Nearly 30,000 people came to Las Vegas last week for the 26th edition of DEF CON, the iconic security conference. And no small amount of the mental energy of that vast crowd was spent on one particular thing: the conference badge.
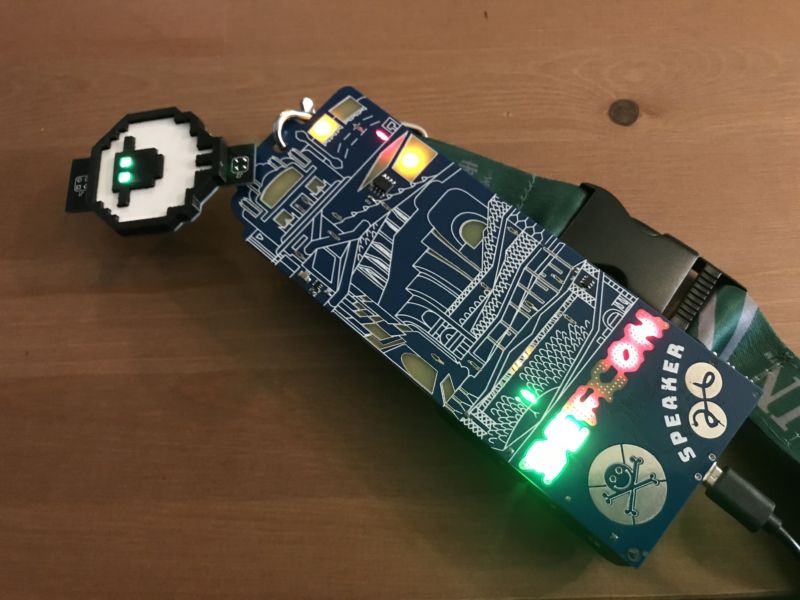
This year's badges, designed by Tymkrs, were elevated works of printed circuit board art with a collection of LED-lit features, including red and green human figures and a color-shifting DEF CON logo. But it quickly becomes apparent that there was a lot more going on here than just blinking lights.
DEF CON alternates year to year between electronic, hackable badges and non-electronic ones; last year's badges were a throwback design intended to celebrate the conference's 25th anniversary. But every year, the badges include some sort of clue to a cryptographic challenge—three years ago, the badge was an actual vinyl record that required attendees to find a turntable to hear the puzzle clue.
DEF CON's theme this year was "1983," and the Tymkrs badge itself is, among other things, a gaming platform that evokes 1980s text-based adventures and handheld button-mashers. It's also a hardware hacking challenge. And as is common with these sorts of things, it's also extendable with add-on hardware—I picked up a cheap cosmetic add-on near the Packet Hacking Village built by KL34N of the DC801 crew ("Sh*ttty add ons for $5! Get your sh*ttty ad-ons!") outside the Wall of Sheep's Packet Hacking Village.
One of the most ingenious aspects of the badge this year is that it forced those who wanted to solve the puzzle to connect—literally. The only way to unlock parts of the badge's code is to dock with at least one of all the eight types of badges issued, each with its own theme: "Human" (general attendee), "Goon" (volunteer), speaker, press, contest staff, artist, vendor, and Call for Papers board member.
Then there's the game that lurks within the badge. By plugging a USB-C cable into the badge and connecting it to a computer, attendees were able to access a game screen in a character-based terminal—either by using a terminal application such as PuTTY on Windows or using Linux or MacOS command line tools such as screen. The DEF CON logo at the bottom of the badge doubles as a directional controller, and the "26" on the badge is action controls.
-
Some of the screens of the mini-game on the Speaker badge for DEF CON 26.
-
-
-
-
-
Each version of the badge had its own story line, based on the badge's theme. The Human badge had a garage theme, for example, and the Goon badge had a prison theme. My speaker badge's game took place in a theater complex, while press badges had a transmission-station motif. But all the games included hexadecimal-encoded clues and were based on the same hardware. The first, on my speaker badge:
Belly of the complex. You can feel the beat as the band performs. *wub wub* Sing it!
0x2BFC8E2B3561C04FBBC73FA43D5D96540D0AA008B30924CE47DA0EC67530D3
It's too dark to see anything. A lot of autographs on the walls here though!
Completing the game requires more than just button mashing. Some clues in the mini-game hinted at required hardware hacks, including flipping a component on the board. Would-be badge hackers turned to Reddit's DEF CON subreddit and a "hackthebadge" Slack channel, sharing hardware hacking discoveries. All the text strings from the game have been dumped and shared as well, along with details on some of the components—one of which is a magnetic switch that unlocks access to an area within the game.
As of the end of DEF CON, it doesn't appear that anyone had yet solved the badge puzzle. A firmware bug that requires re-flashing of the firmware to complete the mini-game had something to do with that. But thanks to a badge emulator project posted on GitHub—which can provide the docking codes from all the issued badges—and other continued work by badge hackers, the game will continue well after everyone's Las Vegas hangovers have faded. Additional clues are being revealed by Tymkrs in a Reddit AMA on the badge, which launched yesterday.
reader comments
41