called "Monthly Clicker Remedial Training" with a reminder email as shown below:
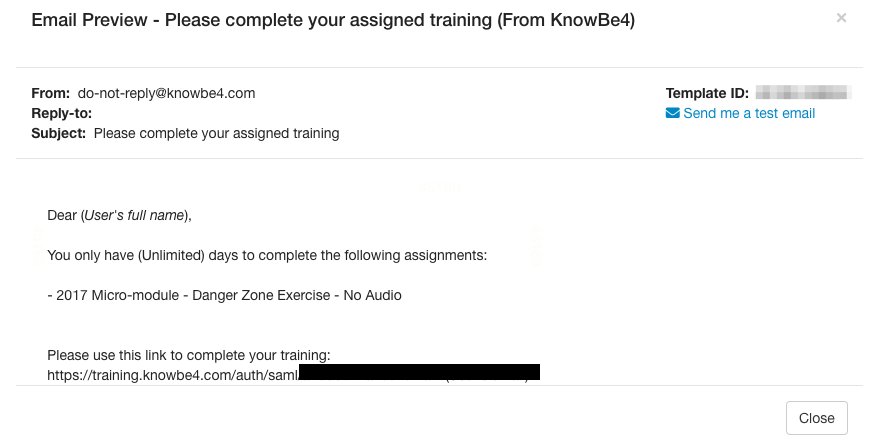
As you can see there are multiple similarities between our reminder email and the real phishing email seen in the wild. However, the course that is used in the malicious email is a course that does not exist but follows our courses format.
The malicious link used in the phishing email was determined to resolve to a compromised website hosted in Japan. This website was hosting a page mimicking an Outlook Web login page:
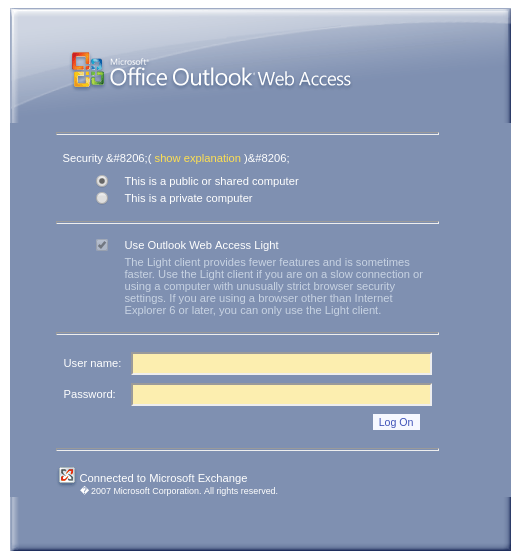
This page is no longer up since January 11th and now displays a 404 Error page. The site is also now being reported as malicious: - https://www.virustotal.com/#/url/bef4af3ecd5e6c0be282bec82f6d6a8f170301ddc1abfa4dd21f344912e99c0f/detection
A new sender and new domain were used in the same phishing campaign from the 14th to 15th:
The email campaign appeared to be sent mostly to educational institutes or government organizations. Our InfoSec team attempted to reach out to the compromised site but was unable to reach them yet.
Your InfoSec team needs to be aware of this particular threat.




