Your organization might just be making someone else money by allowing them to mine for cryptocurrency on your computers… and not even know it.
At the end of the day, cybercriminals simply want to generate revenue through the use of malware-based attacks. We’ve seen an abundance of ransomware, data breaches, and fraud. But in each of those cases, the infected organization is a monetary victim – causing organization like yours to be on the lookout for attacks like these, and to have a response plan. Also, in each of these attack models, there’s quite a bit of work attackers need to do to “earn” their money.
But with the advent of cryptocurrency, and an ability to convert it into liquid cash, cybercriminals have taken a new route to generate their criminal revenue – cryptomining.
Cybercriminals Take to Cryptomining
Cryptomining is the process of solving complex problems to verify digital transactions using computer hardware. Miners are paid in cryptocurrency, but require a large amount of processing power to generate a material amount of money – a single machine only generates around $12/day. And if the mining can be run on an unsuspecting endpoint, that’s “free” processing power to the cybercriminal!
There are a few reasons cryptojacking is so interesting to criminal organizations:
- It’s lucrative – If a cybercriminal organization can infect, say, 1000 machines each day, do the math: it adds up to quite a lot of revenue over time.
- It’s tough to detect – while some cryptomining occurs on an endpoint as a separate process (that can be detected), cybercriminals have some sneaky ways to avoid detection. Some use a browser plug-in (so the process is your browser and closing a tab eliminates all the evidence), and others use PowerShell to inject malware coed into known-good existing processes.
- It’s tough to get caught – Miners are paid in the cryptocurrency they help to mine, so there’s no communication with the victim organization to identify the miner. Plus the mining traffic generated doesn’t necessarily provide any identifying detail (e.g. IP address) of the cyberciminal organization responsible.
How Does Cryptojacking Work?
Keep in mind that cryptomining is just the means to a financial end for the cybercriminal. And, just like ransomware, remote access trojans (RATs), and other types of malware, the cybercriminal needs to somehow infect a machine. The difference with cryptomining is that the monetary value is found in infecting large numbers of endpoints. They’ll be happy to take the single infected machine, but they really want hundreds of them instead. To accomplish this, they use traditional methods, with a focus on attaining those large numbers of victims:
- Drive-by downloads – Heavily trafficked websites (such as the recent attack on government websites in India) are compromised by cybercriminals, inserting code that will attempt to download cryptomining malware to website visitors. In the case of the Indian government website, over 1.6M visitors a month made it a prime target for an easy payoff.
- Phishing attacks – Cybercriminals would rather use a shotgun approach to his as many targets as possible. So, the use of phishing attacks designed to capture the attention of as many people as possible, on as many devices as possible, is the focus.
Once infected, there are only a few symptoms that your organization has become a victim of cyrptojacking:
- Increased network traffic – This isn’t meant to be taken as “massive amounts of traffic”, but certainly more traffic than the endpoint normally generates.
- Slower endpoint performance – This is probably the most telling sign, as mining is a processor-intensive exercise.
Keeping from Becoming a Cryptojacking Victim
When it all boils down, cryptojacking is stealing your power, your bandwidth, and your employee’s productivity. To avoid this there are a few things you can do:
- Prevent – There are a number of things you can do to prevent your organization from becoming a cryptojacking victim. The first is to educate your users via security awareness training about social engineering tactics, attack methods, and what to be on the lookout for. This will help elevate their sense of security and lower the possibility of them falling for malicious attacks. More specific to just cryptojacking is the use of ad blocking software or anti-cryptomining browser extenstions. These solutions will help to eliminate the browser-based attacks.
- Detect – The use of Antivirus and Endpoint Protection solutions still plays a valuable role in detecting cryptomining code. Should an attacker use a custom piece of malware, AV solutions can spot it as unusual. Those attacks leveraging code injection into memory can still be spotted via EP solutions. I should note, none of this is foolproof – attackers spend quite a lot of time testing their wares against security solutions, looking for ways to avoid detection. I also should mention that detection by inspecting network traffic for unusual patterns can also be used to spot cryptomining.
- Respond – Having an ability to remove malware from endpoints and close off unwanted network traffic should be a part of your overall planning around this kind of attack.
Cryptojacking Isn’t Going Anywhere
This form of attack is relatively new and is trending. The lure of utilizing lots of victim endpoints without them knowing (which translates to “without getting caught”) is very appealing to cybercriminals. If you have any kind of security strategy around malware and ransomware, you need to be adding cryptojacking to the list and act accordingly; you’ll be seeing a lot more of this attack vector.
Brand-New Ransomware Simulator Tool Now with Cryptomining Scenario
Bad guys are constantly coming out with new malware versions to evade detection. That’s why we’ve updated our Ransomware Simulated tool “RanSim” to include a new cryptomining scenario!
This new cryptomining scenario simulates a Monero cryptocurrency-mining operation on the local machine. Monero mining is the most popular cryptocurrency mined by real-world malware and takes a lot of CPU and GPU cycles to process the data necessary to generate the currencies.
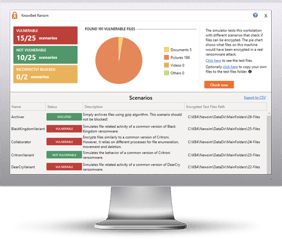
Try KnowBe4’s NEW Ransomware Simulator tool and get a quick look at the effectiveness of your existing network protection against the latest threats.
RanSim will simulate 13 ransomware infection scenarios and 1 cryptomining infection scenario to show you if a workstation is vulnerable to infection.
Here's how RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infection scenarios
- Does not use any of your own files
- Tests 14 different types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
This is a complementary tool and will take you 5 minutes max. RanSim may give you some insights about your endpoint security you never expected!
Download the new Ransim here:
https://info.knowbe4.com/ransomware-simulator-tool-1