A new variant of ransomware, CommonRansom, is asking for RDP access to the victim’s computer in order to decrypt files. CommonRansom is the latest attempt to extend the ransomware attack beyond the simple act of extortion. In this case, upon completing the encryption attack, the ransomware leaves a decryption note as a text file asking for both a Bitcoin ransom, as well as complete administrative RDP access to the infected endpoint.
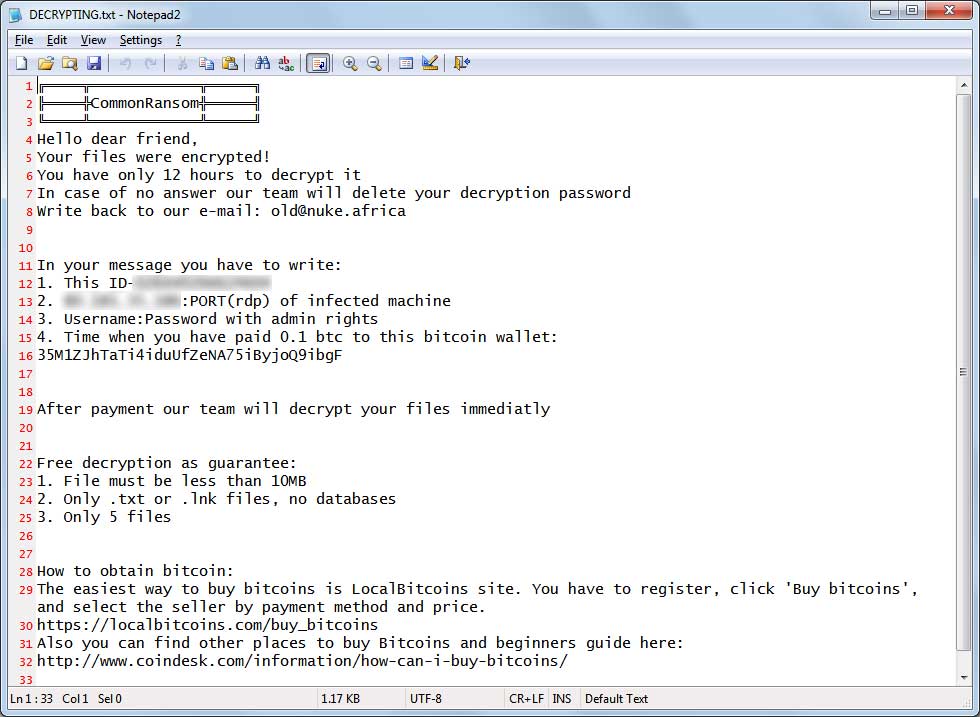
Source: ID Ransomware
I can appreciate cybercriminals wanting to evolve the ransomware attack; it’s been roughly the same tactic for a number of years. We saw another instance of extending the ransomware attack back in 2016 with Popcorn Time – where victims could decrypt their files by either paying the ransom or helping to infect two other people.
In this case, the inclusion of the RDP request is somewhat timely, as the RDP attack vector is in very high demand.
According to Positive Technologies, there’s a 2:1 ratio of demand for RDP access over the current “supply”. RDP credentials sell for as high as $100 on the Russian xDedic website, but generally go for between $3-15 on the dark web.
Given the relatively low amount of return those behind CommonRansom would get from selling RDP credentials (in comparison to their asking for the .1 BTC which, at the time of writing, is worth about $640), it’s more likely they plan on utilizing the credentials themselves, looking for a foothold within an organization, or endpoint-based data that could be of value.
So, the obvious recommendation is to NEVER provide the credentials, as attackers can steal data, further infect the endpoint, and lock everyone out of the entire machine.
While this scenario seems a bit preposterous – to think a user would give up RDP access (if they even knew how) is a bit outlandish. But, we’ve seen data suggesting users are embarrassed to let IT know they’ve become a victim, mixed with a mentality that it’s ok to share passwords with co-workers, and you may have users who think giving up RDP access is the best option.
So, what do you do about it?
- Educate Users – put them through Security Awareness Training so they never click the link, fall for the scam, open the attachment, etc. that allowed the ransomware to run in the first place!
- Backup Data – any data that’s worth protecting (which includes specific critical endpoints) should be backed up regularly.
- Block RDP – on two fronts: first, don’t allow users to have access to RDP on their endpoint. Second, don’t allow endpoint-based RDP from the Internet.
The addition of RDP into the ransomware equation may prove to be short-lived. But while it’s here, it’s important to make sure cybercriminals don’t succeed.
Brand-New Ransomware Simulator Tool Now with Cryptomining Scenario
Bad guys are constantly coming out with new malware versions to evade detection. That’s why we’ve updated our Ransomware Simulated tool “RanSim” to include a new cryptomining scenario!
This new cryptomining scenario simulates a Monero cryptocurrency-mining operation on the local machine. Monero mining is the most popular cryptocurrency mined by real-world malware and takes a lot of CPU and GPU cycles to process the data necessary to generate the currencies.
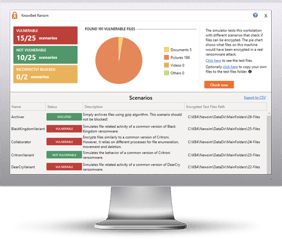
Try KnowBe4’s NEW Ransomware Simulator tool and get a quick look at the effectiveness of your existing network protection against the latest threats.
RanSim will simulate 13 ransomware infection scenarios and 1 cryptomining infection scenario to show you if a workstation is vulnerable to infection.
Here's how RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infection scenarios
- Does not use any of your own files
- Tests 14 different types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
This is a complementary tool and will take you 5 minutes max. RanSim may give you some insights about your endpoint security you never expected!
Don't like to click on redirected buttons? Copy and paste this link into your browser:
https://info.knowbe4.com/ransomware-simulator-tool-1