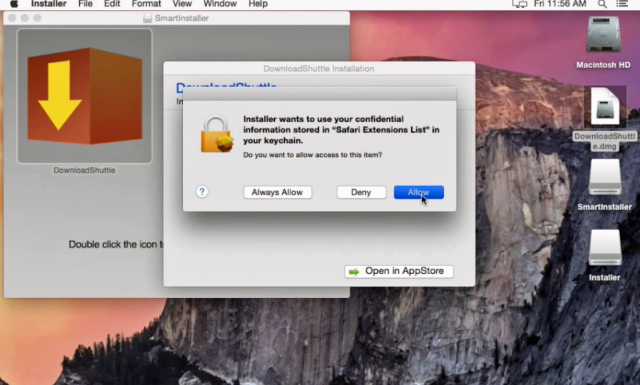
Last month, Ars chronicled a Mac app that brazenly exploited a then unpatched OS X vulnerability so the app could install itself without requiring people to enter system passwords. Now, researchers have found the same highly questionable installer is accessing people's Mac keychain without permission.
The adware taking these liberties is distributed by Israel-based Genieo Innovation, a company that's long been known to push adware and other unwanted apps. According to researchers at Malwarebytes, the Genieo installer automatically accesses a list of Safari extensions that, for reasons that aren't entirely clear, is stashed inside the Mac Keychain alongside passwords for iCloud, Gmail, and other important accounts.Genieo acquires this access by very briefly displaying a message asking for permission to open the Safari extensions and then automatically clicking the accompanying OK button before a user has time to respond or possibly even notice what's taking place. With that, Genieo installs an extension known as Leperdvil. The following three-second video captures the entire thing:
"What they're basically doing is using provided system calls to get the location of the [permission] window and the location of the OK button in the window," Thomas Reed, Malwarebytes' director of Mac offerings, told Ars. "Then they're simulating a mouse click. I'm surprised nobody thought of that before."
The behavior the Genieo installer is exploiting isn't technically what researchers consider a vulnerability. Rather, it's likely Apple developers make the mapping and auto clicking possible to assist users with visual impairments and other disabilities. What's more, the threat posed by Genieo is offset by the fact that the extensions list is only accessed after an end user has downloaded the app, clicked on it, and entered a system password.
Still, asking for permission and then auto clicking the OK button is a sneaky move, one that only reinforces the distrust many people have for Genieo. Reed said that Malwarebytes researcher Adam Thomas has found the same sneaky code littered throughout Genieo applications. Thomas has yet to analyze these other instances to see if they open assets other than the extensions list, but he hasn't ruled it out. It's also unclear why Genieo uses the keychain dialog at all, since the company's installers have been able to install Safari extensions through other means for years. Malwarebytes researchers speculate it may have something to do with changes anticipated in El Capitan, the next major version of OS X.
The discovery also underscores a potential weakness that could be exploited by other unwanted adware or, worse, by outright malicious espionage trojans. For instance, it's not hard to imagine a trojan disguised as a benign program that remains dormant for some period of time. Then, when the machine isn't in active use, the app asks for permission to access a password for iCloud or Gmail and in the blink of the eye approves the request. Unless end users have overridden default Mac settings, the app would now be in possession of the credentials.
"I would argue that that particular alert probably should not have its contents exposed so you can find it and click it," Reed said. "Something needs to be locked down there so it can't just be done by anybody."

reader comments
106