A recent password reset email from ShareFile (a Citrix company) put some users on edge, questioning both the emails legitimacy and why the reset.
Very seldom do we ever get a “please change your password” email from a cloud vendor; unless it’s in response to a data breach, most of us, at best, have seen a request to update passwords as part of a routine logon.
But last week Citrix’s Enterprise File Sync and Share (EFSS) company, ShareFile, sent out an email notice informing users a password reset was required:
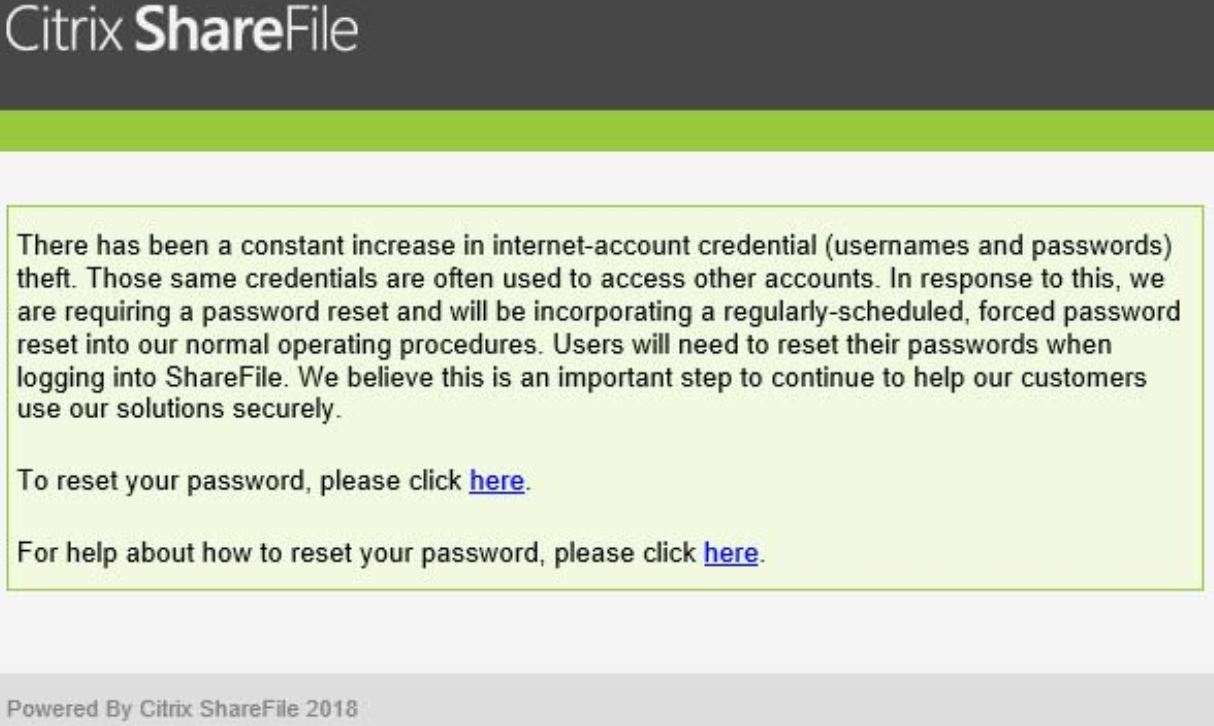
Brian Krebs, from KrebsOnSecurity contacted Citrix, asking point-blank if a data breach had occurred, and was informed one had not occurred. He was told by Citrix spokesperson, Jamie Buranich:
“This is not in response to a breach of Citrix products or services. Citrix forced password resets with the knowledge that attacks of this nature historically come in waves. Attacker’s additional efforts adapt to the results, often tuning the volume and approach of their methods. Our objective was to minimize the risk to our customers. We did not enforce a password reset on accounts that are using more stringent authentication controls. Citrix also directly integrates with common SSO solutions, which significantly reduces risk.”
However, comments from the Krebs article on this password reset email stated that even users with multi-factor authentication in place received the email.
It Feels Like a Phish, Though
The unexpected timing of the email, and the unsolicited nature of the request made many users question whether the email was indeed a phishing scam leveraging common social engineering tactics. We’ve seen scams seeking LinkedIn, eBay, and Google credentials under the guise of a “password reset”, so it’s not unreasonable for IT folks to be on edge.
The ShareFile email highlights the reality of reset scams and the necessity for organizations to protect themselves by educating users on scams that include password reset requests. Security Awareness Training elevates the security-mindedness of the employee through education on attack methods, specific scams, the use of social engineering, and appropriate response.
Which Of Your User's Passwords Are Breached?
KnowBe4’s Breached Password Test (BPT) checks to see if your users are currently using passwords that are in publicly available breaches associated with your domain. BPT checks against your Active Directory and reports compromised passwords in use right now so that you can take action immediately!
Here’s how Breached Password Test works:
- Checks to see if your company domains have been part of a data breach that included passwords
- Checks to see if any of those breached passwords are currently in use in your Active Directory
- Does not show/report on the actual passwords of accounts
- Just download the install and run it
- Results in a few minutes!
Find out now which users are using hacked passwords:
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





