
New hope glimmered on Friday for people hit by last week's virulent ransomware worm after researchers showed that a broader range of PCs infected by WCry can be unlocked without owners making the $300 to $600 payment demand.
A new publicly available tool is able to decrypt infected PCs running Windows XP and 7, and 2003, and one of the researchers behind the decryptor said it likely works for other Windows versions, including Vista, Server 2008, and 2008 R2. The tool, known as wanakiwi, builds off a key discovery implemented in a different tool released Thursday. Dubbed Wannakey, the previous tool provided the means to extract key material from infected Windows XP PCs but required a separate app to transform those bits into the secret key required to decrypt files.Matt Suiche, cofounder of security firm Comae Technologies, helped develop and test wanakiwi and reports that it works. Europol the European Union's law-enforcement agency, has also validated the tool. Suiche has published technical details here, and provided the following screenshot of the tool in action:
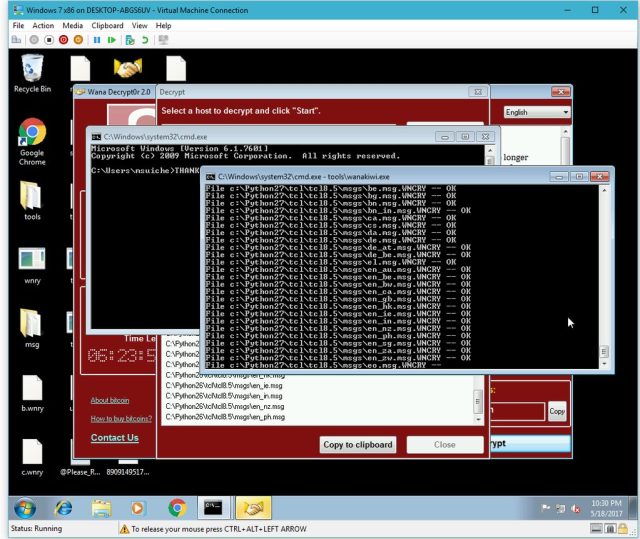
Like Wannakey, wanakiwi takes advantage of shortcomings in the Microsoft Cryptographic Application Programming Interface that WCry and other Windows applications use to generate keys for encrypting and decrypting files. While the interface includes functions for erasing a key from computer memory once it has been secured, previously overlooked limitations sometimes allow the prime numbers used to create a key to remain intact in computer memory. Those numbers can then be recovered as long as PCs remain powered on and the memory location storing the numbers isn't overwritten with new data.
Wanakiwi is able to successfully scour the memory of infected XP and 7 machines, extract the p and q variables that the secret key was based on, and reassemble the finished key. The tool then uses the key to decrypt all files locked by the WCry ransomware.
Benjamin Delpy, one of the developers of wanakiwi, told Ars he replicated the machine state of PCs infected by last week's WCry worm that attacked more than 200,000 machines in 150 countries. He said his tool has successfully decrypted several such PCs, some that run Windows 2003 and 7. He said he presumes other infected versions can be similarly recovered. Wanakiwi provides additional improvements over Wannakey, including a point-and-click interface and the ability to generate the full decryption key without the need for other tools.Infected PC owners "just download wanakiwi, and if the key can be constructed again, it extracts it, reconstructs it (a good one), and starts decryption of all files on the disk," he said in an interview. "In bonus, the key I obtain can be used with the malware decryptor to make it decrypt files like if you paid :)."
As was the case with Wannakey, the recovery won't work if an infected computer has been restarted. And even when an infected PC has remained powered on, the decryptor may not work if the memory location that stored the key material has been overwritten. Wanakiwi has not yet been extensively tested on computers with x64 CPUs, so it's possible the tool doesn't work as reliably on that platform. Despite the limitations, wanakiwi represents a major breakthrough that could provide invaluable relief for tens of thousands of people around the world.
"In lots of cases, the key cannot be recovered," Delpy said. Victims "need a good amount of luck!"
reader comments
51